17 Open-source Free System Auditing Tools for macOS, Windows, Linux, and the Cloud
System auditing is the process of collecting and analyzing information about a computer's use, events, and security. This information can be used to detect and prevent security breaches, troubleshoot problems, and ensure compliance with regulations and policies.
System auditing is important because it provides visibility into what is happening on a computer system. Without auditing, it is difficult to detect and respond to security threats and other issues.
System auditing is primarily used by organizations that need to ensure the security and reliability of their computer systems. This includes government agencies, financial institutions, and healthcare organizations.
There are several advantages to using free open-source auditing systems, including:
- Cost: Open-source software is typically free to use, which can be a significant cost savings for organizations.
- Customizability: Open-source software can be modified to meet specific needs, which can be especially important for organizations with unique requirements.
- Transparency: Because the source code is available, open-source software is often considered more transparent and trustworthy than proprietary software.
In this post, we offer you the best open-source free auditing solutions that you can use for free. However, some of these tools requires experiances to run install, configure and run.
1- OS X Auditor
OS X Auditor is a free Mac OS X computer forensics tool.
OS X Auditor parses and hashes the following artifacts on the running system or a copy of a system you want to analyze:
- the kernel extensions
- the system agents and daemons
- the third party's agents and daemons
- the old and deprecated system and third party's startup items
- the users' agents
- the users' downloaded files
- the installed applications
It extracts:
- the users' quarantined files
- the users' Safari history, downloads, topsites, LastSession, HTML5 databases and localstore
- the users' Firefox cookies, downloads, formhistory, permissions, places and signons
- the users' Chrome history and archives history, cookies, login data, top sites, web data, HTML5 databases and local storage
- the users' social and email accounts
- the WiFi access points the audited system has been connected to (and tries to geolocate them)
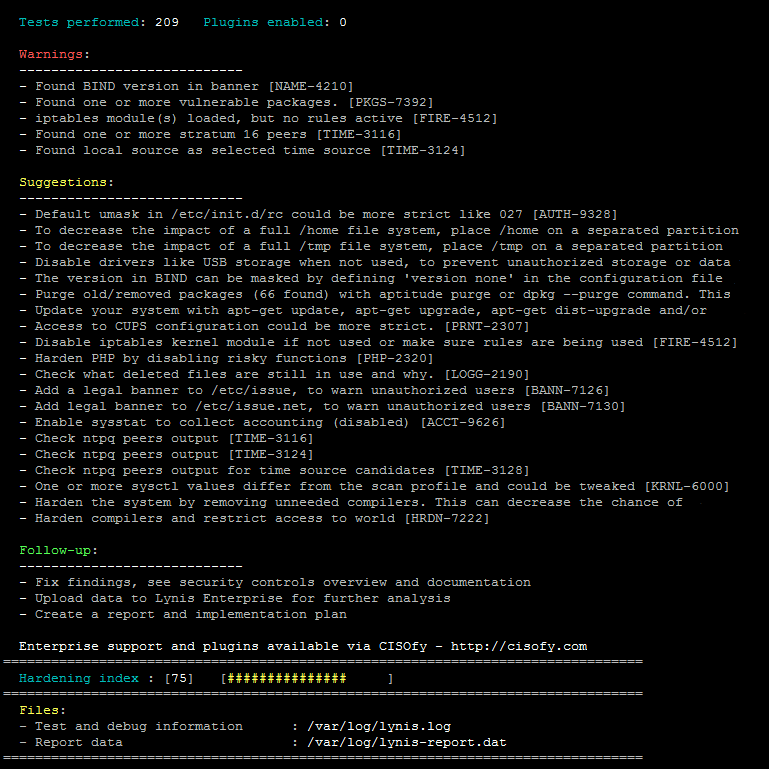
2- Lynis (macOS and Unix auditing)
Lynis is a security auditing tool for systems based on UNIX like Linux, macOS, BSD, and others. It performs an in-depth security scan and runs on the system itself. The primary goal is to test security defenses and provide tips for further system hardening.
It will also scan for general system information, vulnerable software packages, and possible configuration issues. Lynis was commonly used by system administrators and auditors to assess the security defenses of their systems. Besides the "blue team," nowadays penetration testers also have Lynis in their toolkit.
Typical users of the software:
- System administrators
- Auditors
- Security officers
- Penetration testers
- Security professionals
3- Mergen - macOS Audit and Security Check Tool
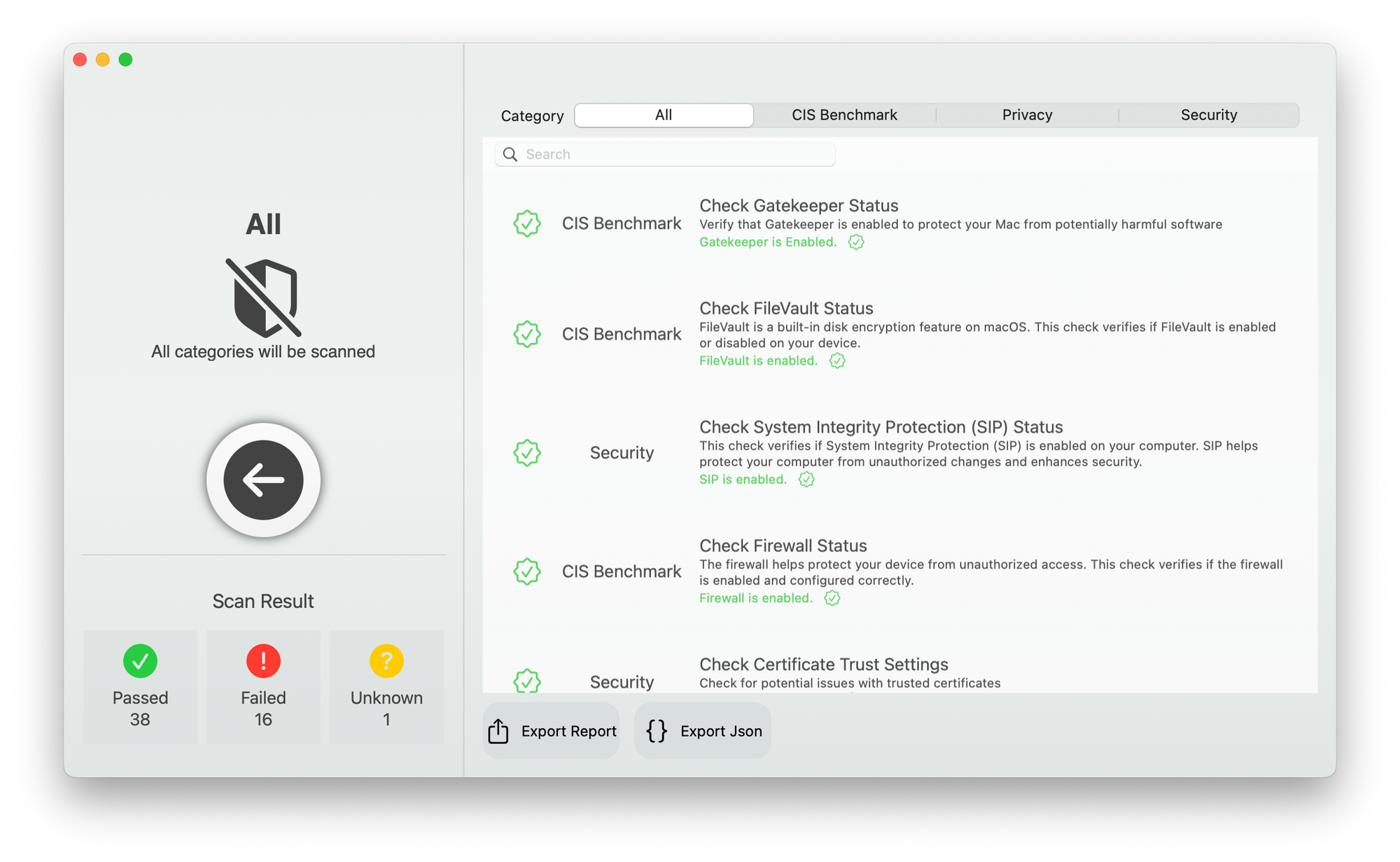
Mergen is an open-source, native macOS application for auditing and checking the security of your Mac. It scans your system for security issues based in the Center for Internet Security (CIS) Benchmark, and checks various settings and configurations related to security and privacy.
Mergen provides a comprehensive list of features to help secure Mac devices, including checking Gatekeeper and Secure Kernel Extension Loading status, disabling various sharing options, enabling automatic updates and security responses, and checking various settings related to time, location, and auditing.
4- Knox (macOS)
A set of Tools to repurpose system auditing for non-security uses. Allows observability and introspection into processes and their lifecycle, granular file access, causes or sources of errors, info about networking use, and more. Based on macOS system auditing API "Basic Security Module" (aka BSM).
5- System Audit Script
A bash script that performs a quick system audit, outputs results to a file, and displays machine type, IP, hostname, DNS, memory, CPU, SUID files, and top 10 processes. The script will not run as root and will exit if executed as root.
6- Scout Suite (Cloud Auditing)
Scout Suite is an open source multi-cloud security-auditing tool, which enables security posture assessment of cloud environments. Using the APIs exposed by cloud providers, Scout Suite gathers configuration data for manual inspection and highlights risk areas. Rather than going through dozens of pages on the web consoles, Scout Suite presents a clear view of the attack surface automatically.
Scout Suite was designed by security consultants/auditors. It is meant to provide a point-in-time security-oriented view of the cloud account it was run in. Once the data has been gathered, all usage may be performed offline.
7- django-auditlog
django-auditlog (Auditlog) is a reusable app for Django that makes logging object changes a breeze. Auditlog tries to use as much as Python and Django's built in functionality to keep the list of dependencies as short as possible. Also, Auditlog aims to be fast and simple to use.
Auditlog is created out of the need for a simple Django app that logs changes to models along with the user who made the changes (later referred to as actor). Existing solutions seemed to offer a type of version control, which was found excessive and expensive in terms of database storage and performance.
The core idea of Auditlog is similar to the log from Django's admin. Unlike the log from Django's admin (django.contrib.admin) Auditlog is much more flexible. Also, Auditlog saves a summary of the changes in JSON format, so changes can be tracked easily.
8- Audited
Audited (previously acts_as_audited) is an ORM extension that logs all changes to your models. Audited can also record who made those changes, save comments and associate models related to the changes.
9- Laravel auditing (PHP)
This package will help you understand changes in your Eloquent models, by providing information about possible discrepancies and anomalies that could indicate business concerns or suspect activities.
Laravel Auditing allows you to keep a history of model changes by simply using a trait. Retrieving the audited data is straightforward, making it possible to display it in various ways.
10- SSH Auditor
ssh-auditor will automatically:
- Re-check all known hosts as new credentials are added. It will only check the new credentials.
- Queue a full credential scan on any new host discovered.
- Queue a full credential scan on any known host whose ssh version or key fingerprint changes.
- Attempt command execution as well as attempt to tunnel a TCP connection.
- Re-check each credential using a per credential
scan_interval- default 14 days.
11- twa (Web)
A tiny web auditor with strong opinions.
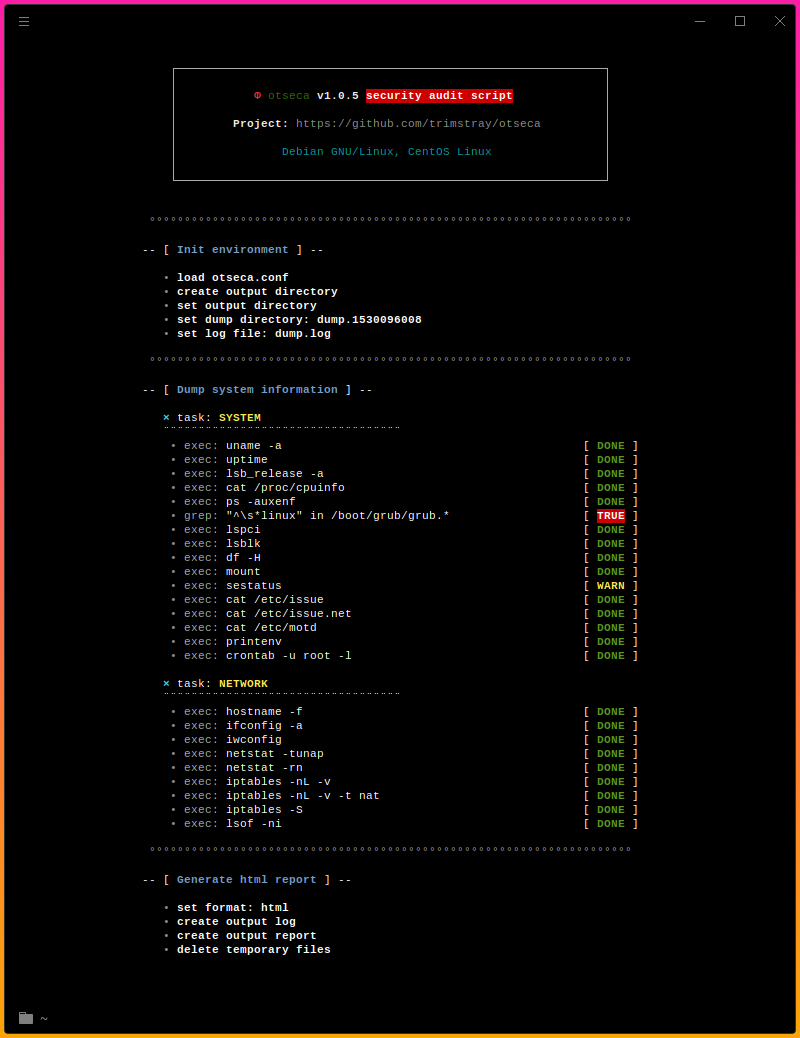
12- Otseca

Open source security auditing tool to search and dump system configuration. It allows you to generate reports in HTML or RAW-HTML formats.
It is an ideal solution for:
- System admins
- Security researchers
- Security professionals
- Pentesters
- Hackers
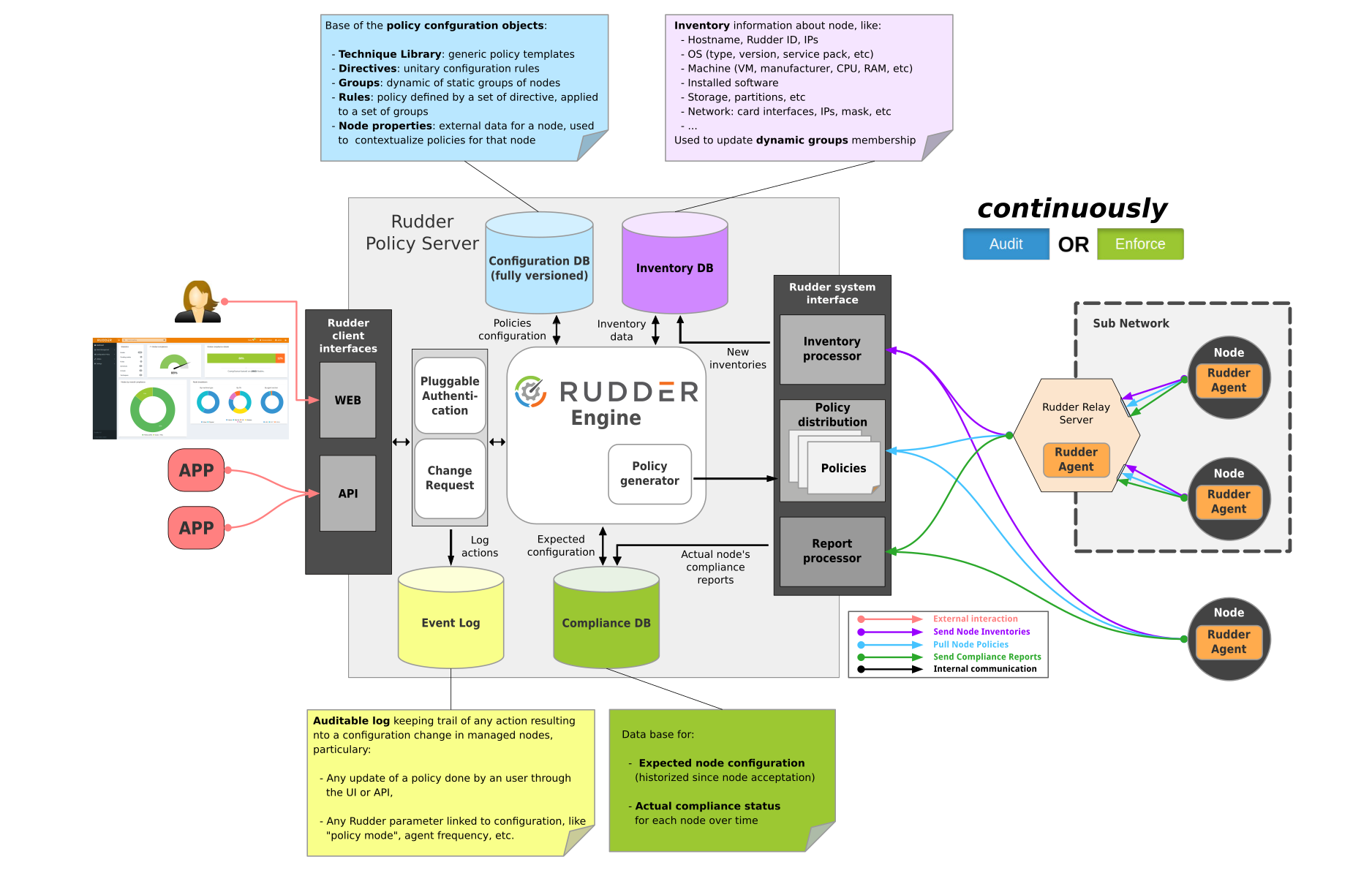
13- Rudder
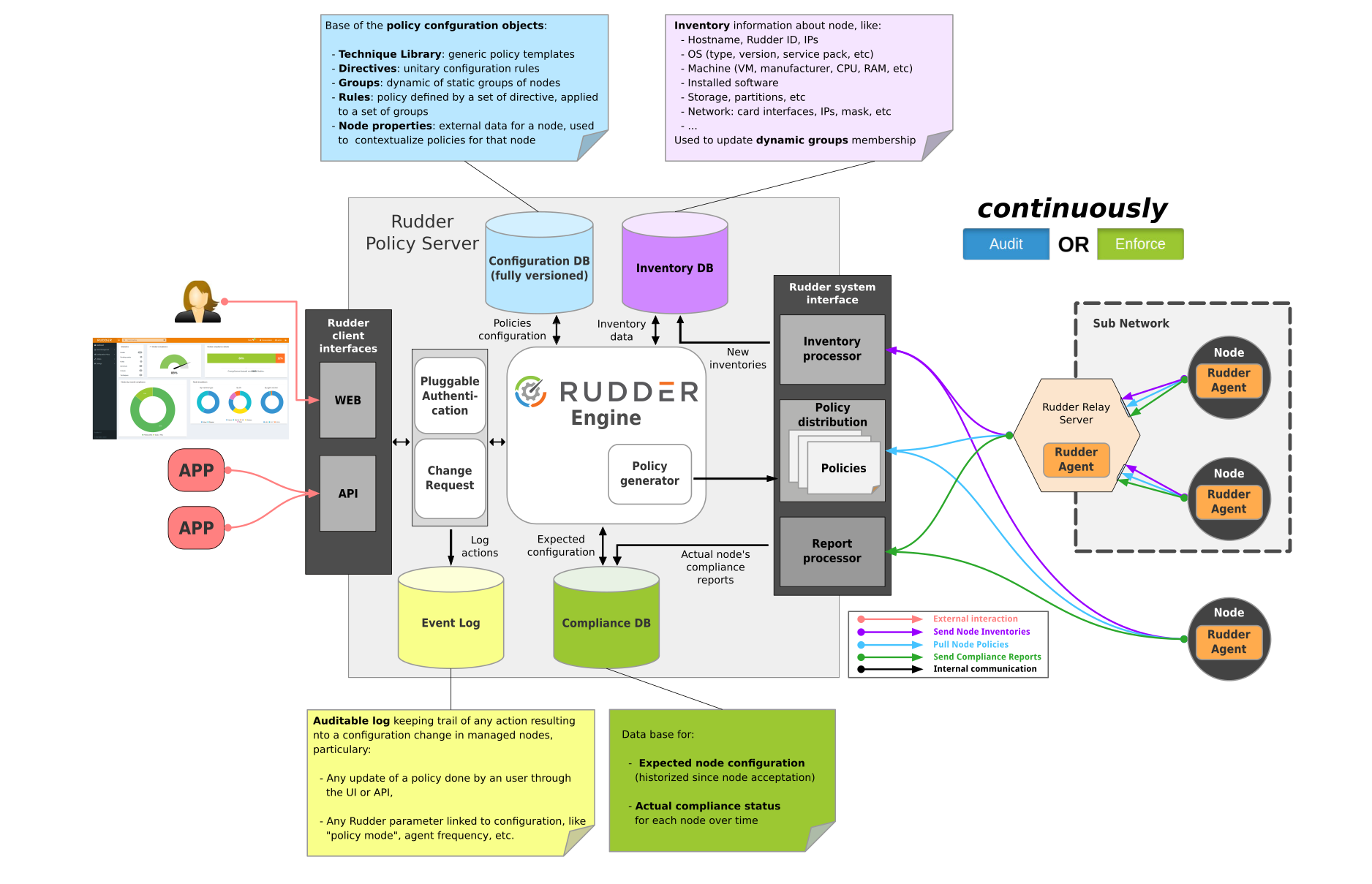
Rudder is an easy to use, web-driven, role-based solution for IT Infrastructure Automation & Compliance.
Rudder is made of several components:
- A central server (written in Scala) that defines the configurations to apply and collects application reports, with a focus on continuously checking configurations and centralising real-time status data. A graphical builder lowers the technical level required to define policies. Each policy can be independently set to be automatically checked or enforced on a policy or host level.
- Agents installed on the managed nodes. As they are very lightweight (10 to 20 MB of RAM at peak) and blazingly fast (they are written in C and takes less than 10 seconds to verify 100 rules), they run on almost every kind of device, so you’ll be managing physical and virtual servers in the data center, cloud instances, and embedded IoT devices in the same way. Installation is self-contained, via a single package, and can auto-update to limit agent management burden.
- Relay servers (optional) that allows managing nodes in different networks, or on different site through a single entry point.
- Rudder is designed for critical environments where a security breach can mean more than a blip in the sales stats. Built-in features include change requests, audit logs, and strong authentication.
The workflow offers different users options at their own level:
- Non-expert users can define parameters in a central interface, and Rudder will automatically make sure that your IT services are installed, configured, running and in good health. All actions (checks, warnings, fixed errors…) are reported upon immediately in the user interface, keeping drift from nominal behaviour low.
- Expert users can configure how to implement these parameters on different systems, or build upon the pre-defined library provided using the CLI or API.
- Managers can consult compliance reports and access audit logs.
Rudder is an established project with several tens of thousands of managed nodes, in companies from small to biggest-in-their-field. Typical deployments manage 100s to 1000s of nodes. The biggest known deployments are about 10k nodes on a single Rudder server.
14- Hardlog: Practical Tamper-Proof System Auditing Using a Novel Audit Device
Prototype source code for the Hardlog research paper, presented at IEEE S&P (Oakland) 2022. If you find this repository useful, please cite our paper/repository.
Hardlog requires two machines---audit device and host---connected through a USB-3.0 interface. While there are numerous machine configurations that should work, we provide below the specifications for machines that we tested with.
Audit Device
We used a RockPro64 development board, equipped with an RK3399 ARM CPU. The board came with 2 GB of main memory. We attached a 250 GB SSD (tested with WD SN550 and Samsung 950 Pro) using its PCIe interface. On the software side, the board was running Armbian 21.05 (Buster) with Linux v4.4.213. The details about building the correct software toolchain (including OS) is provided below.
Host
The host machine came with an Intel (c) Core i7-8700 x86 CPU with 16 GB of DDR4 memory. The host machine had a 512 GB SSD (Samsung 970 Pro), connected through PCIe 3. On the software side, the machine ran Elementary OS Hera 5.1.7 with Linux v5.4.97. We also partly tested with a vanilla Ubuntu 20.04 OS.
15- go-audit
go-audit is an alternative to the auditd daemon that ships with many distros. After having created an auditd audisp plugin to convert audit logs to json, I became interested in creating a replacement for the existing daemon.
Goals
- Safe : Written in a modern language that is type safe and performant
- Fast : Never ever ever ever block if we can avoid it
- Outputs json : Yay
- Pluggable pipelines : Can write to syslog, local file, Graylog2 or stdout. Additional outputs are easily written.
- Connects to the linux kernel via netlink (info here and here)
16- Lunar Lockdown UNix Auditing and Reporting
This scripts generates a scored audit report of a Unix host's security. It is based on the CIS and other frameworks. Where possible there are references to the CIS and other benchmarks in the code documentation.
Why a shell script? I wanted a tool that was able to run on locked down systems where other tools may not be available. I also wanted a tool that ran on all versions of UNIX. Having said that there are some differences between sh and bash, so I've used functions only from sh.
There is no warranty implied or given with this script. My recommendation is to use this script in audit mode only, and address each warning individually via policy, documentation and configuration management.
I am by no means a coder, so there are bound to be bugs and better ways to approach things in this script, so a sincere thank you to the people who have provided feedback, updates and patches to fix bugs/features in code.
Supported systems:
- Linux: RHL, CentOS, Sceintfic Linux, SLES, Debian, Ubuntu, Amazon Linux,
- Solaris
- macOS
- FreeBSD
- AIX
- ESXi
Windows support would require the installation of additional software, so I haven't looked into it. Having said that, Windows support may come in the future via bash.
Supported services:
- AWS
- Docker
- Kubernetes (not complete)
- Apache (not complete)
17- Prowler
Prowler is an Open Source security tool to perform AWS, GCP and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness.
It contains hundreds of controls covering CIS, NIST 800, NIST CSF, CISA, RBI, FedRAMP, PCI-DSS, GDPR, HIPAA, FFIEC, SOC2, GXP, AWS Well-Architected Framework Security Pillar, AWS Foundational Technical Review (FTR), ENS (Spanish National Security Scheme) and your custom security frameworks.
Prowler is licensed as Apache License 2.0 as specified in each file.


