18 Open-source DDoS Distributed Denial Of Service Tools for Pentesting Hackers, Penetration Tester and CyberSecurity
Table of Content
What is a DDoS (Distributed Denial of Service) attack?
A DDoS (Distributed Denial of Service) attack is a malicious attempt to disrupt the regular functioning of a network, service, or website by overwhelming it with a flood of internet traffic. This flood of traffic is generated by multiple compromised devices, forming a botnet.
What are DDoS attack testing tools?
DDoS attack testing tools are used to simulate and assess the resilience of a network or system against DDoS attacks. These tools help organizations identify vulnerabilities and weaknesses in their infrastructure, allowing them to implement appropriate mitigation measures.
What is a Distributed DoS (DDoS) attack?
A Distributed DoS (DDoS) attack is a type of DDoS attack where the attack traffic is generated from multiple sources, making it more difficult to block or mitigate. In a distributed attack, the traffic comes from a botnet consisting of multiple compromised devices, often spread across different geographical locations.
1- MHDDoS
This is an amazing DDoS attack script that supports 56 methods of hacking and DDoS attack. It also comes with powerful tools and recon features.
It provides various methods for Layer 7 and Layer 4 attacks, including GET and POST floods, OVH and CloudFlare bypasses, slowloris attacks, and amplification attacks using protocols like Memcached and DNS. The document also mentions additional tools for finding real IP addresses, checking website status, and performing network diagnostics.
Other Features
- CHAR | Chargen Amplification
- DNS | DNS Amplification
- MCPE | Minecraft PE Status Ping Protocol
- MINECRAFT | Minecraft Status Ping Protocol
- MCBOT | Minecraft Bot Attack
- NTP | NTP Amplification
- MEM | Memcached Amplification
- FIVEM | Send FiveM Status Ping Protocol
- TS3 | Send Teamspeak 3 Status Ping Protocol
- VSE | Send Valve Source Engine Protocol
- XMLRPC | WP XMLRPC exploit (add /xmlrpc.php)
- MCBOT | Minecraft Bot Attack
2- AllHackingTools
AllHackingTools is a system that automates the download and installation of various penetration testing tools.
It offers a wide range of hacking tools, including those for information gathering, exploitation, sniffing and spoofing, web attacks, and more. It also includes tools for DDoS attacks, phishing attacks, and hash cracking, among others.
3- DDoS-Ripper
DDos Ripper is an exceptionally powerful and efficient Distributed Denied-of-Service (DDOS) attack server that effectively incapacitates targets or surrounding infrastructure by overwhelming them with a massive influx of Internet traffic.
4- DDoS Attack
This is a free and open-source Python script for online DDos-Attack.
5- Hulk 3
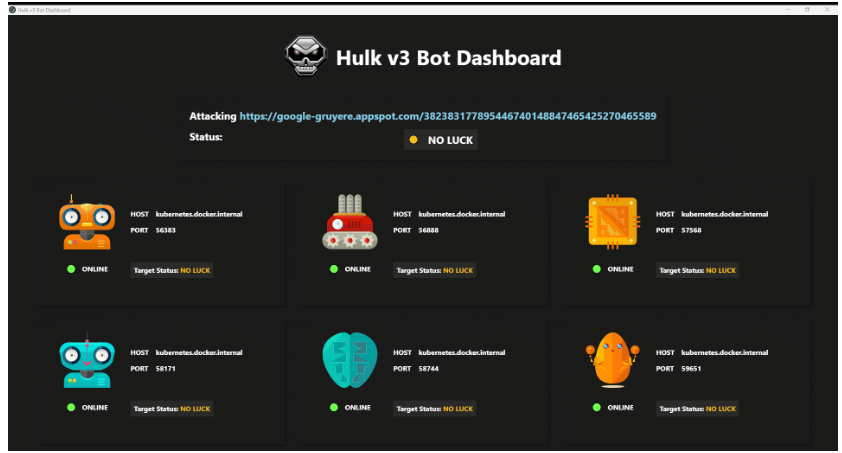
HULK-v3 is a Distributed Denial of Service (DDoS) tool that is designed to put a heavy load on HTTPS servers. Its purpose is to exhaust the resource pool of the targeted servers, potentially causing them to become overwhelmed and unresponsive.
It is important to note that Hulk is meant for educational and research purposes only, and any malicious usage of this tool is strictly prohibited. The authors of Hulk cannot be held responsible for any consequences resulting from the usage of this tool.
6- CC-attak
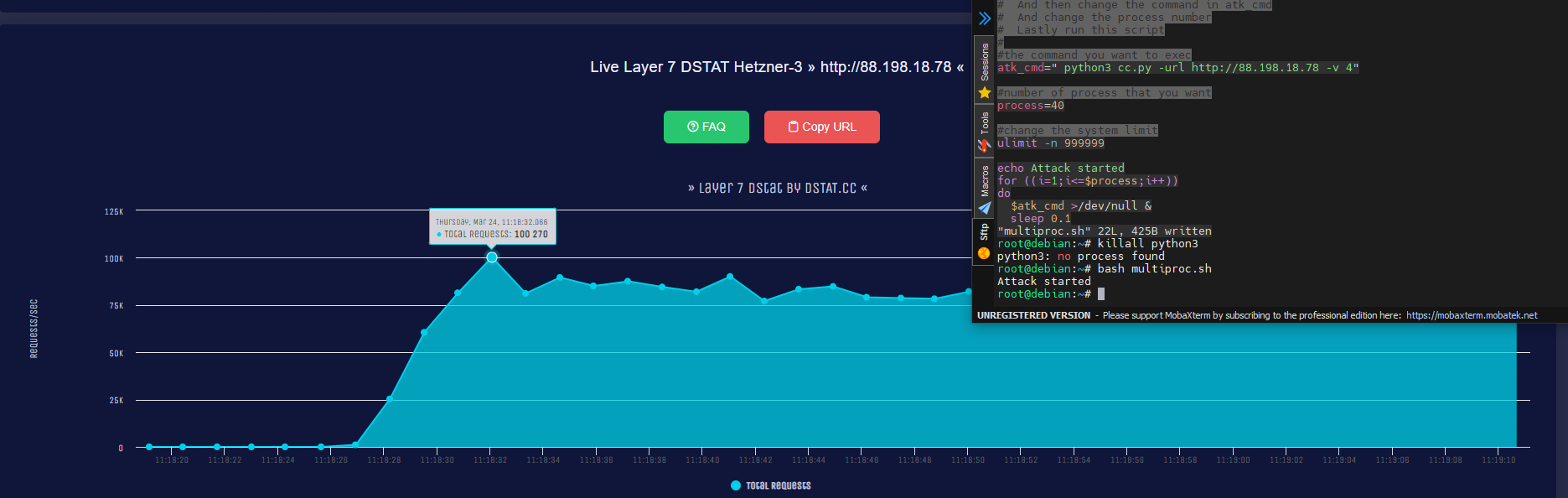
CC-attack is a python script that uses socks4/5 or http proxies to launch DDoS attacks on http(s) servers. It supports HTTP proxies, has options for human-like behavior, and allows customization of cookies and post data. It also supports HTTPS and socks4/5 proxies.
7- Raven Storm
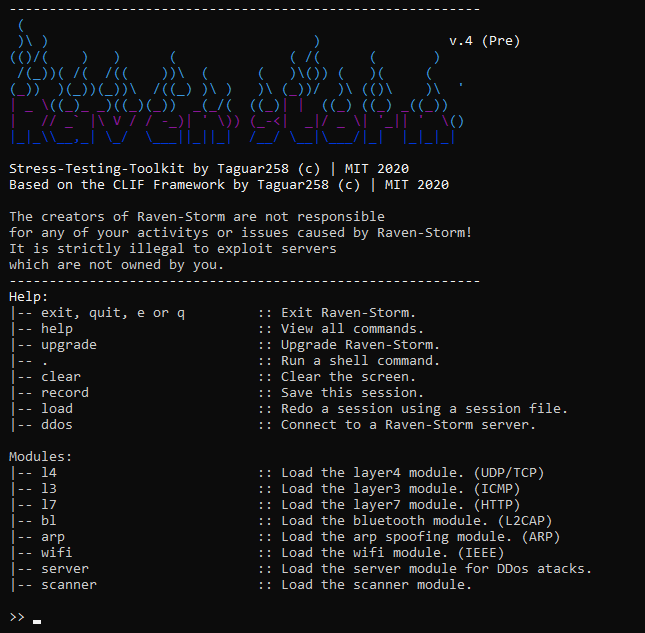
Raven-Storm is a powerful DDoS toolkit for penetration tests, capable of attacking various protocols. It can target WiFi access points, devices in networks, servers, services, and Bluetooth devices. Raven is designed to help with stress-testing attacks and can handle strong servers and non-typical targets. The repository is currently archived and not being actively worked on.
Key Features
- Raven-Storm includes tools for creating shorcuts and working more efficiently.
- Raven is Effective and powerful in shutting down hosts and servers.
- Testing and understanding are the goals of Raven-Storm.
- Raven lets you connects clients together to create a botnet.
- Features different protocols such as UDP/TCP, ICMP, HTTP, L2CAP, ARP and IEEE.
8- Karma DDoS
This open-source free DDoS script comes with multiple bypass capabilities, including bypassing Cloudflare UAM, CAPTCHA, BFM, NOSEC, DDoS Guard, Google Shield, V Shield, and Amazon, among others.
It offers Layer 7 and Layer 4 attack methods, such as bypassing CF attacks, Google Project Shield, and DDoS Guard Free, as well as various HTTP attack types like GET, POST, and HEAD requests. It also includes tools for DNS lookup, Geo IP address lookup, and subnet IP address lookup.
Summary of Features:
- Bypassing various security measures (Cloudflare UAM, CAPTCHA, BFM, NOSEC, DDoS Guard, Google Shield, V Shield, and more)
- Layer 7 attack methods (CF bypass, Google Project Shield bypass, HTTP 2.0 attack, spoof attack, and more)
- Layer 4 attack methods (UDP attack, TCP attack)
- Tools for DNS lookup, Geo IP address lookup, and subnet IP address lookup
9- HTTP Flood with Python
PyFlooder is an HTTP Flood Python script that can launch a DDoS attack by generating a configurable number of random GET requests and sending them to the target, potentially causing a normal website to stop functioning within 10 seconds.
10- Hacking toolKit
This is a free and open-source all-in-one hacking toolkit designed for hackers, penetration testers, and cybersecurity professionals.
It offers a wide range of tools, including those for information gathering, wireless attacks, SQL injection, phishing attacks, web attacks, post-exploitation, forensics, payload creation, exploit frameworks, reverse engineering, DDoS attacks, remote administration, XSS attacks, steganography, and more.
The toolkit also includes features for anonymously hiding tools and offers tools for social media brute force, Android hacking, IDN homograph attack, email verification, hash cracking, WiFi deauthentication, social media discovery, payload injection, web crawling, and various other functionalities.
Summary of Features:
- All-in-one hacking toolkit for hackers, penetration testers, and cybersecurity professionals
- Includes a wide range of tools for various purposes such as information gathering, wireless attacks, SQL injection, phishing attacks, web attacks, post-exploitation, forensics, payload creation, exploit frameworks, reverse engineering, DDoS attacks, remote administration, XSS attacks, steganography, and more
- Features for anonymously hiding tools
- Tools for social media brute force, Android hacking, IDN homograph attack, email verification, hash cracking, WiFi deauthentication, social media discovery, payload injection, web crawling, and more
Wireless Attack Tools
- WiFi-Pumpkin
- pixiewps
- Bluetooth Honeypot GUI Framework
- Fluxion
- Wifiphisher
- Wifite
- EvilTwin
- Fastssh
- Howmanypeople
DDoS Attack
11- Overload DoS Tool
This is a unique simple yet powerful tool called 📡 Overload DoS Tool, that can be installed on Windows, Linux, macOS, and Android using Termux.
Avaiable attacks
- HTTP: This attack consists of exhausting the victim by sending a huge amount of HTTP GET requests, eventually taking it down and preventing others from accessing its resources.
- Slowloris: Just like an HTTP attack, Slowloris also aims to block other users from accessing a certain resource, but it does that by connecting virtual hosts with a slow connection to the victim. The victim will eventually have a lot of slow connections open and will block new users from accessing its resources.
- SYN-Flood: This attack relies on the Transmission Control Protocol (TCP) connections and takes advantage of the TCP 3-Way Handshake by sending a lot of packets with the SYN flag, but never responding to the SYN-ACK packets sent by the victim, which makes it wait forever with an open connection. If the victim does not close the connection, it will eventually block new connections.
- ARP-Spoof: This attack works on layer 2 of the OSI model and specifically targets the Address Resolution Protocol (ARP). It involves sending an adulterated packet to the victim, tricking it into thinking that the attacker's machine is the gateway of the local network. The attacker can then intercept and analyze all of the victim's packets.
- Disconnect: This attack blocks the victim from accessing the internet on the local network during the attack.
12- torDDoS
TorDDos is a Python tool to automatize DDos attacks to a website from the Tor network.
13- Spurt
Spurt is a powerful testing tool designed to simulate high volumes of traffic and evaluate the performance and resilience of web servers.
14- Katana Botnet
Katana Botnet used for DDoS attacks based on the Mirai Botnet.
15- FastNetMon
FastNetMon is a powerful DDoS detector/sensor that is built using multiple packet capture engines: NetFlow, IPFIX, sFlow, and AF_PACKET (port mirror). It excels in performance and is designed to effectively detect and mitigate DDoS attacks.
Supported Package Capture Engines
- NetFlow v5, v9, v9 Lite
- IPFIX
- PCAP
- AF_PACKET (recommended)
- AF_XDP (XDP based capture)
- Netmap (deprecated, still supported only for FreeBSD)
- PF_RING / PF_RING ZC (deprecated, available only for CentOS 6 in 1.2.0)
Features
- Detects DoS/DDoS in as little as 1-2 seconds
- Scales up to terabits on single server (sFlow, Netflow, IPFIX) or to 40G + in mirror mode
- Trigger block/notify script if an IP exceeds defined thresholds for packets/bytes/flows per second
- Complete support for most popular attack types
- Thresholds can be configured per-subnet basis with the hostgroups feature
- Email notifications about detected attack
- Complete IPv6 support
- Prometheus support: system metrics and total traffic counters
- Flow and packet export to Kafka in JSON and Protobuf format
- Announce blocked IPs via BGP to routers with ExaBGP or GoBGP (recommended)
- Full integration with InfluxDB and Graphite
- API
- Redis integration
- MongoDB protocol support compatible with native MongoDB and FerretDB
- VLAN untagging in mirror and sFlow modes
- Capture attack fingerprints in PCAP format
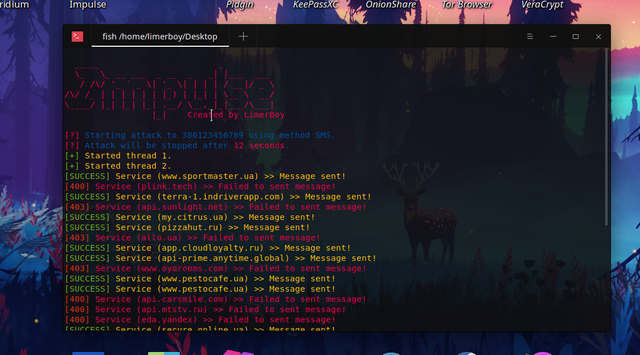
16- Impulse
💣 Impulse Denial-of-service ToolKit that supports DDoS, and dozen of DoS tools and services.
Methods
- SMS: Sends a massive amount of SMS messages and calls to a single target
- EMAIL: Sends a massive amount of Email messages to a target
- NTP: NTP amplification is a type of DDoS attack that exploits publically-accessible NTP servers to overwhelm the target with UDP traffic
- SYN: A SYN flood is a type of DDoS attack that aims to make a server unavailable by consuming all available server resources
- UDP: A UDP flood is a type of DDoS attack that overwhelms a targeted server with a large number of UDP packets, resulting in a denial-of-service to legitimate traffic
- POD (Ping of Death): Ping of Death is a DoS attack that attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets
- ICMP: ICMP flood, also known as Ping flood, is a common DoS attack that overwhelms a victim's computer with ICMP echo requests (pings)
- HTTP: HTTP Flood is a type of DDoS attack that manipulates HTTP and sends unwanted requests to attack a web server or application
- Slowloris: Slowloris is a denial-of-service attack that overwhelms a targeted server by maintaining many simultaneous HTTP connections
- Memcached: A memcached DDoS attack overloads a targeted victim with internet traffic by spoofing requests to a vulnerable UDP memcached server
Supported platforms
- Windows
- Linux
- macOS
- Termux
17- UFONet
UFONet - is a free software, P2P and cryptographic -disruptive toolkit- that allows to perform DoS and DDoS attacks; on the Layer 7 (APP/HTTP) through the exploitation of Open Redirect vectors on third-party websites to act as a botnet and on the Layer3 (Network) abusing the protocol.
It also works as an encrypted DarkNET to publish and receive content by creating a global client/server network based on a direct-connect P2P architecture.
18- Zero-attacker
Zero-attacker is a free and open-source multipurpose hacking tool with over 15+ multifunction tools.