24 Free Open-source Keylogger Windows, Linux, and macOS
A keylogger is a type of software or hardware device that records keystrokes on a computer or mobile device. It can capture every keystroke made by a user, including passwords, messages, and other sensitive information.
Use-cases for keyloggers include:
- Monitoring employee activity in the workplace to ensure productivity and prevent misuse of company resources.
- Parental control to monitor and protect children's online activities.
- Law enforcement agencies may use keyloggers as part of an investigation to gather evidence.
Benefits of keyloggers include:
- Detecting unauthorized access or suspicious activities on a computer system.
- Recovering lost or forgotten passwords.
- Monitoring and improving user experience by analyzing keystrokes and user interactions.
However, it is important to note that keyloggers can also be used for malicious purposes, such as stealing personal information or conducting unauthorized surveillance. The use of keyloggers must comply with legal and ethical standards, and user consent should be obtained when monitoring activities.
Keyloggers can potentially be used for hacking purposes. Malicious actors can use keyloggers to record sensitive information, such as passwords, credit card details, and personal data, without the user's knowledge. This information can then be used for unauthorized access or identity theft.
It is essential to ensure your devices are protected against keyloggers by using up-to-date antivirus software, practicing safe browsing habits, and being cautious of downloading and installing software from untrusted sources. Regularly monitoring your accounts for suspicious activities and using strong, unique passwords can also help protect against potential hacking attempts.
In this list, you can find the best open-source free-to-use Keylogger apps for Windows, Linux, and macOS. Some of them require some technical skills to be used.
1- Sinister
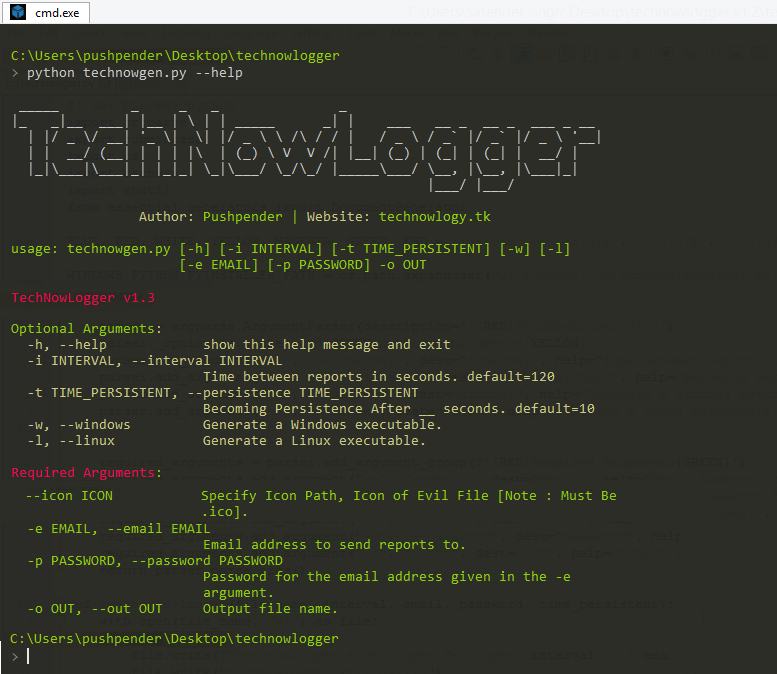
Sinister is Keylogger Generator for Windows/Linux, which sends key-logs & screenshot via email with other juicy target info written in Python 3.
Platforms: Windows 10, Windows 8.1, Windows 7, and Kali Linux.
Features
- Works on Windows/Linux
- Notify New Victim Via Email
- Undetectable
- Persistence
- Email Credentials Validation before Payload Generation.
- Can receive Keylogs in any email provider such as GMAIL, YAHOO, OUTLOOK, Custom SMTP.
- SMTP Server/ Port
- Sends Screenshot of Victim PC's Screen via email
- Creates Executable Binary With Zero Dependencies
- Create less size ~ 5mb payload with advance functionality
- Obfusticate the Payload before Generating it, hence Bypassing few more antivirus
- Generated Payload is Encoded with base64, hence makes extremely difficult to reverse engineer the payload
- Function to Kill Antivirus on Victim PC and tries to disable the security
- Awesome Colourful Interface to generate payload
- On Attacker Side: While Creating Payload, Script Automatically Detects Missing Dependencies & Installs Them
- Distinguish Log Data on the Basics of Active Window Name (Check Image for Better Understanding)
- Able to add custom Icon to evil file
- Built-in Binder which can bind Keylogger to Any File [.pdf, .txt, .exe etc], Running legitimate file on front end & evil codes in back-end as a service.
- Checks for Already Running Instance on System, If running instance found, then only legitimate file is executed [Multiple Instance Prohibiter to avoid Receiving Duplicate Email Logs].
- Attacker can Create/Compile for Both Windows/Linux OS Using Linux System, But Can only Create/Compile Windows Executable using Windows Machine
- Retrieves Saved Passwords from victim System and sends it to Attacker.
2- logkeys (Linux)
logkeys is a Linux keylogger. Although it is not more advanced than other available Linux keyloggers like lkl and uberkey, it is relatively newer and more up to date. One advantage of logkeys is that it doesn't unreliably repeat keys and it shouldn't crash your X. In general, it simply works. logkeys utilizes the event interface of the Linux input subsystem. Once fully configured, it logs all common character and function keys while also recognizing the Shift and AltGr key modifiers.
3- Letterpress (Ubuntu)
Letterpress is a free and open-source Python-based Keylogger app for Ubuntu desktop.
Letterpress can:
- hides in plain sight
- compiles to python bytecode for obfuscation
- encrypts keylog files so that only you can read them
- uploads keylog files to pastebin for remote exfiltration
- is easily deployable with the Bash Bunny
5- linux-keylogger
This linux-keylogger is an open-source simple C++ keylogger prototype, which is meant to showcase the basics of Linux keylogging.
Replace /dev/input/event4 (main.cpp) with your keyboard event, $cat /proc/bus/input/devices should give you an idea about it
The keylogger needs root privileges to be run. You can use the build.sh script to try it out, or compile it with the command g++ main.cpp -o main && sudo ./main
6- XKeylogger
Keylogger for Linux with GTK+ 3 based desktop environments such as GNOME, XFCE, LXDE etc.
XKeylogger features include:
- Keystrokes logging
- Clipboard logging
- Screenshot after every paste (Ctrl+V)
7- Windows Keylogger
This is a Keylogger designed for Windows systems, written in C#. It is capable of running undetected by most popular antivirus software.
8- Tanit Python Keylogger
9- Keylogger (Windows)
This is a Windows OS keylogger with a hook mechanism (i.e. with a keyboard hook procedure).
10- Keylogger (C++)
Keylogger is a 100% invisible keylogger, not only for users. It monitors all keystrokes and mouse clicks. Additionally, it has a separate process that continuously captures system screenshots and sends them to an FTP server at specified intervals.
It is designed in visual C++ and it is run in the background in stealth mode (Hidden Window).
This Keylogger is a stealthy tool that monitors keystrokes, mouse clicks, and captures system screenshots. It is designed to be undetectable and tamper-proof. It logs all keystrokes, provides a reader-friendly version, and offers continuous screenshots. The captured data is sent to an FTP server and the tool can automatically start on system bootup and copy itself to a specific folder.
11- PyLoggy
PyLoggy is a simple and powerful Python keylogger that can log keystrokes, mouse clicks, take screenshots, and more! The tool can send the logs to your email every minute (this interval can be changed).
12- macOS Keylogger
This is a macOS Keylogger that is built as a proof-of-concept using C language.
13- Simple Keylogger (Windows, Linux, and macOS)
This is an open-source and free simple keylogger app for Windows, Linux, and macOS.
14- Stitch
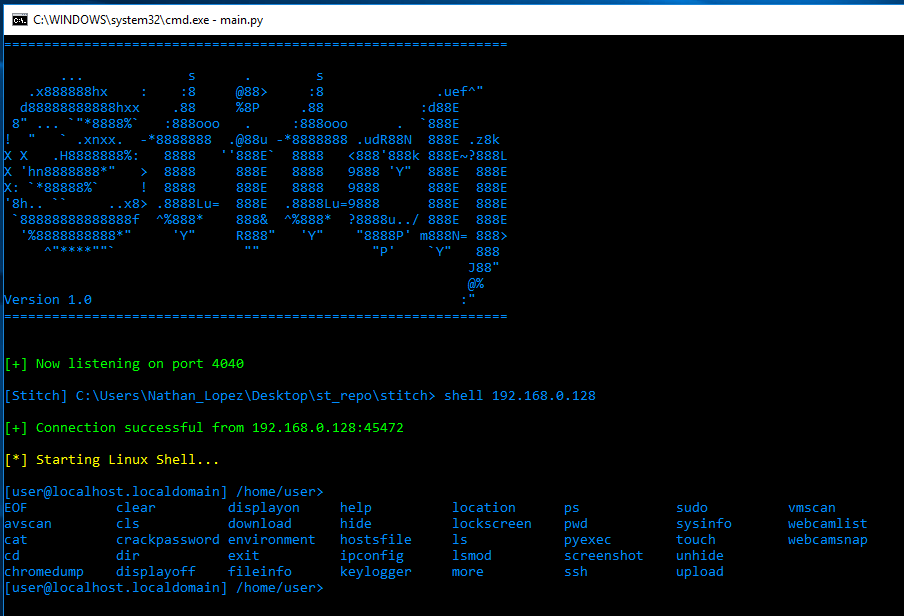
Stitch is an open-source Remote Administration Tool (RAT) with rich key logging functionality. It works on Windows, Linux, and macOS.
It also comes with dozens of RAT tools and features and platform-specific features.
15- Lo0sR
Lo0sR is a simple python Keylogger.
Features
- Keylogging
- Takes Photos through Webcam
- Screenshotting
- If CTRL-C copies what is being copied
- Dumps all passwords stored in Chrome
- Dumps Chrome History
- Sends Mail every 5 min with all the gathered data (The Keylogger deletes all already sent data)
- Moves itself to Startup
- Gets Window name that is currently being used
- Hides Folder
- If Skype is installed: gets all Personal Information from Skype DB
16- w1n-keylogger (Windows)
Windows keylogger made in python.
17- PySimpleLogger
A simple python code that you can use to make an effective keylogger.
18- KeyloggerScreenshot
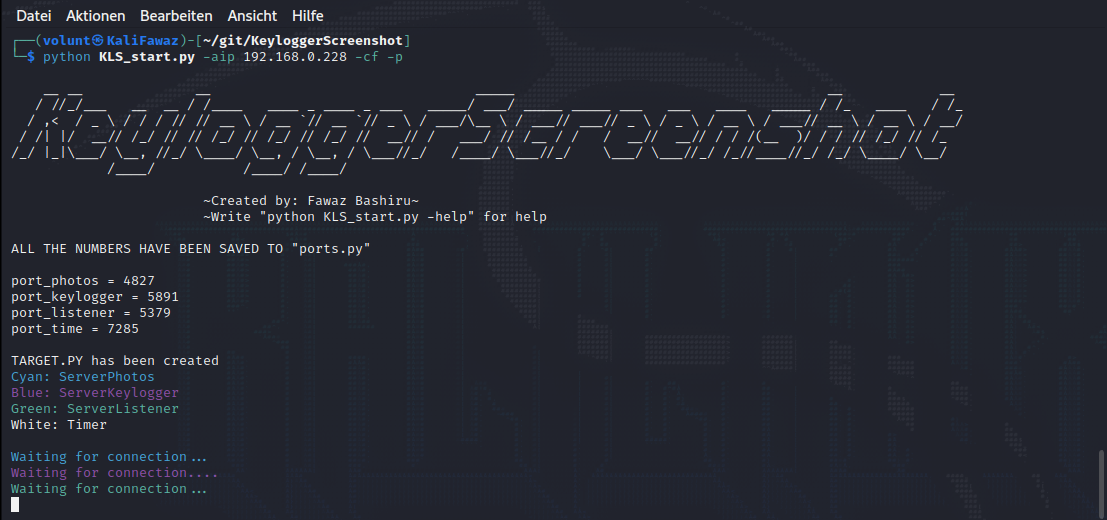
KeyloggerScreenshot is a tool that enables attackers to capture all the information typed by the target, take screenshots at specific intervals, and store all the audio recorded from the target's microphone on your server. Every mouse click made by the target will also be logged on the server. Follow the instructions in the "KeyloggerScreenshot" guide to set up your own server.
19- Keyboard-Tracker (Windows)
Application to track all user keyboard strokes.
20- Inputs To Mail
This is a simple yet powerful app that allows you to get Keyboard, Mouse, ScreenShot, Microphone Inputs and Send to your Mail. The purpose of the project is testing the security of information systems.
21- Unknown-Logger
Unknown Logger is an advanced Windows Keylogger with features like (Disable CMD, Screenshotter, Client Stub Builder, Low Level Keyhooks, Hide Application, Respawner, Delete Chrome and Firefox data, and more!).
Features
- Low level keyhooks
- A client with runtime builder
- Disable CMD
- Hide application
- Assembly editor
- Icon editor
- Disable control panel
- Fake messagebox
- Respawner
- Site visitor
- Download and execute
- Disable UAC
- Disable taskmanager
- Take screenshots
- File binder
- Encrypter
- Delete Chrome and Firefox data
- Add application to startup
22- ToRat
ToRat is an amazing remote admin tool with keylogging functionality.
23- Impost3r
Impost3r is a keylogger that enables users to capture passwords .
24- Stealerium
Stealer is an open-source data extraction, keylogger, and clipper, and more. It is basically an advanced pentesting and hacking tool.

