41 Open-source and Free Vulnerability Scanners For Pentesting and Web App Security
Table of Content
Vulnerability scanners are software applications that monitor systems for potential security threats. These tools scan your network and systems for vulnerabilities that could be exploited by hackers. They check for unpatched software, insecure system configurations, and other weaknesses.
Vulnerability Scanners for Web Apps
Web application vulnerability scanners, specifically, are designed to scan web applications for vulnerabilities such as SQL injection, cross-site scripting (XSS), and path traversal vulnerabilities.
They are important because they automate the process of checking web applications for security vulnerabilities, which can be a time-consuming and complex task. By identifying vulnerabilities early, organizations can address them before they are exploited by hackers.
Vulnerability Scanners for HIPAA and GDPR Compliance
Vulnerability scanners are particularly crucial in maintaining compliance with regulations such as HIPAA (Health Insurance Portability and Accountability Act) and GDPR (General Data Protection Regulation). These regulations require organizations to take adequate measures to protect sensitive data like healthcare and personal information. By identifying and addressing vulnerabilities, businesses can ensure they are not inadvertently exposing such sensitive data.
For Enterprise
In an enterprise setting, vulnerability scanners are pivotal. They help maintain the security of large networks with numerous connected devices.
They can monitor these networks continuously, providing regular updates about potential vulnerabilities and helping enterprises to stay ahead of potential security threats.
The ability to scan on a schedule, or continuously, ensures that new vulnerabilities are identified as soon as possible, reducing the window of opportunity for attackers. They also provide detailed reports, which can help in auditing and demonstrating compliance with various security standards.
In this post, we offer you the best open-source Vulnerability Scanners
1- vMass Bot
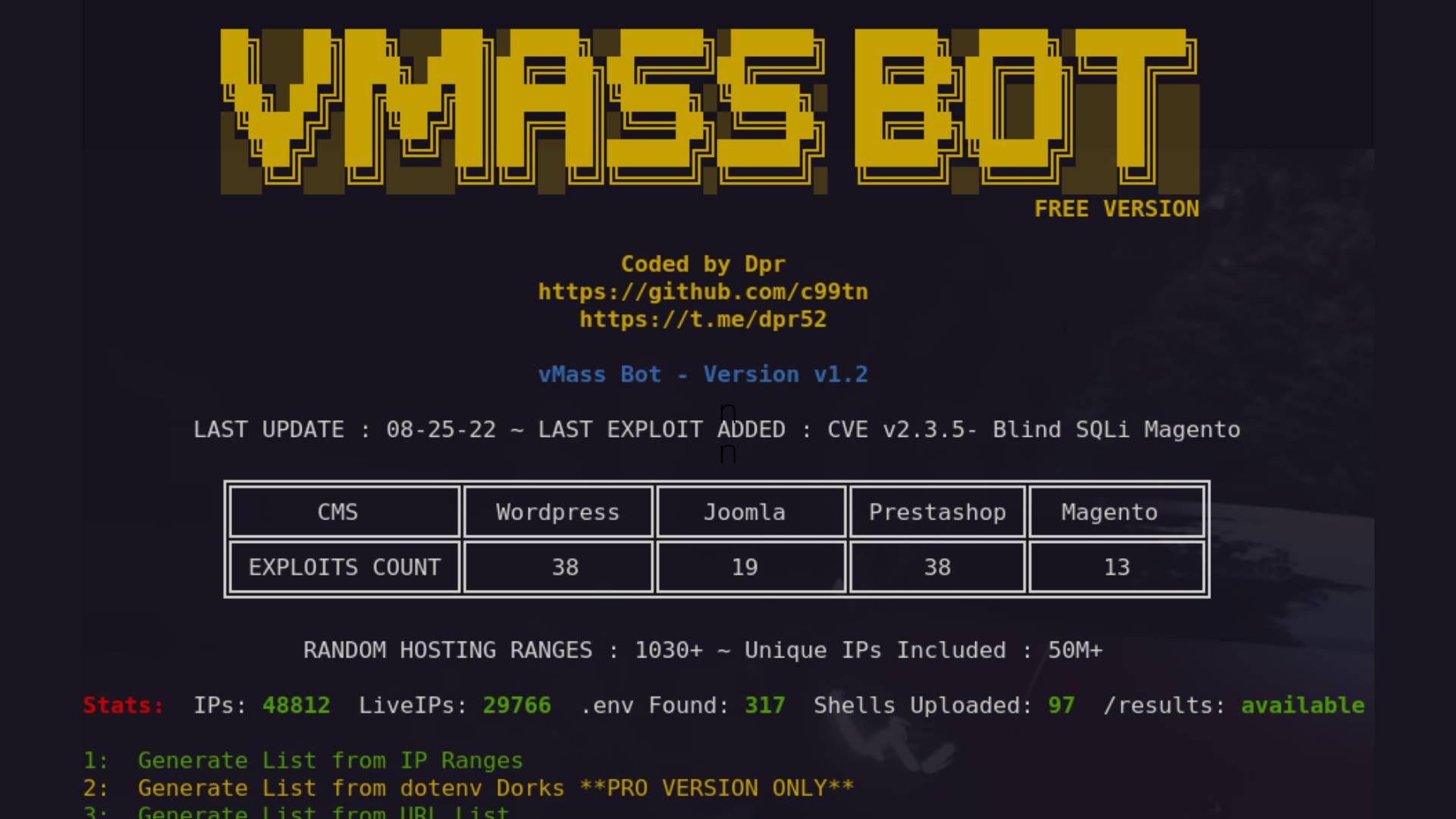
vMass Bot is an open-source and free tool that automates the exploitation of remote hosts by finding environment files, extracting tools and information, detecting the target's CMS, and attempting to auto-exploit and upload shell payload.
It can generate host lists from various sources if no target list is provided. Extracted tools can be filtered and tested, and the bot can also use hosts with phpmyadmin access for auto upload if CMS exploits fail. Results can be delivered to a Telegram channel, and the entire process can be automated using the AUTOPILOT option.
2- Vuls: VULnerability Scanner
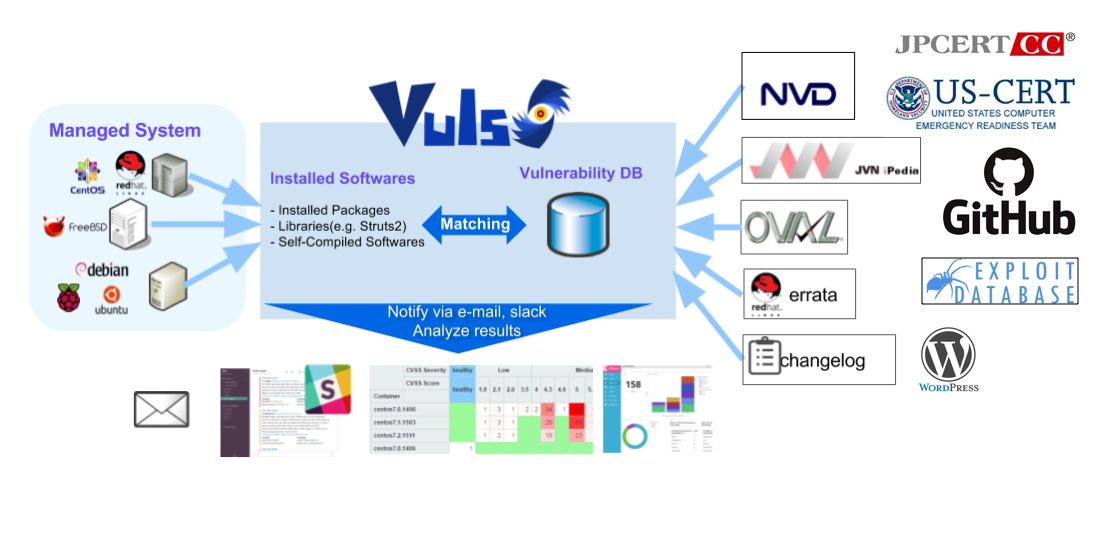
Vuls is an open-source, agent-less vulnerability scanner for various operating systems and environments. It helps system administrators by automatically detecting vulnerabilities, informing about affected servers, and generating regular reports.
It supports major Linux, FreeBSD, Windows, macOS systems, and can be used in cloud, on-premise, and Docker container environments.
It also enables DevOps to scan containers, and and provide nondestructive testing for all.
Vuls also include a strong suite to test WordPress, and its plugins and themes.
3- VulnX
Vulnx is an intelligent bot that can automatically inject shells and detect security vulnerabilities in CMS systems. It can perform quick CMS security detection, information collection, and vulnerability scanning. Unlike other tools that require manual shell injection, Vulnx analyzes the target website for vulnerabilities and injects the shell if a vulnerability is detected.
Features
- Detects cms (WordPress, Joomla, PrestaShop, Drupal, opencart, Magento, lokomedia)
- Target information gatherings
- Target Subdomains gathering
- Multi-threading on demand
- Checks for vulnerabilities
- Auto shell injector
- Exploit dork searcher
Ports ScanHigh LevelDns-Servers Dump- Input multiple target to scan.
- Dorks Listing by Name by ExploitName.
- Export multiple target from Dorks into a logfile.
4- XAttacker
XATTACKER is a comprehensive tool for scanning and automatically exploiting vulnerabilities in web applications. It can detect a website's architecture, identify vulnerabilities based on the detected Content Management System (CMS), generate an exploit, and send the user the exploit link.
Features include a vulnerability scanner, auto-exploiting, CMS attacking, dork search with multiple search engines, and plain text reporting.
Supported CMS solutions
- Joomla
- WordPress
- Prestashop
- Drupal
- Lokomedia
Supported systems
- Android
- Linux
- Windows
- macOS

5- Commix
Commix (short for [comm]and [i]njection e[x]ploiter) is a powerful, user-friendly, and versatile open-source tool designed for penetration testing. Developed by Anastasios Stasinopoulos, it automates the detection and exploitation of command injection vulnerabilities in web applications. It's portable, modular, and compatible with various systems, platforms, CMS, and web applications, making it a crucial tool for security testing.
6- KILLSHOT
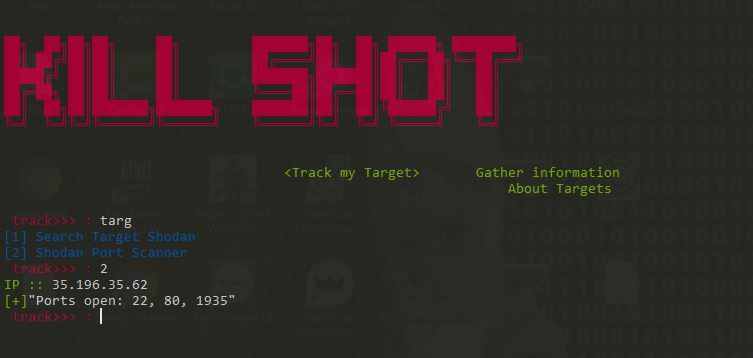
KillShot is a penetration testing framework, an information-gathering tool, and a website vulnerability scanner.
KillShot allows you to spider your website, gather important information automatically, and identify vulnerabilities. Key features include:
- Information gathering using whatweb-host-traceroute-dig-fierce-wafw00f
- CMS identification and vulnerability detection via Cms Exploit Scanner and WebApp Vul Scanner
- Automatic scanning using Nmap and Unicorn
- Backdoor generation with simple PHP backdoors for manual upload and connection to the target
KillShot also includes a simple Ruby fuzzer that has been tested on VULSERV.exe, and a Linux log clear script to change the content of login paths. Spider can help you identify site parameters and scan for XSS and SQL vulnerabilities.
Other scanning capabilities include:
- Port scanning
- App scanning
- Shell scanning
7- PatrOwl
PatrowlHears is a real-time Vulnerability Intelligence platform that provides CVE, exploits, and threat news. It is part of Patrowl's suite of open-source security operations and threat intelligence solutions. Developed in Python, it uses Django for the backend and Vue.js + Vuetify for the frontend, with RabbitMQ and Celery supporting asynchronous tasks and engine scalability. It can be accessed via the embedded web interface or the REST-API.
8- XAttacker Tool
The X Attacker Tool ☣ is a modified version of the original X Attacker, designed to scan websites for vulnerabilities and automatically exploit them.
This tool is useful for assessing the security of your website by identifying any potential vulnerabilities. It can also be used to gain access to shells, send files, deface websites, control panels, and databases.
It's capable of detecting security issues within CMS, as well as numerous vulnerabilities in systems such as WordPress, Joomla, and others.
9- Fox Ex v2
{Fox Ex v2} tool is a free and open-source solution that is designed for hacking tests. It exploits vulnerabilities and backdoors discovered recently, with the ability to upload shell +50 exploit and get +3000 shell in 2 minutes.
10- RVuln
RVuln is a multithreaded vulnerability scanner written in Rust that scans for XSS vulnerabilities. It is compatible with Ubuntu/Debian based OS, Arch Linux based OS, and Windows 10.
11- wsltools - Web Scan Lazy Tools
wsltools is an elegant and simple Web Scan auxiliary library for Python.

12- OWASP ASST
(Automated Software Security Toolkit)
ASST (Automated Software Security Toolkit) is an open-source, CLI application developed with JavaScript (Node.js framework) for scanning source code.
Currently, it focuses on PHP and MySQL languages, but its core functionalities are designed for contributions from programmers to add plugins or extensions for other languages and their frameworks. ASST is unique in that it scans PHP language according to OWASP Top 10 Web Application Security Risks.
13- Phaser
Phaser is an exceptional, high-performance attack surface mapper and vulnerability scanner. Give it a target, and it will confidently generate a comprehensive report with every detail it discovers, effectively saving you countless hours of manual audit and eliminating the need to juggle multiple tools.
14- TechViper
TechViper is a web security scanner that identifies vulnerabilities in web applications. It provides detailed security assessments and helps improve the security of web applications by detecting issues such as Remote Code Execution, Reflected XSS, Template Injection, and SQL Injection.
Supported systems
- Kali Linux
- Android
- Windows
15- Himawari
Himawari is an open-source free Web Vulnerability Scanner written in Golang.
16- VulnScanX
VulnScanX v2.0 is a command-line application that helps identify vulnerabilities in web applications, focusing on Cross-Site Scripting (XSS), SQL Injection (SQLi), and Remote Code Execution (RCE). Key features include testing for various types of vulnerabilities, multithreading support, automated link crawling and testing, logging of results, an improved user interface, and enhanced payload file import.
Features
- Reflected XSS Testing
- DOM-based XSS Testing
- SQL Injection Testing
- Remote Code Execution Testing
- Server-Side Template Injection Testing
- Open Redirection Testing
- Multithreading Support
- Automated Link Crawling and Testing
- Results Logging
- Improved User Interface
- Efficient Payload File Import
17- Enlightn Security Checker
A PHP dependency vulnerabilities scanner based on the Security Advisories Database.
18- Tools for Finding Bugs and Vulnerabilities
This repo includes a dozen of a free and open-source tools to search and discover web app bugs and vulnerabilities.
19- RapidScan
RapidScan is a multi-tool web vulnerability scanner that executes various security scanning tools, checks for vulnerabilities, and provides spontaneous results. It is light-weight, time-efficient, and helps to identify false positives. It offers vulnerability definitions and remediation advice. Features under development include association with OWASP Top 10 & CWE 25, artificial intelligence for tool deployment, detailed reports in PDF format, and on-the-run Metasploit auxiliary modules.
Features
- one-step installation.
- executes a multitude of security scanning tools, does other custom coded checks and prints the results spontaneously.
- some of the tools include
nmap, dnsrecon, wafw00f, uniscan, sslyze, fierce, lbd, theharvester, amass, niktoetc executes under one entity. - saves a lot of time, indeed a lot time!.
- checks for same vulnerabilities with multiple tools to help you zero-in on false positives effectively.
- extremely light-weight and not process intensive.
- legends to help you understand which tests may take longer time, so you can
Ctrl+Cto skip if needed. - association with OWASP Top 10 & CWE 25 on the list of vulnerabilities discovered. (under development)
- critical, high, medium, low and informational classification of vulnerabilities.
- vulnerability definitions guides you what the vulnerability actually is and the threat it can pose.
- remediation tells you how to plug/fix the found vulnerability.
- executive summary gives you an overall context of the scan performed with critical, high, low and informational issues discovered.
- artificial intelligence to deploy tools automatically depending upon the issues found. for eg; automates the launch of
wpscanandplecosttools when a wordpress installation is found. (under development) - detailed comprehensive report in a portable document format (*.pdf) with complete details of the scans and tools used. (under development)
- on the run metasploit auxilliary modules to discover more vulnerabilities. (under development)
20- afrog
afrog is a high-performance security tool for bug bounty, pentesting, and red teaming. It features a fast, stable vulnerability scanner with low false positives, customizable PoCs, and detailed HTML vulnerability reports. afrog supports user-defined PoC and has several built-in types. It is open-source and has an active community exchange group.
21- Threat-Patrol
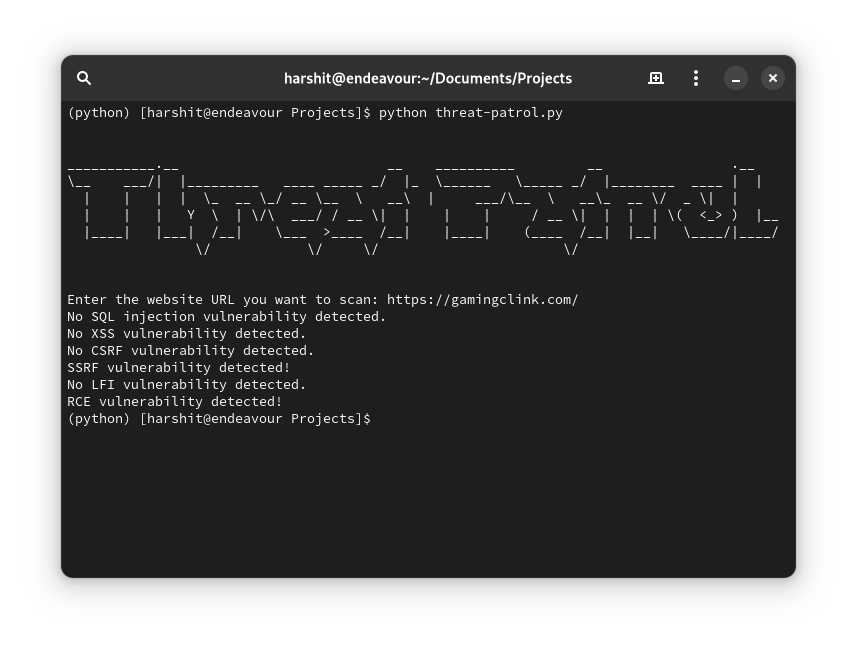
Threat-Patrol is a Python script that scans websites for potential vulnerabilities including SQL injection, XSS, CSRF, SSRF, LFI and RCE. It is user-friendly, provides instant results, automatically scans for vulnerabilities, and offers a simple command line interface.
22- w4af
w4af is an open-source web application security scanner, originally based on w3af, that helps identify and exploit vulnerabilities in web applications. It is currently in an early alpha development phase and user experience and bug reports are welcomed, but no warranties are made about the software as it is still a work in progress.
23- Damn Web Scanner
The Damn Web Scanner is a web vulnerabilities scanner extension for Chrome and Opera. It scans for SQL Injection, Cross Site Scripting, Local File Inclusion, and Remote Commands Execution. It can detect server status, list vulnerabilities, reuse cookies and user-agents for cookie-authenticated pages, export vulnerabilities into a CSV file, and launch scans when a form is submitted or a page is opened via the URL bar.
Currently it scans for:
- SQL Injection : Time based SQLi scanner using polyglot vectors (MySQL, SQLite, Oracle, Postgresql, SQL Server)
- Cross Site Scripting : Using a browser simulator (Ghost)
- Local File Inclusion
- Remote Commands Execution using polyglot vectors based on time
All the features are:
- Detect if the server is up with a "/ping" request
- New XSS vectors, work in different contexts (JS var, JS function, inside HTML tag, outside HTML tag)
- Basic page to list the vulnerabilities URL and TYPE
- Re-use your cookies and user-agent to get access to page with cookie-authentication
- Export vulnerabilities into a CSV file
- Launch scan when a form is submitted or a page is opened via the URL bar
24- Nuclei
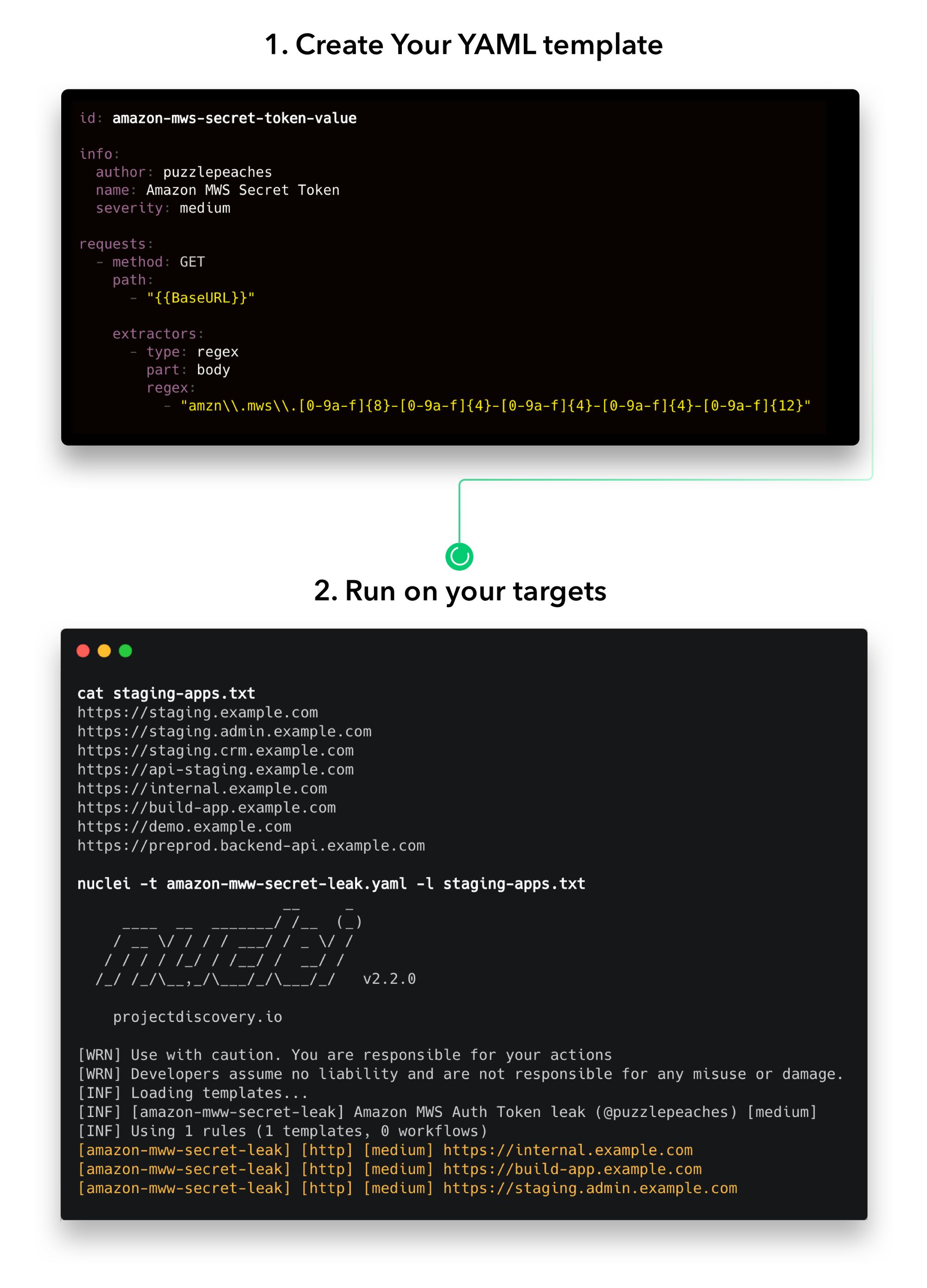
Nuclei is a fast, customizable vulnerability scanner that sends requests across targets based on a template. It provides zero false positives and can scan a large number of hosts. Nuclei supports various protocols and can model all kinds of security checks thanks to its powerful and flexible templating.
25- Raccoon
Raccoon is a high-performance offensive security tool for reconnaissance and vulnerability scanning. It provides DNS details, WHOIS information, TLS data, port scanning, services and scripts scanning, URL fuzzing, subdomain enumeration, web application data retrieval, WAF detection, and supports anonymous routing. It uses asyncio for improved performance and saves output to files.
Features
- DNS details
- DNS visual mapping using DNS dumpster
- WHOIS information
- TLS Data - supported ciphers, TLS versions, certificate details and SANs
- Port Scan
- Services and scripts scan
- URL fuzzing and dir/file detection
- Subdomain enumeration - uses Google dorking, DNS dumpster queries, SAN discovery and bruteforce
- Web application data retrieval:
- CMS detection
- Web server info and X-Powered-By
- robots.txt and sitemap extraction
- Cookie inspection
- Extracts all fuzzable URLs
- Discovers HTML forms
- Retrieves all Email addresses
- Scans target for vulnerable S3 buckets and enumerates them for sensitive files
- Detects known WAFs
- Supports anonymous routing through Tor/Proxies
- Uses asyncio for improved performance
- Saves output to files - separates targets by folders and modules by files
26- Fuxploider
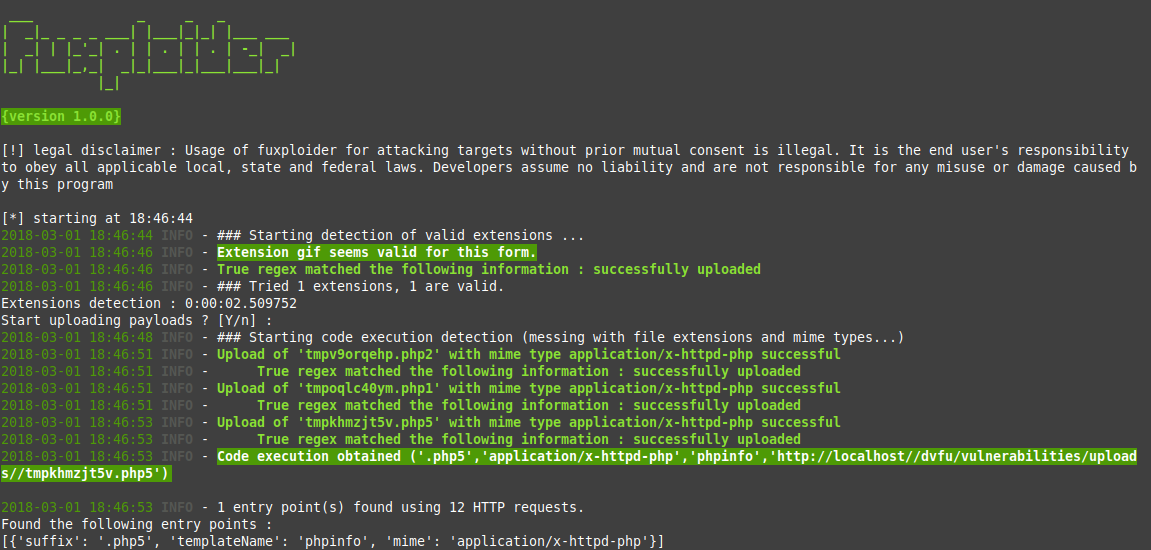
Fuxploider is an unrivaled, open-source penetration testing tool that masterfully automates the process of detecting and exploiting file upload form flaws. With a unique ability to discern the file types allowed for upload, it adeptly determines the most effective technique to upload web shells or any malicious file onto the targeted web server.
27- OWASP Nettacker
The OWASP Nettacker project is a free open-source tool designed to automate information gathering, vulnerability scanning, and report generation for networks. This includes identifying services, bugs, vulnerabilities, misconfigurations, and other relevant information. This software will use TCP SYN, ACK, ICMP, and many other protocols to detect and bypass Firewall/IDS/IPS devices. Utilizing a unique method in OWASP Nettacker, it can discover protected services and devices such as SCADA, giving it a competitive edge over other scanners and making it one of the best.
OWASP IoT Scanner
- Python Multi Thread & Multi Process Network Information Gathering Vulnerability Scanner
- Service and Device Detection ( SCADA, Restricted Areas, Routers, HTTP Servers, Logins and Authentications, None-Indexed HTTP, Paradox System, Cameras, Firewalls, UTM, WebMails, VPN, RDP, SSH, FTP, TELNET Services, Proxy Servers and Many Devices like Juniper, Cisco, Switches and many more… )
- Asset Discovery & Network Service Analysis
- Services Brute Force Testing
- Services Vulnerability Testing
- HTTP/HTTPS Crawling, Fuzzing, Information Gathering and …
- HTML, JSON, CSV and Text Outputs
- API & WebUI
- This project is at the moment in research and development phase
- Thanks to Google Summer of Code Initiative and all the students who contributed to this project during their summer breaks:
28- EMBA
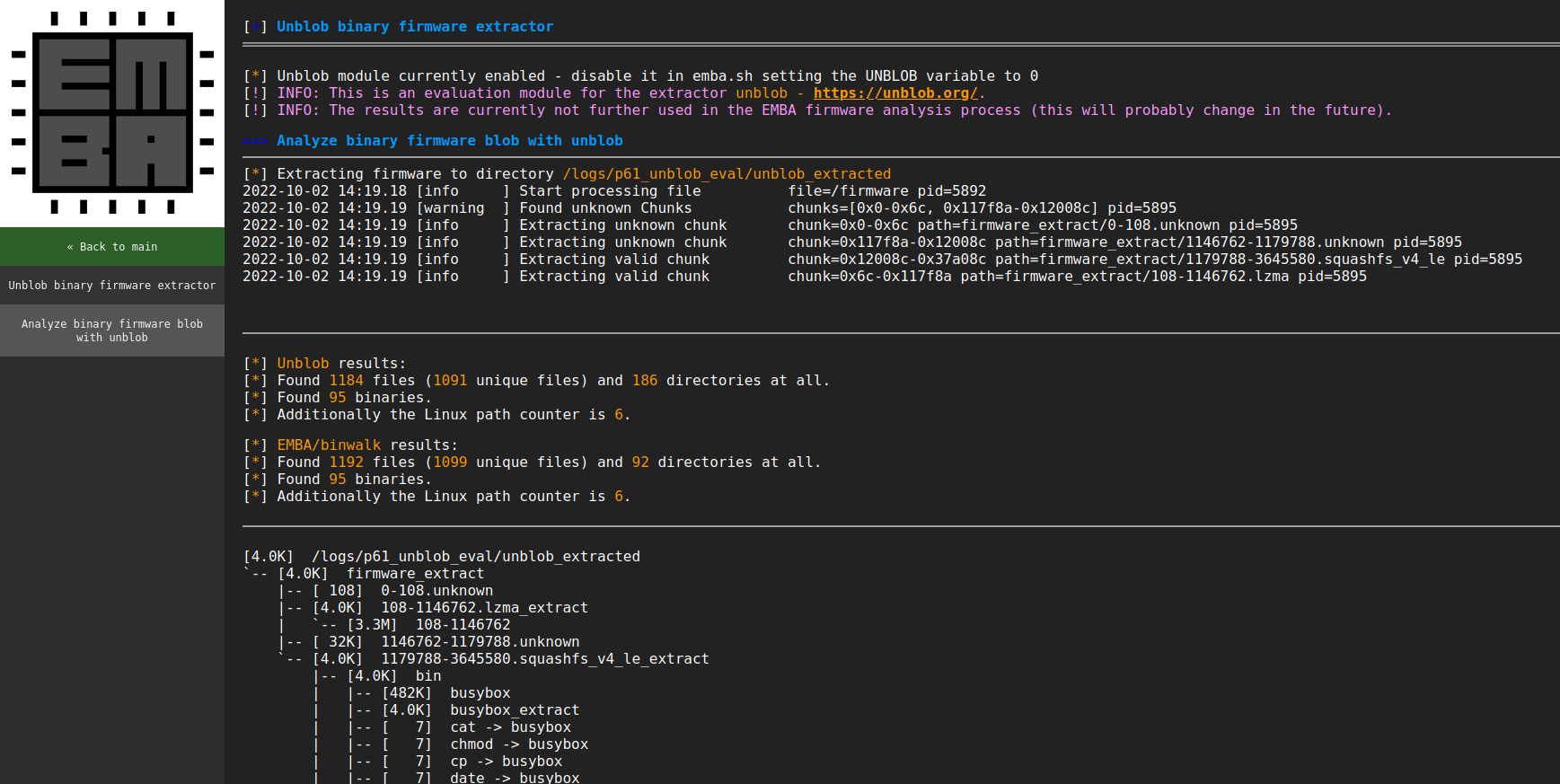
EMBA is a firmware analysis tool designed for penetration testers and product security teams. It supports the entire security analysis process, from firmware extraction to static and dynamic analysis, and generates a web report. EMBA identifies potential vulnerabilities in firmware, such as insecure binaries, outdated software components, vulnerable scripts, or hard-coded passwords. It provides comprehensive information about the firmware, allowing testers to decide on focus areas and interpret the results.
29- CRLFuzz
CRLFuzz is a free, open-source tool written in Go, designed for fast scanning of CRLF vulnerabilities.
30- Jackhammer
Jackhammer is a collaboration tool designed to bridge the gap between security, development, and QA teams. It performs static and dynamic code analysis, identifies security vulnerabilities, and helps manage these vulnerabilities in an era of continuous integration and deployment.
It operates on Role Based Access Control (RBAC) and features dashboards for individual and team scans. Jackhammer is built on a pluggable architecture, allowing integration with any open source or commercial tool, and uses the OWASP pipeline project to run multiple tools against your code, web app, mobile app, CMS, or network.
Key Features:
- Provides unified interface to collaborate on findings
- Scanning (code) can be done for all code management repositories
- Scheduling of scans based on intervals # daily, weekly, monthly
- Advanced false positive filtering
- Publish vulnerabilities to bug tracking systems
- Keep a tab on statistics and vulnerability trends in your applications
- Integrates with majority of open source and commercial scanning tools
- Users and Roles management giving greater control
- Configurable severity levels on list of findings across the applications
- Built-in vulnerability status progression
- Easy to use filters to review targeted sets from tons of vulnerabilities
- Asynchronous scanning (via sidekiq) that scale
- Seamless Vulnerability Management
- Track statistics and graph security trends in your applications
- Easily integrates with a variety of open source, commercial and custom scanning tools
31- Mageni
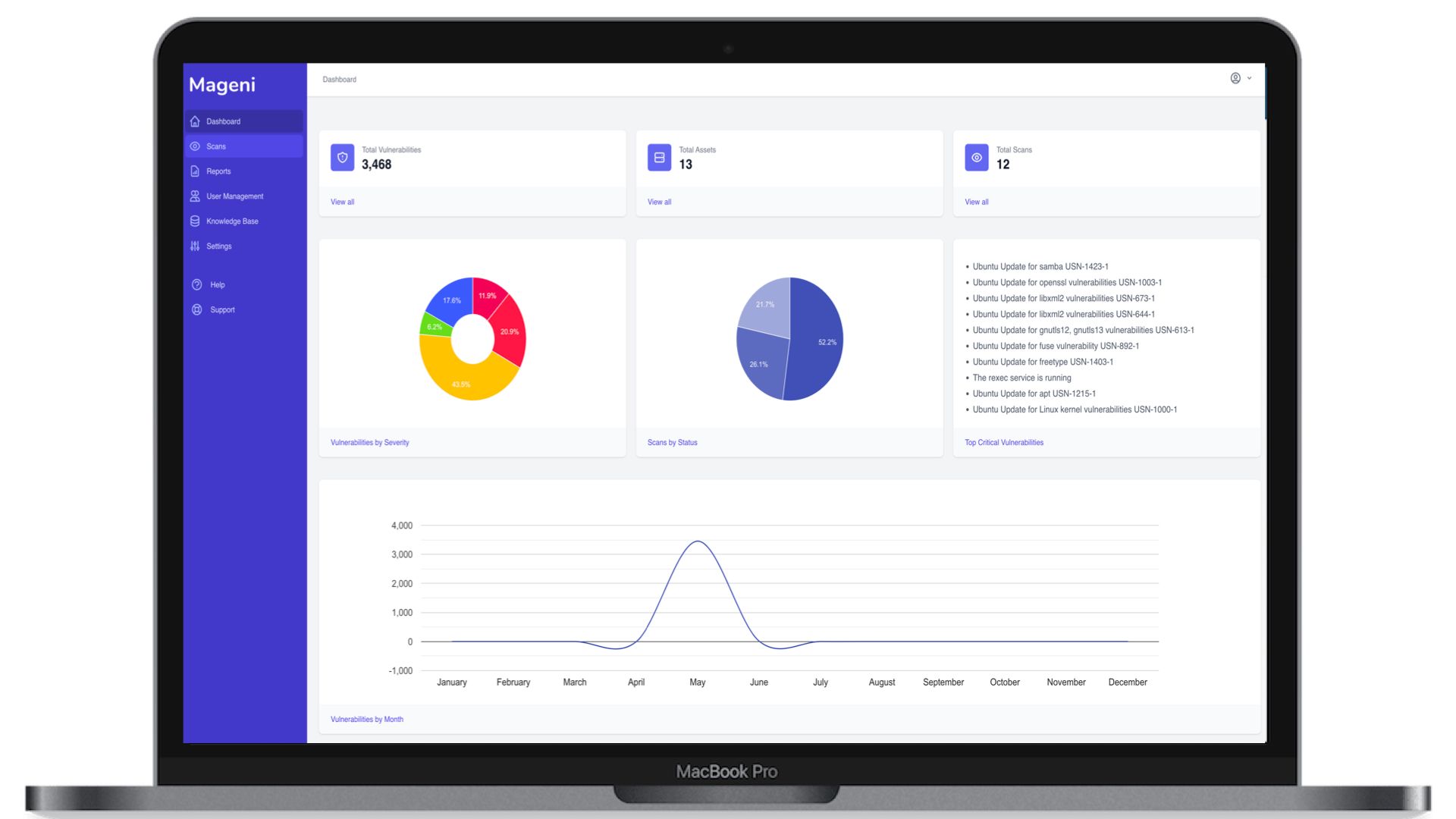
Mageni is a cross-platform, open-source vulnerability management platform that offers a range of features including assets, services, ports, applications, rogue device, and shadow IT discovery. It also provides vulnerability scanning, assessment, reporting, remediation, prioritization, and validation, as well as security audits, IoT, OT, and SCADA security testing, and hardening testing. It aids in addressing vulnerabilities for compliance with various standards like PCI DSS, NIST, HIPAA, ISO, NERC, FISMA, and NIS.
32- FazScan

FazScan is a Perl program designed for vulnerability scanning and pentesting, offering 18 options. These include various vulnerability scanners for SQL injection and common web vulnerabilities, automated CMS detectors and vulnerability scanners for multiple CMS platforms, an information gathering kit, a CloudFlare WAF protection bypasser, a dork scanner, an automated open port scanner, a denial of service attack feature, and an admin page detector.
33- Trivy
Trivy is a versatile security scanner that can scan a variety of targets, including container images, filesystems, git repositories, virtual machine images, Kubernetes, and AWS. It can detect issues such as OS packages and software dependencies in use, known vulnerabilities, IaC issues and misconfigurations, sensitive information and secrets, and software licenses. Trivy supports most popular programming languages, operating systems, and platforms.
34- Scanners Box

Scanners Box, also known as scanbox, stands as a formidable hacker toolkit, aggregating open source scanners from Github across more than 10 categories. This includes scanners for subdomains, databases, middleware and more, all with a modular design. However, it's worth noting that other renowned scanning tools like nmap, w3af, brakeman, arachni, nikto, metasploit, aircrack-ng are not included in our collection.
35- MagicRecon
MagicRecon is a shell script designed to streamline the process of data collection and vulnerability detection. It organizes results in various formats and directories, and its features include subdomain enumeration, live domain checking, whois and DNS information retrieval, technology extraction, certificate information, screenshot taking, email and user searching, public resource enumeration in AWS, Azure, and Google Cloud, GitHub Dorks information searching, robots.txt file entry checking, endpoint retrieving, parameter and port scanning, dirsearch, 403 HTTP status code bypass checking, massive recon and vulnerability scanning via Nuclei, and missing security header searching.
36- OSV-Scanner
OSV-Scanner is a tool that identifies vulnerabilities in a project's dependencies by connecting to the open-source OSV database. It offers advantages over closed-source databases and scanners, including advisories from open and authoritative sources, the ability for anyone to suggest improvements, and a machine-readable format that precisely maps onto a developer's list of packages.
37- Wapiti - Web Vulnerability Scanner
Wapiti is a Python-based web vulnerability scanner that supports various protocols and features. It operates as a "black-box" scanner, functioning like a fuzzer rather than studying source code. It scans web application pages, extracts links and forms, sends payloads, and looks for error messages or abnormal behaviors.

38- Collector
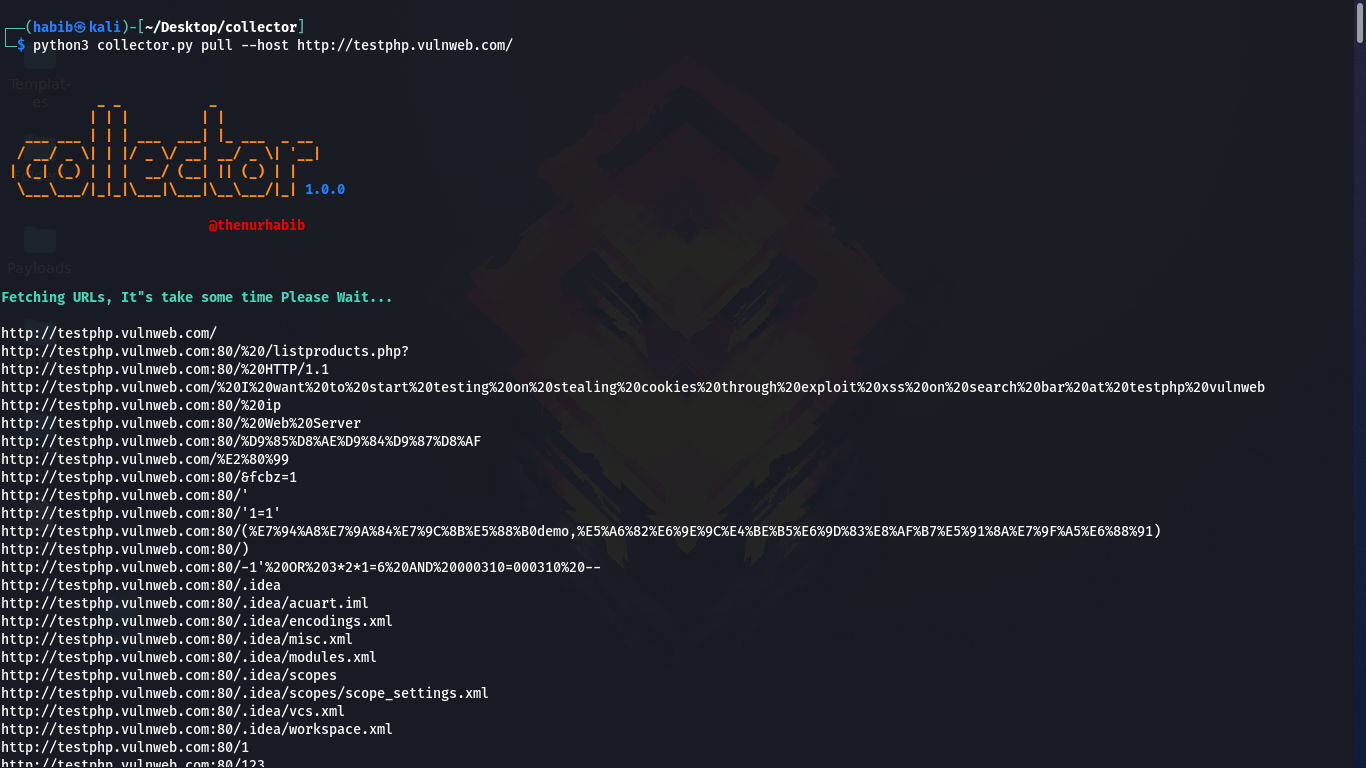
Collector is an intelligent automated tool that uses the Wayback Machine to find every vulnerable parameter. Its main features include finding XSS vulnerable parameters, crawling entire websites to collect every URL, advanced error handling, and collecting GET parameters.
39- Subdover
Subdover is a Python3-based, multithreaded subdomain takeover vulnerability scanner with over 88 fingerprints of potentially vulnerable services. It uses a CNAME record for verification and includes built-in subdomain enumeration and HTTP probing. Features include scanning from a subdomain list, testing single targets, customizable thread numbers, result saving in TXT format, clean output, OS independence, and an auto command line updater.
40- Tsunami
Tsunami is a versatile network security scanner that uses an extensible plugin system to detect high-risk vulnerabilities with high confidence. All publicly available Tsunami plugins are hosted in a separate repository.
41- Th3_Monster Tool 2.5
Th3_Monster Tool 2.5 ☣ is an open-source website vulnerability scanner and automatic exploitation bot ☣ .