Advanced Persistent Security Operating System For Security Researchers
Table of Content
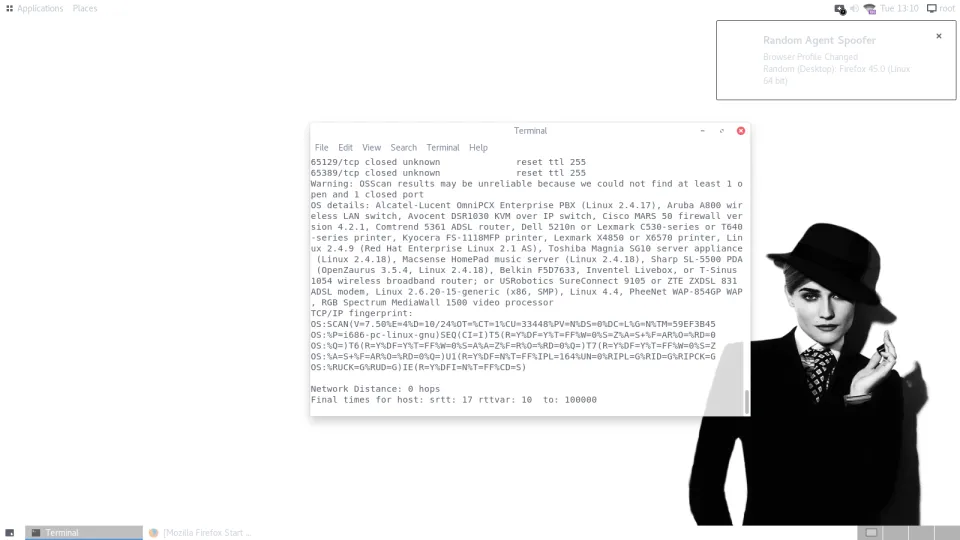
Advanced Persistent Security is an ISO system that is designed with integrated fingerprinting mechanisms to avoid detection and memory analysis.
It allows anonymous browsing, denies responses to servers, and prevents retrieval of information or forensic attempts by creating different identities. It also provides built-in security and protection against pings, scans, and tests.
Screenshots
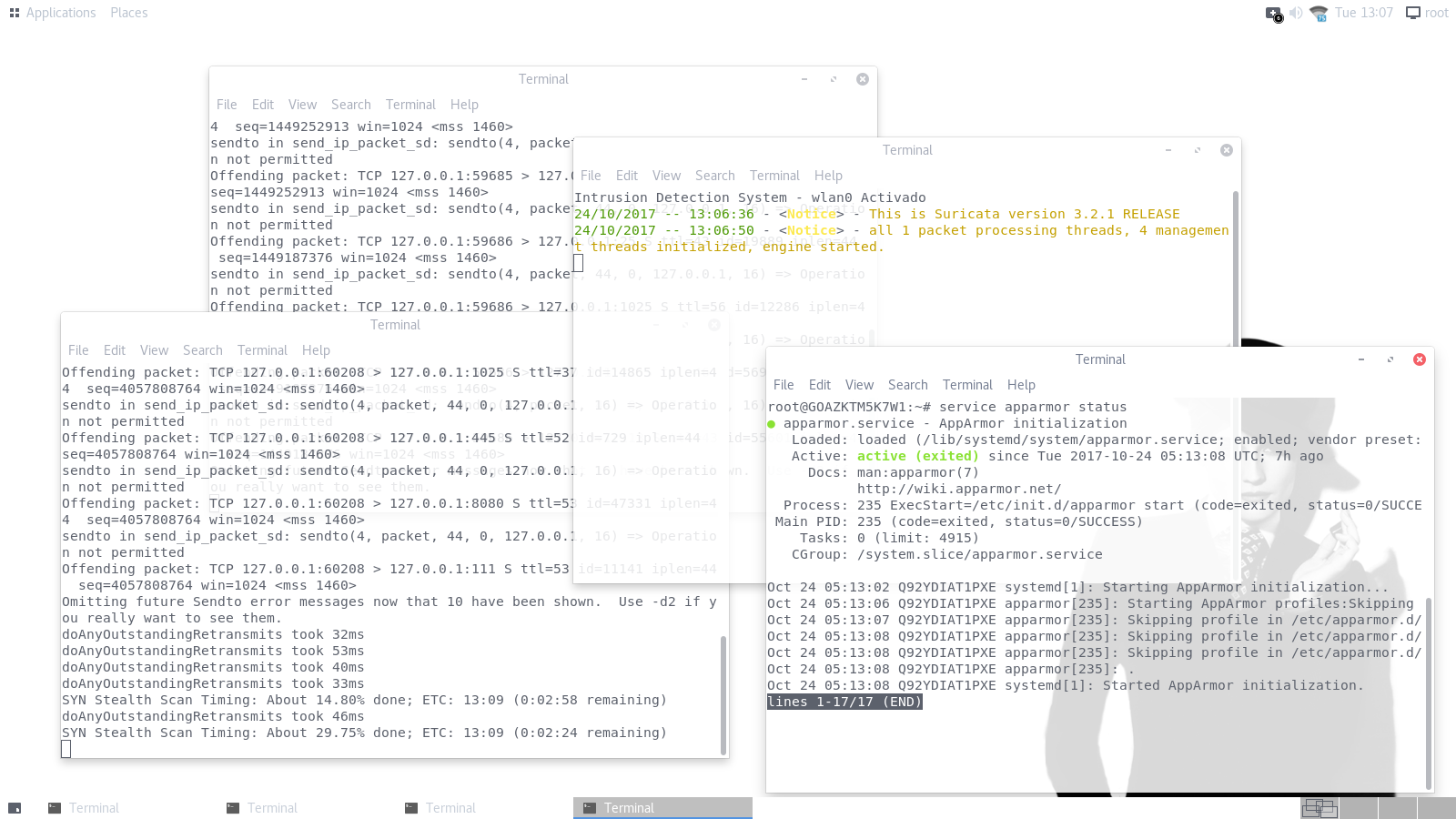
Features
- Anonymous Navigation
- Pegasus Malware Detection
- Hacking Team Malware Detection
- Analysis and Detection of other operating systems
- Custom Kernel
- Stable and Lightweight Distribution
- Live or Installation Mode
- Block Akamai Technologies
- Custom Theme
- Intrusion Detection System
- Memory Analysis Block
- Kernel-based Sdhash Prevention
- OS Hardening
- Block Cox Communications Inc
- Block Leaseweb USA, Inc
- Block Akamai International
- Block Nobis Technology Group
- Block Extraordinary Managed Service
- Block National Polytechnic Institute
- Block National Autonomous University of Mexico
- Block Secretary of Education and Technological Research
- Block Akamai Technologies, Inc
- Block INFOTEC
- Block Monterrey Institute of Technology and Higher Education
- Block Autonomous Technological Institute of Mexico
- Block ITESO
- Block Hewlett-Packard
- Block MCI Communications Services
- Block US Network Information Center - NSA
- Block Criminal Investigation Agency - PGR
- Block DigitalOcean
- Block Mexico Government IPS
- Block US Tor Nodes .edu
- Block United States Country
- Block United Kingdom Country
- Block IPS NSA / Abuse IP
- Block UK Tor Nodes - Trace
- Block Calyx Institute - Jabber
- Block .Us .Edu Tor Nodes / Exit Nodes
- Block United States Jabber / Server
- Block United States VPN Services
- Block CERT - Mx
- Block Google
- Block Facebook
- Block Israel Intelligence Attacks Method
- Block RSA
- Wipe Suite / DNS Suite / Kernel Suite
- Wipe Emergency Suite
- Persistent Protection
- Random OS Module
- ASRL Kernel Protection
- OS Fingerprinting Update
- Kernel Fingerprinting
- Hidden Kernel Headers
- Classic Gnome
- Tor Target Node
- United States Tor Block
- Automatic CVE Scanning
- Fake CPU Protections
- Random Hardware ID
- Tor Browser Fingerprinting
- Zero-day Tor Exploit Zerodium
- Easy Usage Hacker OS
- Sandbox
- IPSET Block UK, US Country
- IPSET Block Ireland, Australia, Canada Country
- Firewall Update
- Update Tor Security
- Maximum Security / Persistence
- Paranoic Activity - Clean OS permanent Wipes
- Panic Module to Prevent USB Attacks
- Block Hurricane Electric, Inc.
- IPSET Block New Zealand Country
- Block Tor Edu Nodes
- Block Protonmail
- Block NSA Surveillance
- Camouflage Activity
- Block Riseup
- APT Security Module
- Wipe USB
- Hardware Isolation / hwdb
- Evation Network Investigative Technique / NIT
- Block Attacks Against Tor
- Block Wireshark
- Evation / Computer Aided Investigative | CAINE
- Evation / Digital Forensics
- Block / SANS Investigative Forensic Toolkit
- IPSET Block Germany Country
- Double Sandbox
- Sandbox All Systems