Artificial Intelligence (AI)
The AI Showdown: ChatRTX vs. ChatGPT – A Doctor’s Perspective as a Software Engineer
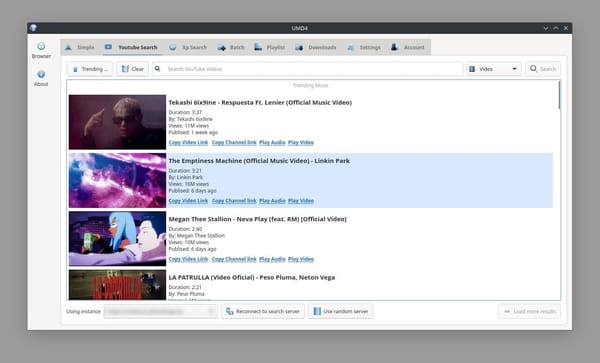
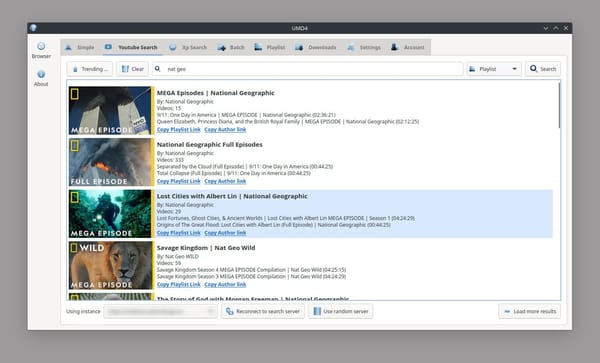
As a doctor who also work as a software engineer, I’ve always been fascinated by the intersection of technology and healthcare. Recently, some of my regular clients—ranging from fellow doctors to tech enthusiasts—asked me to dive into the world of AI and compare the new competitors to