Android
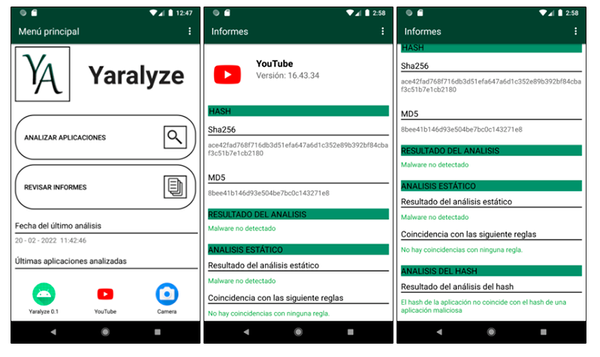
Yaralyze - Free malware detection Tool for Android Devices
Yaralyze is an malware detection tool for Android that relies on two types of static analysis, Yara rule analysis and hashes analysis.

Android
Yaralyze is an malware detection tool for Android that relies on two types of static analysis, Yara rule analysis and hashes analysis.

Android
In today's digital landscape, securing your Android device is more important than ever. With reports revealing that 11 million devices have been infected with malicious bots , ensuring the safety of your smartphone is a priority. If you're concerned about the security of your Android device, look

GDPR
In recent years, many companies outside the EU, including Turkey, have been hit with significant fines for failing to comply with GDPR regulations. The GDPR doesn’t just apply to EU-based businesses but extends to any company that processes the personal data of EU citizens. This creates challenges for many
Arch Linux
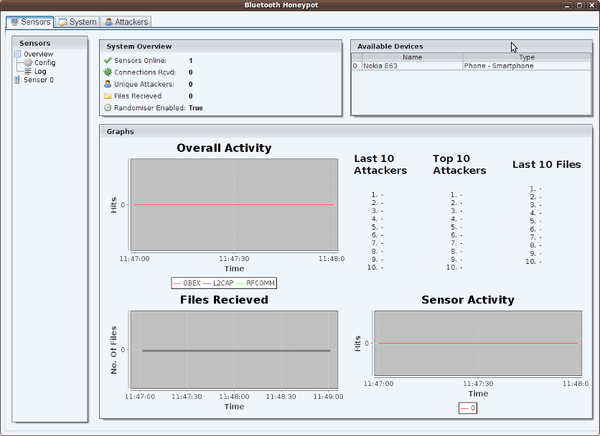
Bluepot is free and open-source Bluetooth honeypot framework designed for security research and penetration testing. It creates multiple virtual Bluetooth devices, simulating vulnerable endpoints to attract attackers. Pentesters and security researchers can use Bluepot to study and analyze Bluetooth-based attacks in a controlled environment, making it a valuable tool for
pentesting
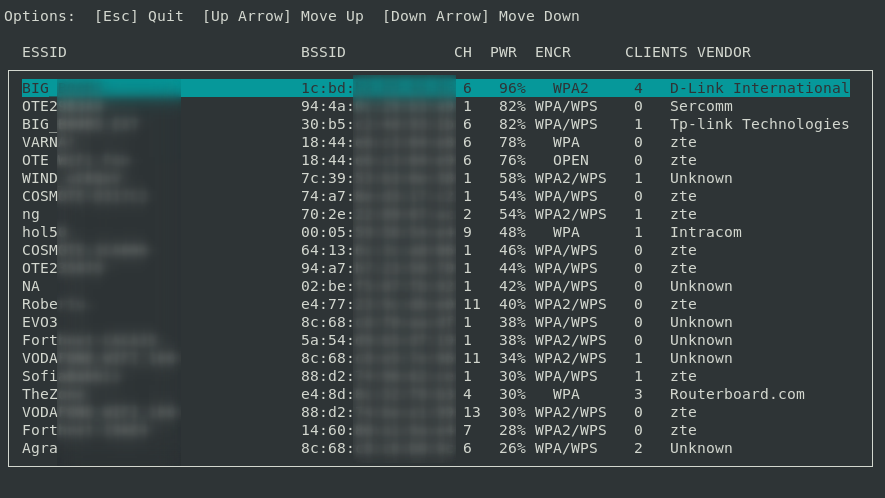
Wifiphisher is an advanced Wi-Fi security tool that automates phishing attacks against Wi-Fi networks to obtain credentials or infect devices with malware. It works by performing man-in-the-middle attacks by creating rogue access points, allowing attackers to capture credentials or deploy malware without needing brute-force methods. Wifiphisher is highly customizable and
Cybersecurity
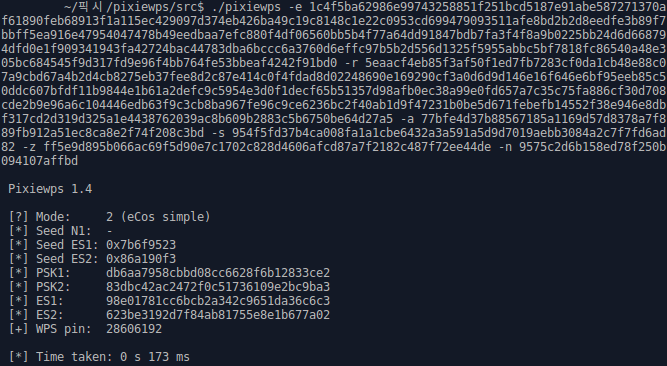
Pixiewps is an open-source tool written in C designed to perform offline brute-force attacks on WPS (Wi-Fi Protected Setup) PINs by exploiting vulnerabilities in some software implementations. It specifically leverages the "pixie-dust attack," a method discovered by Dominique Bongard in 2014. This attack takes advantage of weak or
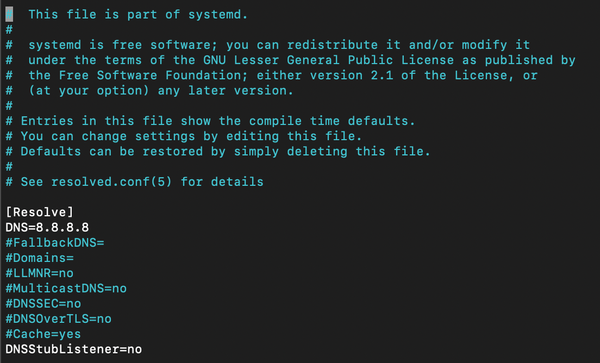
Cybersecurity
wifipumpkin3 is powerful framework for rogue access point attack, written in Python, that allow and offer to security researchers, red teamers and reverse engineers to mount a wireless network to conduct a man-in-the-middle attack. Features * Rogue access point attack * Man-in-the-middle attack * Module for deauthentication attack * Module for extra-captiveflask templates * Rogue

Cybersecurity
We've all been there—sipping on that overpriced coffee in a café, casually scrolling through emails, maybe even doing some online shopping (because why not?). All thanks to the glorious, "free" WiFi. But here's the catch: that free WiFi comes at a cost—your

Opinions
In a world where simplicity seems to be taking a backseat, we’re bombarded with a plethora of “smart” gadgets that make us wonder: Why complicate our lives when we could keep things easy? Not Everything Needs to Be Smart! Enough Smart Things, Keep it Simple - The Need to

Opinions
As a web developer, I often get asked about frameworks for building scalable, powerful applications. While Svelte has gained popularity for its simplicity, I wouldn't recommend it for large-scale projects. The Svelte Appeal: A Double-Edged Sword Svelte positions itself as a revolutionary framework, promising a streamlined experience that
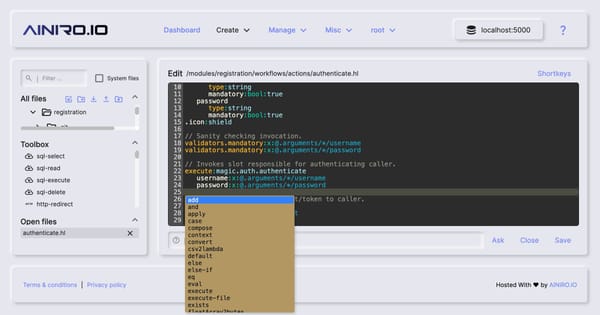
News
Magic is an AI-based low-code and no-code software development automation framework. Originally designed to empower developers by automating repetitive tasks, Magic uses artificial intelligence to streamline backend development, particularly for database-driven applications. The framework allows users to build scalable applications with minimal code, supporting both front-end and back-end automation. However,
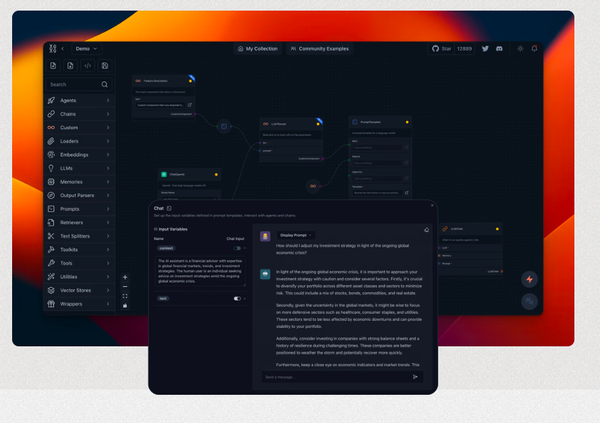
LLM
Langflow is a low-code app builder for RAG and multi-agent AI applications. It’s Python-based and agnostic to any model, API, or database.

Artificial Intelligence (AI)
Ludwig is a self-hosted open-source low-code framework for building custom AI models like LLMs and other deep neural networks. Features 1- 🛠 Build custom models with ease A declarative YAML configuration file is all you need to train a state-of-the-art LLM on your data. Support for multi-task and multi-modality learning. Comprehensive

programming
If you’ve ever stepped into a corporate IT meeting, you've probably heard executives chanting, "Java this" or "NET that," as if they're ordering a combo meal from the Enterprise Fast Food Drive-thru. And why not? Java and .NET are the comfort

GDPR
Ensuring user privacy and data protection is more important than ever, especially for websites operating within the European Union (EU). The General Data Protection Regulation (GDPR), which came into effect in May 2018, is designed to protect the personal data and privacy of EU citizens. One of its key components

Opinions
As we live in a world where everything is “smart.” Smart toasters, smart mirrors, smart water bottles—because apparently, we need a reminder to drink water. But just when you thought the tech world couldn’t get any more absurd, along comes the Smart Potty Training App. Yes, you read

Opinions
We live in an era where everything, from your toothbrush to your trash can, is powered by Artificial Intelligence (AI). You might have heard the phrase “there’s an app for that,” but now it seems there’s a smart device for everything—whether it makes sense or not. In

News
Discord is a popular communication platform designed primarily for gamers, but it has expanded to serve various communities, including hobbyists, educators, and businesses. Launched in 2015, it allows users to create servers, engage in voice and video calls, and chat through text channels. With millions of active users worldwide, Discord

business
Boycotting Samsung: Corporate Greed and Its Toll on Humanity

News
Samsung Electronics Co. reported earnings and revenue that fell short of market expectations, raising uncertainty about the outlook for its core chip division. The world’s largest memory chip and smartphone maker reported preliminary operating profit of about 9.1 trillion won ($6.8 billion) for the quarter ended September,

Opinions
Smart technology is everywhere. It’s embedded in our homes, cars, workplaces, and even on our wrists. From smart toasters and watches to fitness trackers and voice-controlled assistants, we live in a world where convenience is king. But here’s the problem: the more dependent we become on this tech,

Cybersecurity
Airports are hubs of activity—people rushing to catch flights, grabbing quick coffee, or checking emails while waiting for their boarding calls. In the midst of all this, free public Wi-Fi seems like a gift. But here’s the thing: it's a hacker's playground. Without knowing
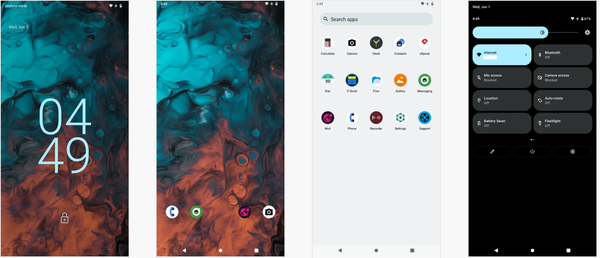
Android
DivestOS is more than just another Android-based operating system—it's a tool built for those who prioritize security and privacy above all else. Whether you're a privacy advocate, a professional working with sensitive data, or someone who values control over their device, DivestOS offers a highly

business
Freelancers, startups, as many professionals find themselves tethered to commercial apps and services. This reliance often leads to a phenomenon known as vendor lock-in, where users become dependent on a particular vendor's tools, making it challenging to switch to alternatives without incurring significant costs or disruptions. Understanding Vendor