Generate a Random HTTP Traffic Noise using Python - Web Traffic Obfuscation for Privacy Protection
Table of Content
Web traffic obfuscation is a privacy-enhancing technique that involves generating random internet traffic to mask a user's actual browsing patterns.
This approach is based on the principle of introducing "noise" into one's digital footprint, making it more challenging for third parties to accurately profile an individual's online behavior.
Why you may not to obfuscate your Traffic?
- Data collection: Various entities, including advertisers, ISPs, and data brokers, routinely collect and analyze web traffic data.
- Behavioral profiling: This collected data is often used to create detailed behavioral profiles of internet users.
- Privacy concerns: Such profiling raises significant privacy concerns, as it can reveal personal information, habits, and preferences.
- Obfuscation technique: Generating random HTTP requests and DNS queries creates a layer of meaningless data that obscures genuine browsing activity.
- Effectiveness: By introducing randomness, this method reduces the reliability and value of collected data for profiling purposes.
- Implementation: This can be achieved through custom scripts or specialized software that runs in the background during internet use.
- Limitations: While helpful, this technique is not foolproof and should be used in conjunction with other privacy measures for comprehensive protection.
- Ethical considerations: Users should be mindful of responsible implementation to avoid unnecessary strain on network resources.
This approach represents one of many strategies in the ongoing effort to maintain digital privacy in an era of pervasive data collection and analysis.
How It Works
- Random HTTP Requests: The script randomly selects URLs from a predefined list and sends HTTP requests using
curl. - Random DNS Queries: It performs DNS lookups for a set of dummy domains.
- Background Execution: Both functions run simultaneously in separate threads, continuously generating traffic.
Prerequisites
- Ensure you have Python installed (2.7 or 3.6+).
- Install required libraries:
pip install requests dnspython
Using the Script
- The script will start generating random HTTP requests and DNS queries.
- It will run continuously until you stop it.
- To stop the script, press Ctrl+C in the terminal.
Customization:
- You can modify the
DOMAINSlist to include or exclude specific websites. - Adjust the
time.sleep()values to change the frequency of requests. - Modify the number of concurrent threads by changing the
max_workersvalue inThreadPoolExecutor.
import random
import requests
import time
import dns.resolver
from concurrent.futures import ThreadPoolExecutor
# List of popular domains to query
DOMAINS = [
"google.com", "youtube.com", "facebook.com", "amazon.com", "wikipedia.org",
"twitter.com", "instagram.com", "linkedin.com", "reddit.com", "netflix.com"
]
def make_http_request(url):
try:
requests.get(f"http://{url}", timeout=5)
except requests.RequestException:
pass
def make_dns_query(domain):
try:
dns.resolver.resolve(domain, 'A')
except dns.exception.DNSException:
pass
def generate_traffic():
while True:
# Randomly choose between HTTP request and DNS query
if random.choice([True, False]):
url = random.choice(DOMAINS)
make_http_request(url)
else:
domain = random.choice(DOMAINS)
make_dns_query(domain)
# Sleep for a random interval between 1 and 5 seconds
time.sleep(random.uniform(1, 5))
if __name__ == "__main__":
print("Starting random traffic generation...")
print("Press Ctrl+C to stop.")
# Use ThreadPoolExecutor to run multiple requests concurrently
with ThreadPoolExecutor(max_workers=5) as executor:
try:
futures = [executor.submit(generate_traffic) for _ in range(5)]
# Wait for all futures to complete (which they won't, unless an exception occurs)
for future in futures:
future.result()
except KeyboardInterrupt:
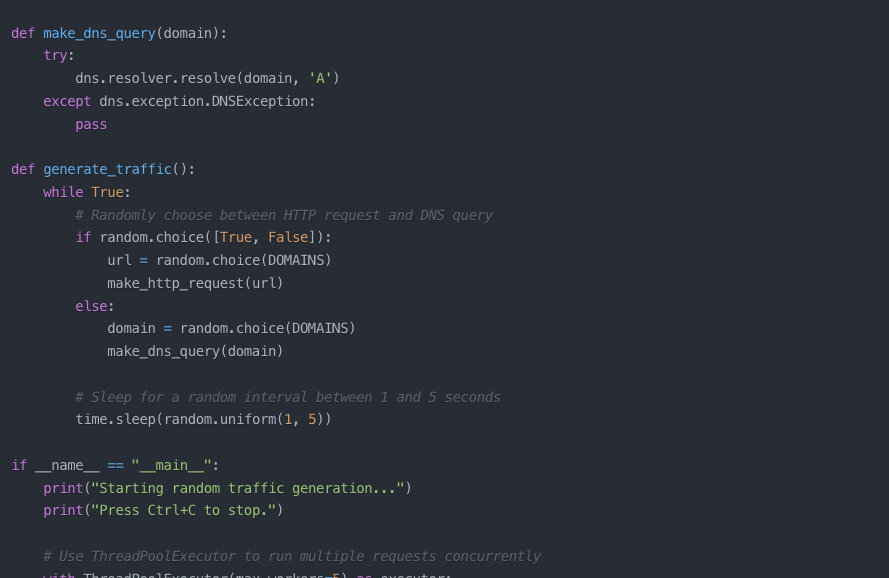
print("\nStopping traffic generation.")noise_generator.py
Compatibility
- This script should work on macOS, Ubuntu, Raspbian, and other Unix-like systems.
- For Windows users, you may need to install additional dependencies for DNS resolution.
Remember, while this script can help obfuscate your browsing patterns, it's not a comprehensive privacy solution. For better privacy, consider using VPNs, Tor, or other dedicated privacy tools alongside responsible browsing habits.
Generating random HTTP/DNS traffic can add a layer of obscurity to your online presence, making it harder for entities to build accurate behavioral profiles. This simple script demonstrates how you can quickly implement such noise generation on macOS, Ubuntu, and Raspbian systems.
With minimal code and dependencies, this solution is easy to deploy and can provide additional peace of mind when browsing the web.
Do not forget
- This script creates noise, not anonymity. Use it with additional tools like VPNs or Tor for more robust privacy.
- Monitor CPU usage, as generating continuous traffic can consume resources.
Important Notes:
- This script is for educational purposes and to demonstrate the concept of traffic obfuscation.
- Be aware that generating excessive traffic may violate your ISP's terms of service.
- Use responsibly and be mindful of the load you're putting on the servers you're querying.