Healthcare and Cyber Safety: Steps to Protect Your Personal Information
Table of Content
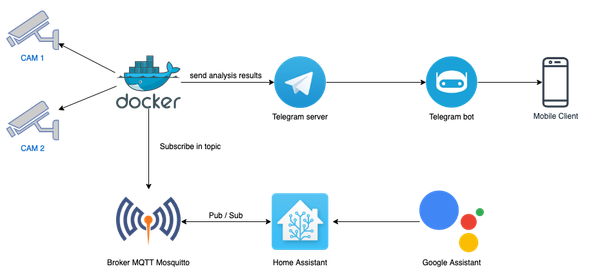
Healthcare providers store large amounts of sensitive data inside their records for every patient.
This includes medical histories, social security numbers, and insurance details. It's the personal information about every patient who visits the facility.
For the healthcare provider, this information is important. It allows better quality care but there's a 'con' to it - It also makes healthcare systems prime targets for cybercriminals.
Although protecting this data is a fundamental aspect of ensuring patient safety and maintaining trust, healthcare institutions are only able to do so much about security on their end.
Nowadays, everyone should be aware of the potential risks and therefore work on keeping their information secure on the individual level, as well.
Identity Theft in the Healthcare Sector
The rise of cybercrime in the healthcare sector has been alarming. The further we go into digitization of health records and the integration of IoT devices, the potential attack surface for cybercriminals will expand even more.
Hackers are developing sophisticated methods to breach healthcare and other systems. Their aim is to steal personal information for their financial gain or they aim just to cause widespread disruption.

The frequency and severity of cyber-attacks on healthcare organizations have also surged. This underscores the urgent need for more robust cybersecurity measures and diligence on the individual level of healthcare users.
Types of Cyber Risks
It's always a matter of confidentiality, integrity, and availability of patient data. And common threats include:
Ransomware Attacks - It's about different kinds of malicious software that encrypts data and demands a ransom for its release.
Phishing Scams - Phishing emails are deceptive emails or messages that trick individuals into revealing sensitive information.
Data Breaches - A data breach is any unauthorized access to sensitive data. This often results from the existing vulnerabilities in the system.
Malware - It's any software designed to disrupt or damage computer systems, or to gain unauthorized access to computer systems.
Insider Threats - The 'insiders' here are usually employees or associates who intentionally (or unintentionally!) cause data breaches.
Most Common Types of Identity Theft and Fraud
Healthcare users are vulnerable to several particular types of identity theft and fraud:
Medical Identity Theft - When someone uses another person's identity to obtain things, it's called identity theft. In the healthcare sector, the hackers aim to use another person's identity to obtain medical services, prescriptions, or insurance benefits.