13 Network Vulnerability Scanners and Pentesting Tools for Pentesting, Test Your Wifi Network Now
Table of Content
Pentesters, security researchers, and business owners must ensure the security of their Wi-Fi networks to protect sensitive data and prevent unauthorized access. Testing your network helps identify vulnerabilities that could be exploited by attackers, ensuring your system remains secure.
The Importance of Regular Wi-Fi and Network Security Testing for Business Owners
- Prevent Data Breaches: Protect sensitive company and customer information from unauthorized access and cyberattacks.
- Compliance with Regulations: Meet industry standards and legal requirements, such as GDPR or HIPAA, by ensuring secure networks.
- Mitigate Financial Loss: Avoid costly downtime, fines, and potential damage to your brand’s reputation by identifying vulnerabilities early.
- Safeguard Against Ransomware: Ensure your network is secure from malware and ransomware attacks that could cripple operations.
- Maintain Customer Trust: Strengthen security to assure customers their data is safe, fostering long-term loyalty.
With these 13 powerful vulnerability scanners and pentesting tools, you can effectively test and fortify your Wi-Fi network against potential threats.
1- Wifi-Hacking.py
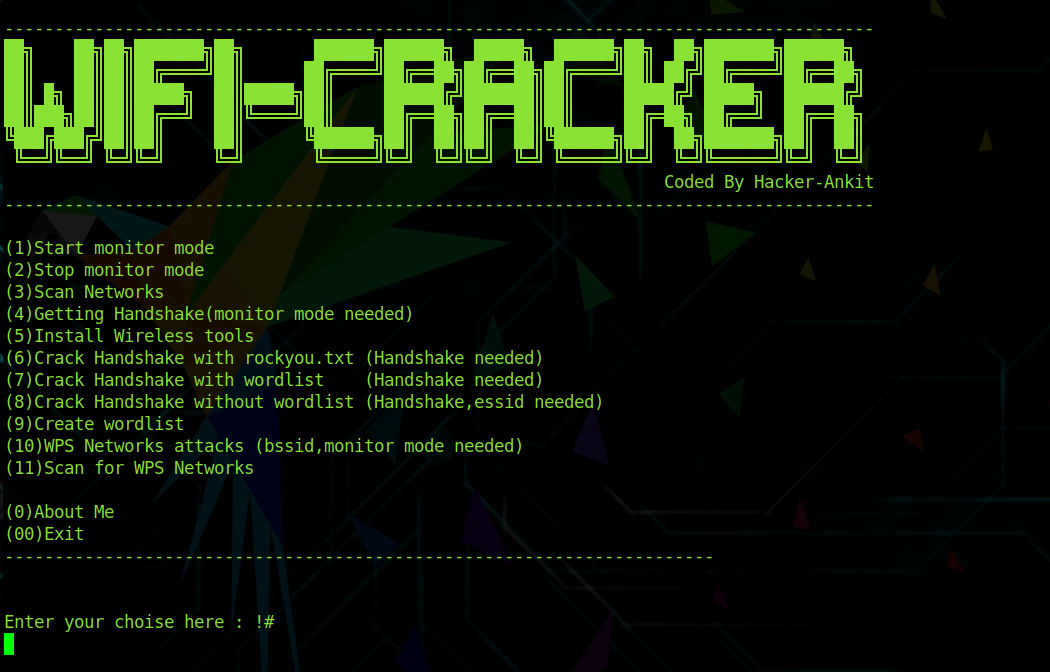
Wifi-Hacking.py is a free Python Tool For Hacking Wireless Connections Using Built-In Kali Tools. Supports All Securities (WEP, WPS, WPA, WPA2/TKIP/IES).
Its features include : WPS Networks attacks, WPS scanner, and Crack Handshake, Crack Handshake with and without wordlist.
The tool was tested on Kali Linux, BlackArch Linux, Ubuntu, Kali Nethunter, Termux (Rooted Devices), and Parrot OS.
2- WIFIPumpkin3
WiFiPumpkin3 is a powerful Python app for rogue access point attacks. It enables security researchers, red teamers, and reverse engineers to create a wireless network for conducting man-in-the-middle attacks.
Features Highlights
- Rogue access point attack
- Man-in-the-middle attack
- Module for deauthentication attack
- Module for extra-captiveflask templates
- Rogue Dns Server
- Captive portal attack (captiveflask)
- Intercept, inspect, modify and replay web traffic
- WiFi networks scanning
3- Mass Bruter
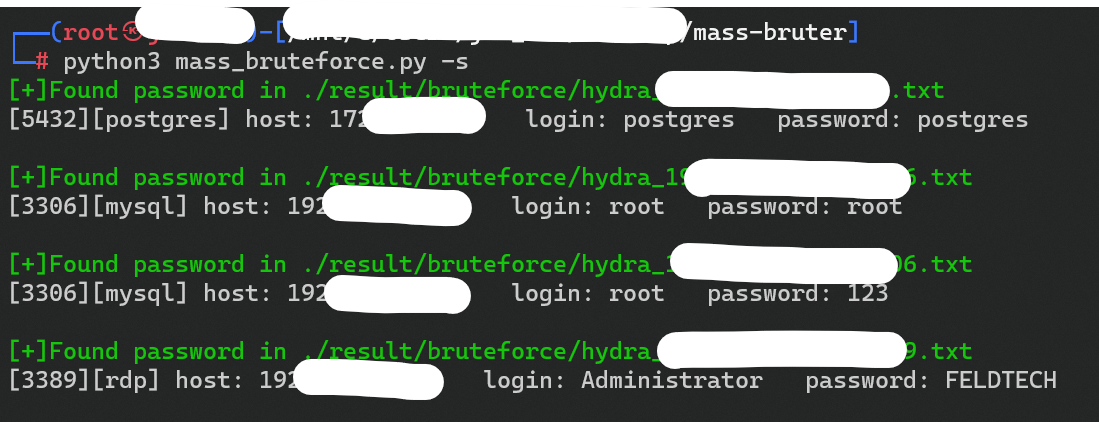
Yet another python tool that enables pentesters and security researchers test their networks using Mass bruteforce authentication.
4- Pentest Tools Framework (exploits, Scanner, Password.)
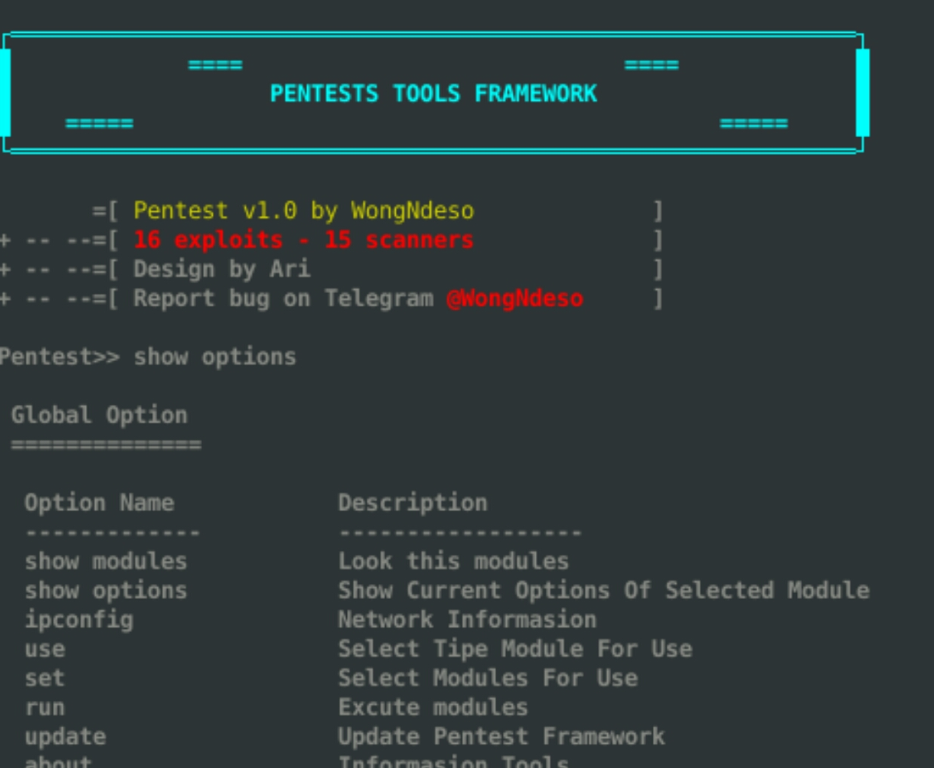
Pentest Tools Framework is a database of exploits, Scanners and tools for penetration testing. Pentest is a powerful framework includes a lot of tools for beginners. You can explore kernel vulnerabilities, network vulnerabilities
5- Pixiewps
Pixiewps is a tool written in C used to bruteforce offline the WPS PIN exploiting the low or non-existing entropy of some software implementations, the so-called "pixie-dust attack" discovered by Dominique Bongard in summer 2014.
6- Wifiphisher
Wifiphisher is a versatile rogue access point framework for red team engagements and Wi-Fi security testing, enabling man-in-the-middle attacks, phishing, and malware delivery, with support for various Wi-Fi association techniques and customizable modules.
7- Fluxion (KaliLinux Tool)
"Fluxion is the Future of MITM WPA Attacks" It is a remake by Mr. SAGE with less bugs and more functionality. It's compatible with the latest release of Kali (rolling). The attack is mostly manual, but experimental versions will automatically handle most functionality from the stable releases.
How does it work?
- Scan the networks.
- Capture a handshake (can't be used without a valid handshake, it's necessary to verify the password)
- Use WEB Interface
- Launch a FakeAP instance to imitate the original access point
- Spawns a MDK3 process, which deauthenticates all users connected to the target network, so they can be lured to connect to the FakeAP and enter the WPA password.
- A fake DNS server is launched in order to capture all DNS requests and redirect them to the host running the script
- A captive portal is launched in order to serve a page, which prompts the user to enter their WPA password
- Each submitted password is verified by the handshake captured earlier
- The attack will automatically terminate, as soon as a correct password is submitted..
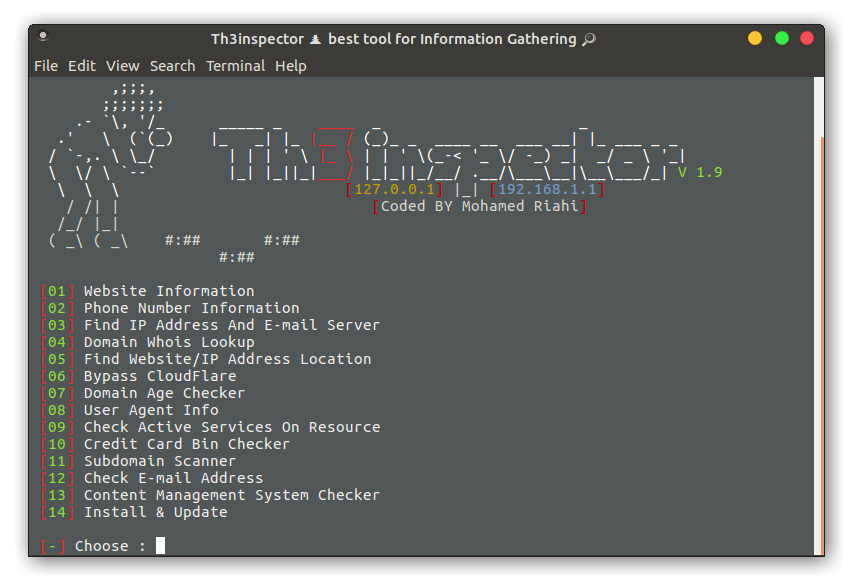
8- OWASP Nettacker
OWASP Nettacker is a powerful and automated security testing tool designed to scan, attack, and detect vulnerabilities in networks, services, and web applications. It offers multi-threaded scanning, network mapping, and supports a wide range of protocols.
Nettacker is highly efficient for security experts and pentesters looking for a comprehensive and customizable tool to identify weaknesses and improve network security.
It also offers an IoT Scanner that includes:
- Python Multi Thread & Multi Process Network Information Gathering Vulnerability Scanner
- Service and Device Detection ( SCADA, Restricted Areas, Routers, HTTP Servers, Logins and Authentications, None-Indexed HTTP, Paradox System, Cameras, Firewalls, UTM, WebMails, VPN, RDP, SSH, FTP, TELNET Services, Proxy Servers and Many Devices like Juniper, Cisco, Switches and many more… )
- Asset Discovery & Network Service Analysis
- Services Brute Force Testing
- Services Vulnerability Testing
- HTTP/HTTPS Crawling, Fuzzing, Information Gathering and …
- HTML, JSON, CSV and Text Outputs
- API & WebUI
9- Nuclei
Nuclei is used to send requests across targets based on a template, leading to zero false positives and providing fast scanning on a large number of hosts. Nuclei offers scanning for a variety of protocols, including TCP, DNS, HTTP, SSL, File, Whois, Websocket, Headless, Code etc.
With powerful and flexible templating, Nuclei can be used to model all kinds of security checks.
10- FluxER
FluxER - The bash script which installs and runs the Fluxion tool inside Termux. The wireless security auditing tool used to perform attacks such as WPA/WPA2 cracking and MITM attacks.
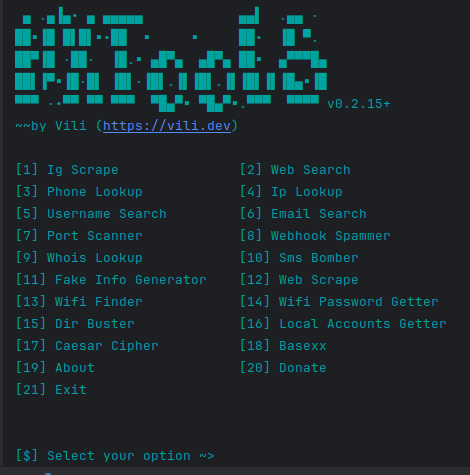
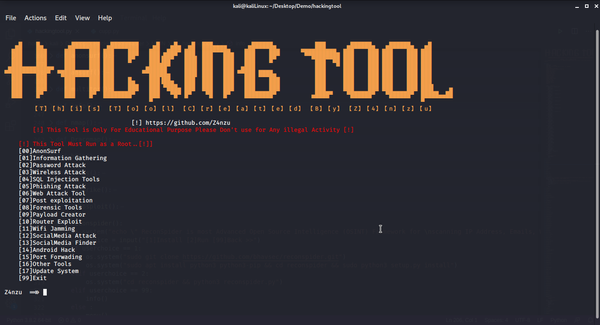
11- All in One Hacking tool For Hackers🥇
HackingTool is an all-in-one popular toolkit for hackers, pentesters, and security experts, offering a vast range of tools for network scanning, information gathering, vulnerability scanning, and password cracking. It streamlines the entire security testing process, from reconnaissance to exploitation, all in one interface.
With tools like Nmap, Metasploit, and Aircrack-ng, it's ideal for both beginners and advanced users.
12- Fakeap
Fakeap is a script to perform Evil Twin Attack, by getting credentials using a Fake page and Fake Access Point
13- Wifite2
Wifite2 is the modern version of the original Wifite, a powerful, automated tool designed for auditing and attacking wireless networks. It focuses on ease of use and supports a wide range of Wi-Fi attack methods, including WPA handshake capture and WPS attacks. Wifite2 is optimized for the latest wireless vulnerabilities and can automatically target multiple networks in one run.
The original Wifite was widely used for Wi-Fi hacking due to its automation of complex attacks. However, Wifite2 enhances this legacy by adding support for updated protocols and faster, more efficient attacks, making it a go-to for modern wireless security testing.