12 Cutting-Edge Docker-Based Vulnerability Scanners for Cybersecurity Professionals and Pentesters
Table of Content
In the ever-evolving landscape of cybersecurity, professionals face an increasing number of threats that require robust solutions. Offensive Security practices play a crucial role in identifying and mitigating vulnerabilities before they can be exploited.
Docker, a powerful containerization platform, has emerged as a favorite among cybersecurity experts for its ability to create isolated environments for testing and deployment. With tools designed specifically for vulnerability assessment, Docker managers enable security teams to efficiently deploy and manage their scanning tools.
In this article, we will explore 12 cutting-edge Docker-based vulnerability scanners that empower pentesters and security professionals to uncover weaknesses in their environments.

From automated scanning to real-time reporting, these tools are indispensable for anyone serious about fortifying their cybersecurity posture.
Join us as we dive into the world of vulnerability scanning and discover how these innovative solutions can enhance your security practices.
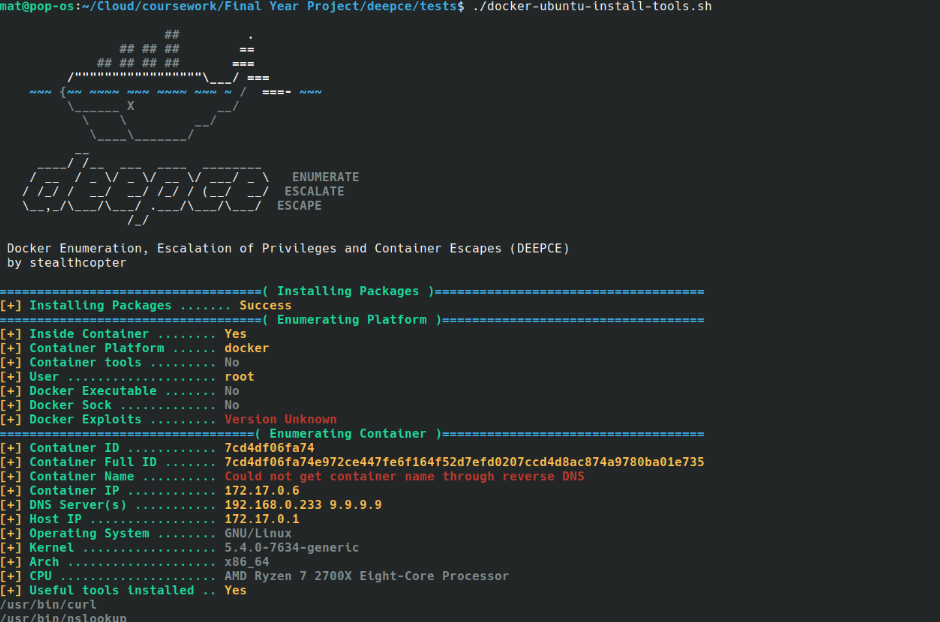
1- Offensive Docker
Offensive Docker is an image with the more used tools to create an pentest environment easily and quickly.
Features
- OS, networking, developing and pentesting tools installed.
- Dozens of network and port scanners
- Connection to HTB (Hack the Box) vpn to access HTB machines.
- Popular wordlists installed: SecLists, dirb, dirbuster, fuzzdb, wfuzz and rockyou.
- DNS Lookup tools
- Web Scanning
- CMS vulnerability scanners for WordPress, Joomla, and more
- Proxy service to send traffic from any browsers and burp suite installed in your local directory.
- Brute Force attack
- Exploit database installed.
- Tool for cracking password.
- Linux enumeration tools installed.
- Tools installed to discovery services running.
- Tools installed to directory fuzzing.
- Monitor for linux processes without root permissions
- Zsh shell installed.
- Built-in developer tool installed
- Web crawlers
- Fuzzer search
- APK tools
- Metasploit
2- NIGHTINGALE
Nightingale is an open-source docker package designed for testing, pentesting and developing APIs. It offers a user-friendly interface for managing API requests, making it easier for developers to interact with APIs during development and debugging.
Nightingale supports a range of protocols, including HTTP and WebSockets, and enables users to quickly build, test, and document APIs.
This tool is ideal for developers working with APIs, offering efficiency and ease of use during the testing phase of their projects.
3- DockerSecurityPlayground
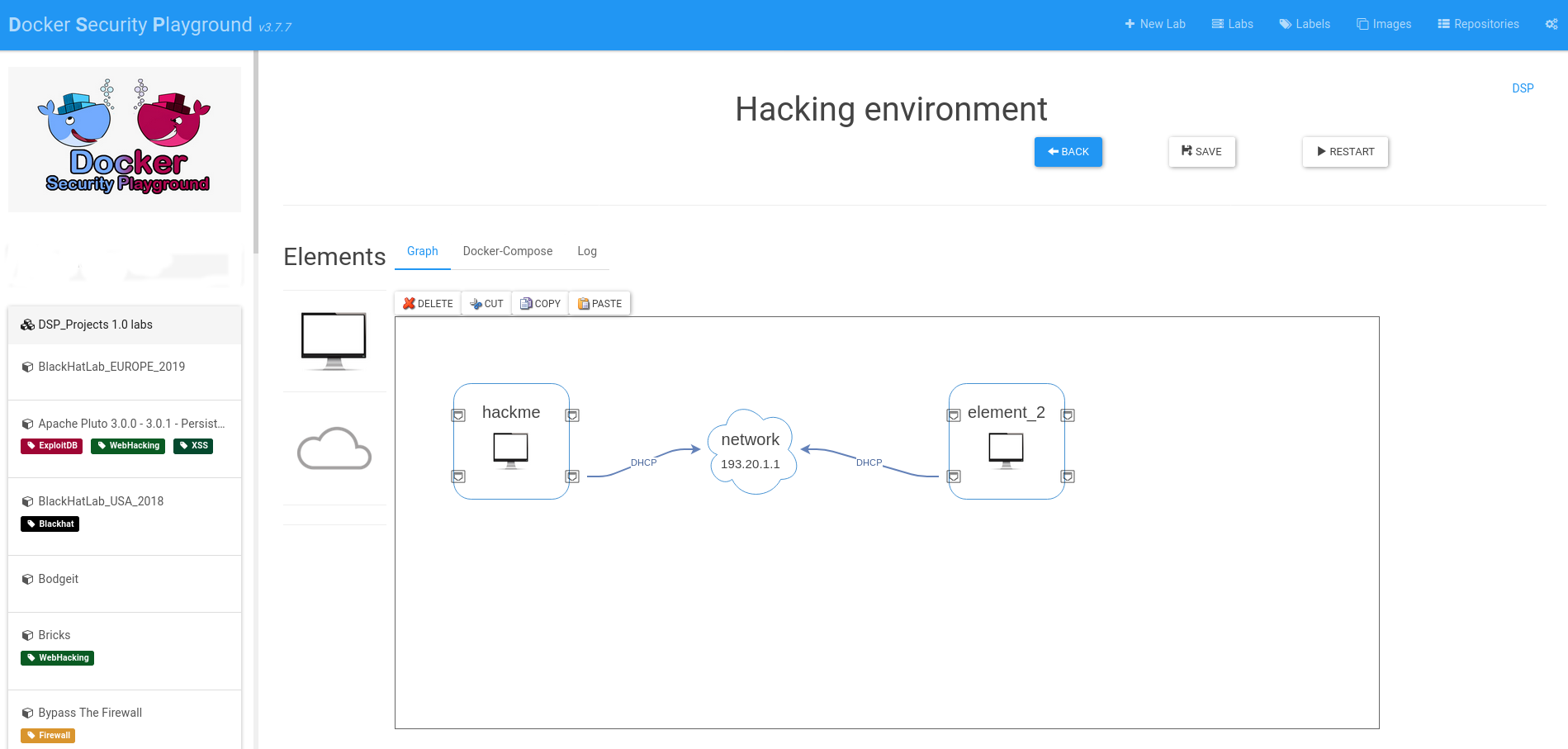
Docker Security Playground (DSP) is an open-source Microservices-based framework designed for simulating and testing security scenarios using Docker containers.
It provides a virtual environment where users can create and explore complex network topologies, simulate attacks, and test security measures in an isolated environment.
DSP is perfect for security professionals, researchers, and students looking to practice ethical hacking, penetration testing, and security auditing.
4- Automated Pentest
This open-source project provides a minimal Docker container based on Parrot OS, specifically designed for running automated security scans and penetration testing reports.
This Docker container integrates over 20 essential modules, making it a versatile tool for security assessments and auditing. It simplifies the process of conducting thorough pentests by automating the use of multiple tools within one unified environment.
Features included:
- Whois Domain Analyzer: Extracts domain registration information.
- Nslookup: Queries DNS records for IP and domain details.
- Nmap: Network discovery and security auditing.
- Uniscan: Web vulnerability scanner.
- TheHarvester: Gathers emails, subdomains, hosts, and employee names.
- Metagoofil: Extracts metadata from public documents.
- Dirb: Brute-force web directory scanning.
- DNSRecon: DNS enumeration.
- DNSmap: Subdomain brute-forcing.
- Wafw00f: Web application firewall detection.
- Nikto: Web server vulnerability scanner.
- XssPy: XSS vulnerability detection.
- XSStrike: Advanced XSS detection.
- WhatWeb: Web technology fingerprinting.
- Wapiti: Web vulnerability scanner.
- WPScan: WordPress vulnerability scanner.
- Joomscan: Joomla vulnerability detection.
- Droopescan: CMS vulnerability scanning (WordPress, Joomla, Silverstripe, Drupal, Moodle).
- SSLScan: SSL certificate analysis.
- SSLyze: SSL/TLS configuration testing.
- A2SV: Automated SSL vulnerability testing.
- WFuzz: Web fuzzing for vulnerabilities.
5- Aria Cloud Penetration Testing Tools Container - KaliLinux Packages as Docker Image
Aria Cloud is an open-source project that provides a simple cloud-based download manager powered by Aria2. It allows users to manage and monitor their downloads remotely through an easy-to-use web interface.
AriaCloud is perfect for users looking for a lightweight, remote-controlled download manager with broad protocol support.
Key Features:
- Web Interface: Manage and monitor downloads via an intuitive browser-based interface.
- Aria2 Integration: Supports multiple protocols for efficient downloading.
- Remote Access: Control downloads remotely from any device.
- Multiple Downloads: Handle several downloads simultaneously.
- Queue Management: Organize and prioritize downloads efficiently.
6- Docker Images for Penetration Testing and Cybersecurity
Docker Security Images by Ellerbrock provides a collection of Docker images focused on enhancing security testing and learning. These images are designed to help security professionals and developers practice, test, and improve their security skills.
The repository includes images for vulnerability scanning, penetration testing, and auditing, making it a valuable resource for anyone interested in cybersecurity and secure software development.
7- Docker for Network Penetration testing
BNPT_Docker is a Docker-based automated penetration testing tool by BriskInfosec. It simplifies network and web application security assessments with integrated modules for scanning and testing, streamlining the vulnerability identification process.
It also includes the Rebel framework, which is created with a collection of modules that provide additional benefits for penetration testing. Moreover, Raccoon-Scanner, an offensive security tool for reconnaissance and vulnerability scanning, is also part of the toolkit.
- Nmap – Network discovery and security auditing tool.
- Metasploit – Penetration testing framework.
- WPScan – WordPress vulnerability scanner.
- Nikto – Web server scanner.
- Gobuster – Directory and file brute-forcing tool.
- SQLMap – Automatic SQL injection tool.
- Rebel Framework – Collection of penetration testing modules.
- Raccoon-Scanner – Reconnaissance and vulnerability scanning tool.
- Sublist3r – Subdomain enumeration tool.
- TheHarvester – Information gathering tool for email, subdomains, IPs.
- Dirb – Directory brute-forcing tool.
- Arachni – Web application security scanner.

8- Pentest Docker Step-By-Step
Pentest-In-Docker is an open-source project by Swordfish Security that provides a set of Docker containers for penetration testing.
It includes a pre-configured environment with various tools for security assessments, making it easier for professionals to conduct penetration tests without needing to set up complex environments.
9- vulhub-lab
This Docker Compose setup enables users to quickly create a dedicated security testing and research environment. It facilitates the establishment of a network where containers can be accessed via their hostnames, allowing for multiple containers to listen on the same port without port mapping conflicts.
Pentesters can easily add, delete, or update vulnerable containers to suit their specific requirements.
10- Local PentestLab Management Script
PentestLab is a Docker-based framework designed to simplify the creation of a penetration testing lab environment.
It allows users to quickly deploy various vulnerable applications and services in isolated containers for security testing and practice
11- Web Hacking ToolKit
The Web Hacking Toolkit is a Docker container designed for web application security testing. It provides a comprehensive set of tools and utilities for penetration testers to analyze, exploit, and secure web applications.
Users can easily deploy the toolkit in a containerized environment, allowing for efficient testing without the need for extensive setup.
The toolkit includes various scripts and tools to facilitate common web hacking tasks, making it a valuable resource for security professionals.

12- HuntKit