Pixiewps - Free App that Enables you to Test Your Wifi WPS PIN Security
Table of Content
Pixiewps is an open-source tool written in C designed to perform offline brute-force attacks on WPS (Wi-Fi Protected Setup) PINs by exploiting vulnerabilities in some software implementations.
It specifically leverages the "pixie-dust attack," a method discovered by Dominique Bongard in 2014.
This attack takes advantage of weak or non-existent entropy in the generation of WPS PINs, allowing Pixiewps to recover the PIN in seconds or minutes, much faster than traditional online brute-force methods like Reaver or Bully, which take hours.
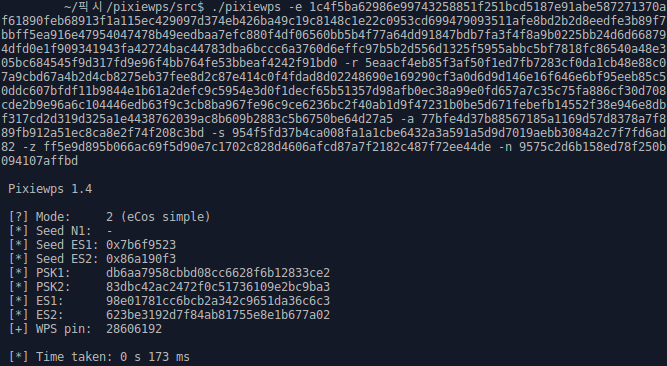
Starting from version 1.4, Pixiewps has enhanced functionality, allowing it to recover the WPA-PSK (Wi-Fi Protected Access Pre-Shared Key) from a passive capture (messages M1 through M7) for certain vulnerable devices.
This tool is designed for educational and security testing purposes only, highlighting weaknesses in wireless security implementations.
For Educational Purpose
Pixiewps is mainly intended for educational and security testing purposes, to identify and demonstrate weaknesses in wireless security implementations.
Features
The Pixiewps tool, available at GitHub, offers a range of features that make it an efficient tool for testing vulnerabilities in Wi-Fi Protected Setup (WPS) PIN implementations. Below are the key features of Pixiewps:
Pixie-Dust Attack Implementation:
Pixiewps performs an offline brute-force attack known as the "pixie-dust attack," which exploits low or non-existent entropy in some WPS PIN generation methods. This allows for fast recovery of WPS PINs.
Speed:
Unlike traditional online brute-force methods, Pixiewps can recover vulnerable WPS PINs in a matter of seconds or minutes, depending on the target's vulnerability.
Works with Captured Handshakes:
Starting from version 1.4, Pixiewps can also recover the WPA-PSK (Pre-Shared Key) by analyzing a passive capture of WPS messages (M1 through M7) from certain devices, allowing for a complete passive attack without interacting with the target.
Support for Multiple WPS Modes:
Pixiewps supports different modes of WPS operation, particularly focusing on vulnerable implementations that use --mode 3, where the attack is especially effective.
Command-Line Tool:
The tool is lightweight and runs from the command line, making it highly customizable and scriptable for users who are testing Wi-Fi security.
Compatibility with Reaver:
Pixiewps can be integrated with other tools like Reaver, which is commonly used for online brute-force attacks, providing a comprehensive approach to testing WPS security vulnerabilities.
Supported Platforms
- Linux: Ubuntu, Fedora, Linux Mint, Arch Linux
License
The project is released under the The GNU General Public License.