reNgine is an open-source Security Recon Framwork for Web Apps
Are You Truly Ready to Put Your Mobile or Web App to the Test?
Don`t just assume your app works—ensure it`s flawless, secure, and user-friendly with expert testing. 🚀
Why Third-Party Testing is Essential for Your Application and Website?We are ready to test, evaluate and report your app, ERP system, or customer/ patients workflow
With a detailed report about all findings
Contact us nowTable of Content
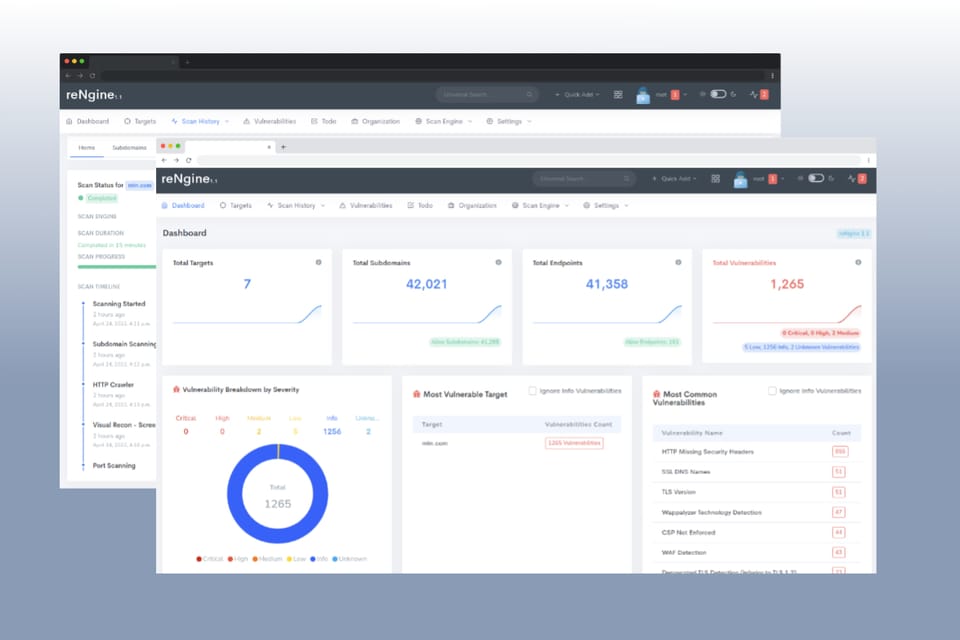
reNgine is an automated reconnaissance framework for web applications with a focus on highly configurable streamlined recon process via Engines, recon data correlation and organization, continuous monitoring, backed by a database, and simple yet intuitive User Interface.
reNgine is your go-to web application reconnaissance suite that's designed to simplify and streamline the reconnaissance process for security professionals, penetration testers, and bug bounty hunters. With its highly configurable engines, data correlation capabilities, continuous monitoring, database-backed reconnaissance data, and an intuitive user interface, reNgine redefines how you gather critical information about your target web applications.
The Problem
Traditional reconnaissance tools often fall short in terms of configurability and efficiency. reNgine addresses these shortcomings and emerges as a excellent alternative to existing commercial tools.
The Solution
reNgine was created to address the limitations of traditional reconnaissance tools and provide a better alternative, even surpassing some commercial offerings. Whether you're a bug bounty hunter, a penetration tester, or a corporate security team, reNgine is your go-to solution for automating and enhancing your information-gathering efforts.
Features
- Reconnaissance:
- Subdomain Discovery
- IP and Open Ports Identification
- Endpoints Discovery
- Directory/Files fuzzing
- Screenshot Gathering
- Vulnerability Scan
- Nuclei
- Dalfox XSS Scanner
- CRLFuzzer
- Misconfigured S3 Scanner
- WHOIS Identification
- WAF Detection
- OSINT Capabilities
- Meta info Gathering
- Employees Gathering
- Email Address gathering
- Google Dorking for sensitive info and urls
- Projects, create distinct project spaces, each tailored to a specific purpose, such as personal bug bounty hunting, client engagements, or any other specialized recon task.
- Perform Advanced Query lookup using natural language alike and, or, not operations
- Highly configurable YAML-based Scan Engines
- Support for Parallel Scans
- Support for Subscans
- Recon Data visualization
- GPT Vulnerability Description, Impact and Remediation generation
- GPT Attack Surface Generator
- Multiple Roles and Permissions to cater a team's need
- Customizable Alerts/Notifications on Slack, Discord, and Telegram
- Automatically report Vulnerabilities to HackerOne
- Recon Notes and Todos
- Clocked Scans (Run reconnaissance exactly at X Hours and Y minutes) and Periodic Scans (Runs reconnaissance every X minutes/- hours/days/week)
- Proxy Support
- Screenshot Gallery with Filters
- Powerful recon data filtering with autosuggestions
- Recon Data changes, find new/removed subdomains/endpoints
- Tag targets into the Organization
- Smart Duplicate endpoint removal based on page title and content length to cleanup the reconnaissance data
- Identify Interesting Subdomains
- Custom GF patterns and custom Nuclei Templates
- Edit tool-related configuration files (Nuclei, Subfinder, Naabu, amass)
- Add external tools from Github/Go
- Interoperable with other tools, Import/Export Subdomains/Endpoints
- Import Targets via IP and/or CIDRs
- Report Generation
- Toolbox: Comes bundled with most commonly used tools during penetration testing such as whois lookup, CMS detector, CVE lookup, etc.
- Identification of related domains and related TLDs for targets
- Find actionable insights such as Most Common Vulnerability, Most Common CVE ID, Most Vulnerable Target/Subdomain, etc.
License
Distributed under the GNU GPL v3 License
Resources & Downloads