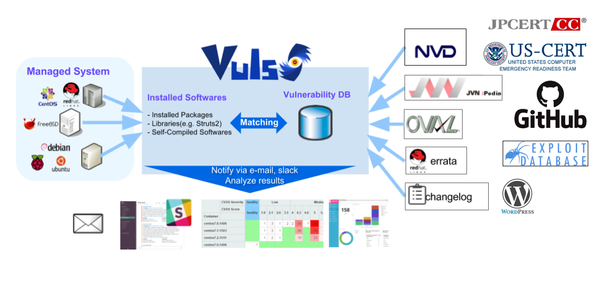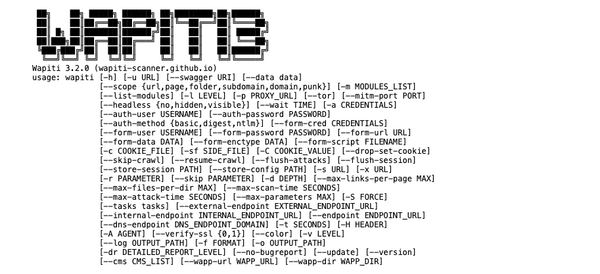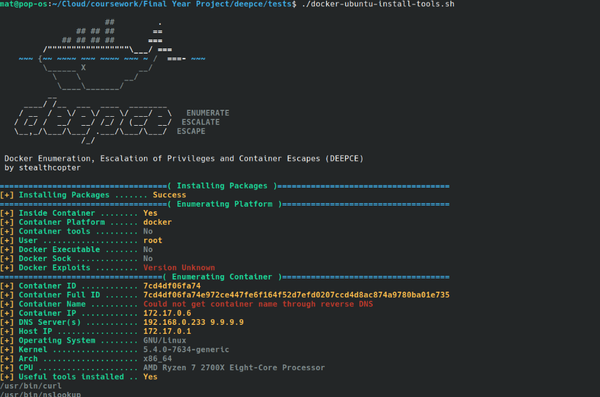
CCTV
12 Free Open-source NVR CCTV Solutions for Windows Systems
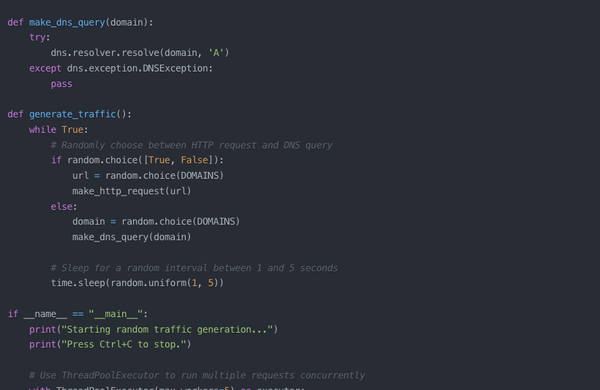
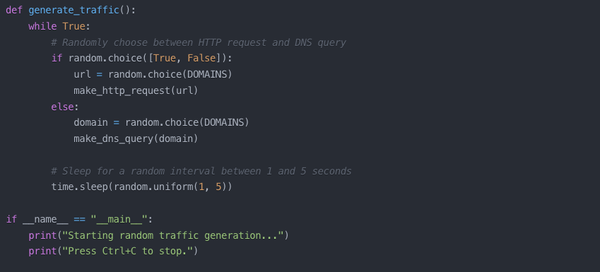
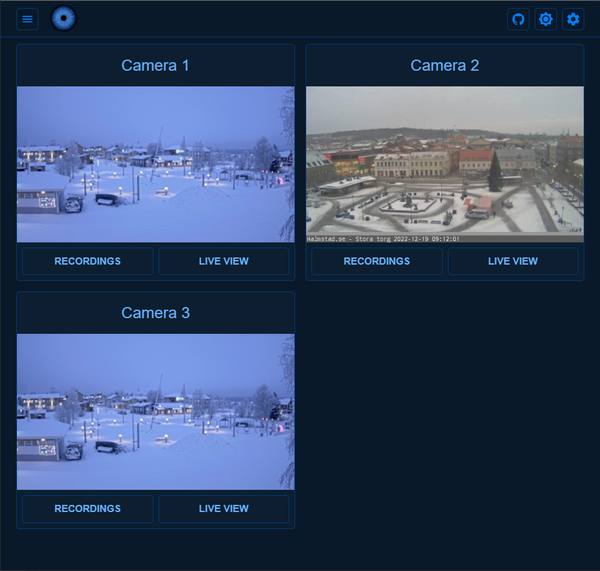
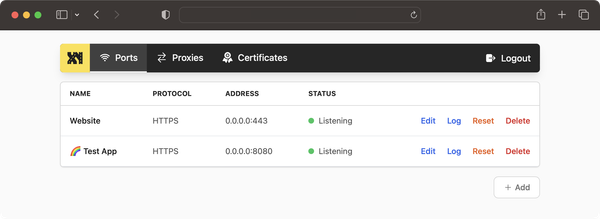
NVR stands for Network Video Recorder. Think of it as a super-smart digital video recorder for security cameras. But unlike those old-school systems that need a ton of cables, NVRs are all about working with cameras over your home or office network. Imagine you've got a bunch of