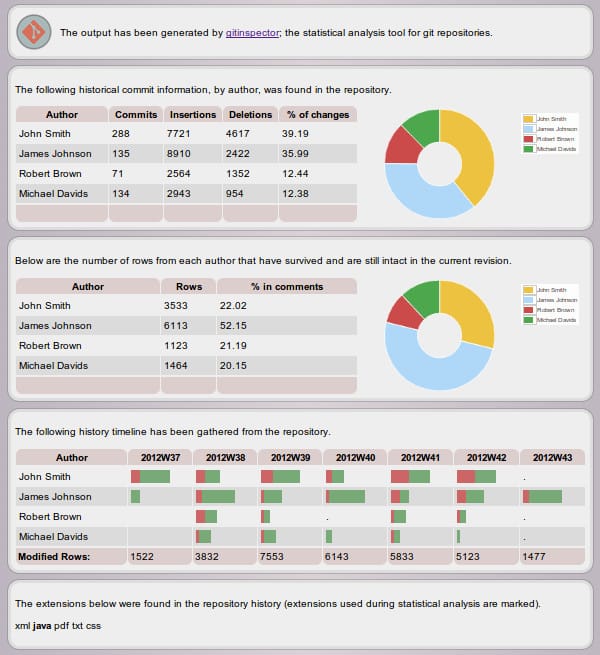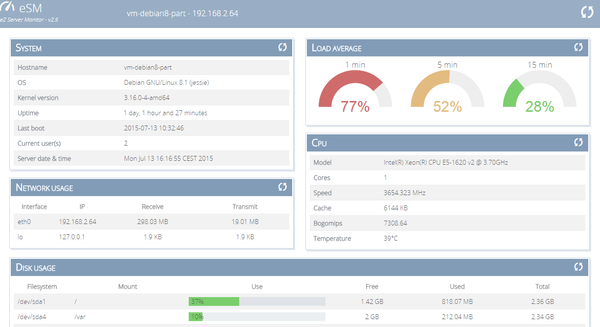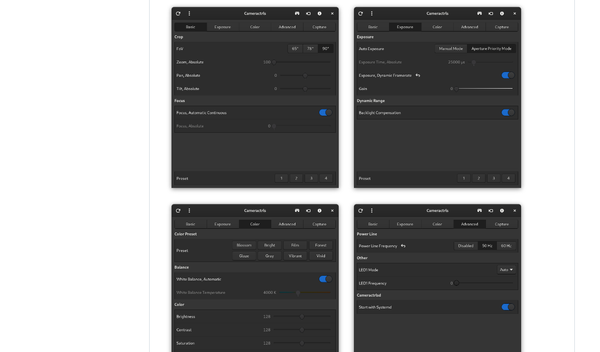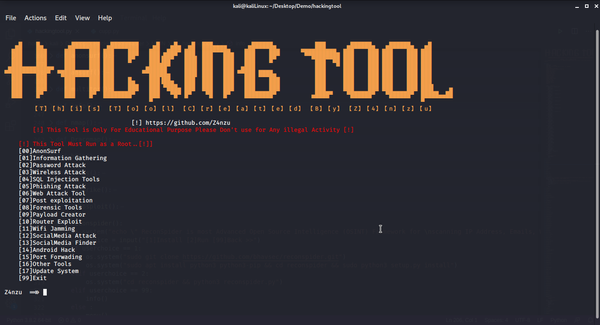
Developer Tools
8 Open-source Apps to Display and Control Android Devices From Your Desktop!
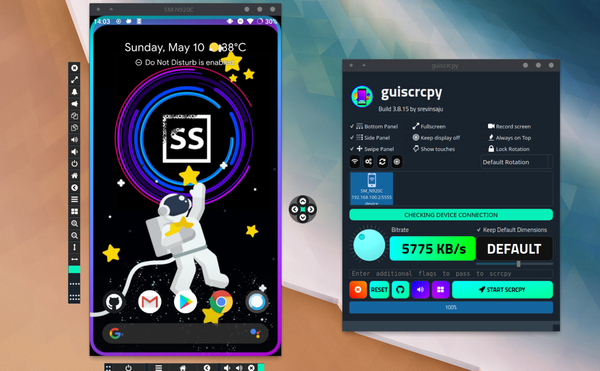
So, I recently had an interesting conversation with a good friend who's a game developer. He was telling me about how he uses his Android tablet for development and, to get the most out of it, controls it from his desktop. He even paid for a subscription to