Cybersecurity
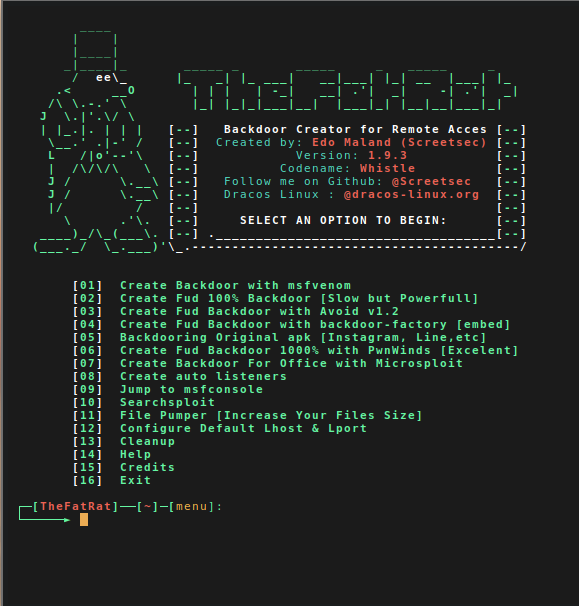
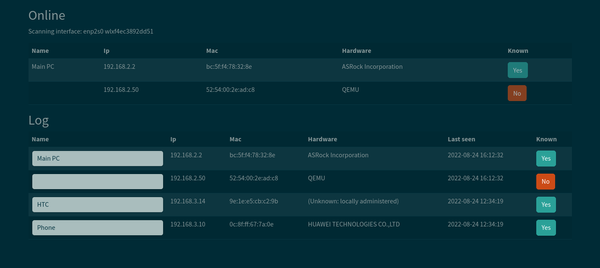
13 Network Vulnerability Scanners and Pentesting Tools for Pentesting, Test Your Wifi Network Now
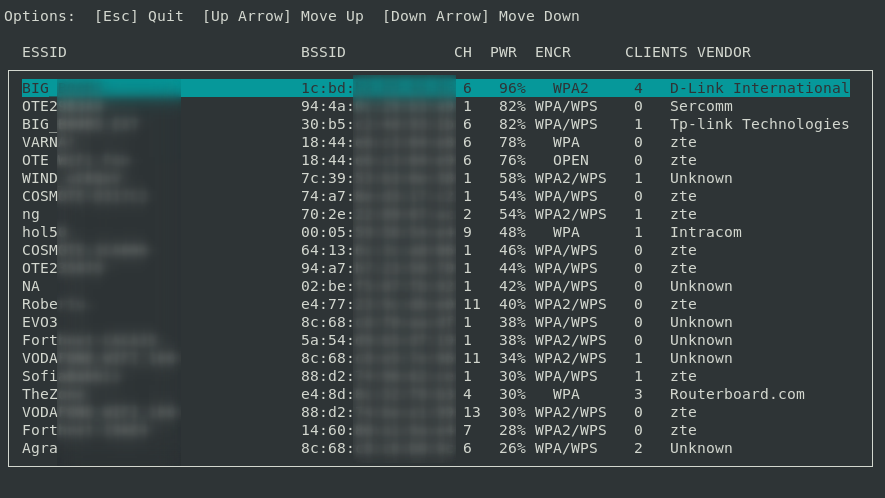
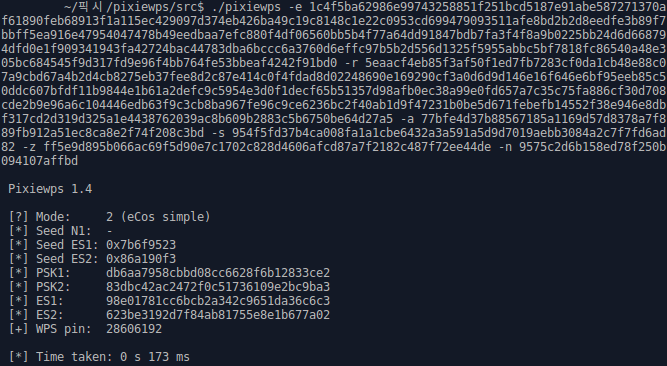
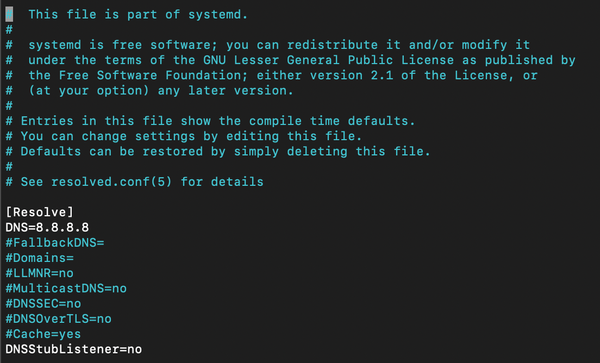
Pentesters, security researchers, and business owners must ensure the security of their Wi-Fi networks to protect sensitive data and prevent unauthorized access. Testing your network helps identify vulnerabilities that could be exploited by attackers, ensuring your system remains secure. The Importance of Regular Wi-Fi and Network Security Testing for Business