Vuls - An Open-source Fast Agentless Vulnerability Scanner for Linux/ FreeBSD Written with Go for Cybersecurity Experts and Pentesters
Table of Content
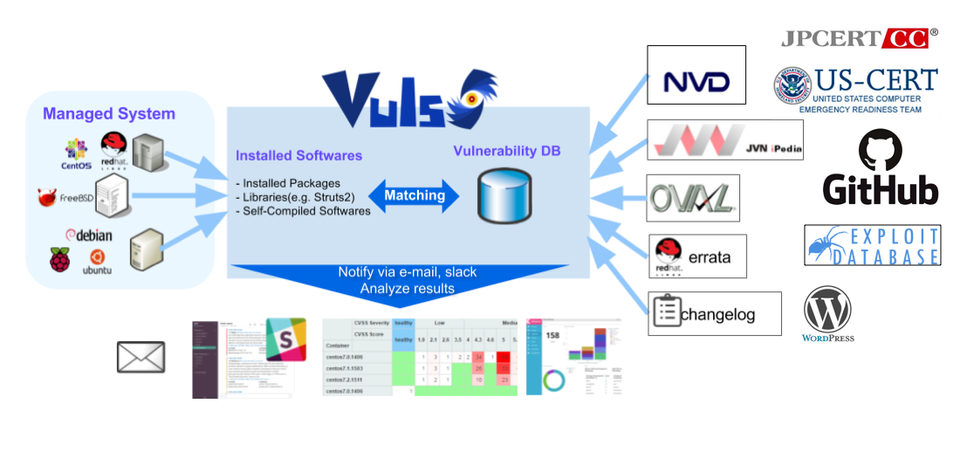
Vuls is an open-source, agentless vulnerability scanner designed to help administrators and security professionals, like pentesters, keep their systems secure. It’s written in Go, known for its lightweight and high-performance capabilities.
Vuls provides a proactive way to detect vulnerabilities without needing to install any agents on the target systems, simplifying the scanning process across multiple environments.
Scanning for WordPress
For WordPress security, you would need a specialized scanner that focuses on web applications and CMS platforms. Tools like WPScan or Wordfence are specifically tailored to identify vulnerabilities in WordPress, including outdated plugins, themes, and core files.
They also check for common security misconfigurations and known exploits related to WordPress installations.

As a pentester, Vuls offers the following benefits:
- Efficient Scanning: With its agent-less design, you can scan multiple servers quickly, without needing to install any intrusive software on the target machines.
- Automated Alerts: Automate the detection of new vulnerabilities with daily or weekly reports, ensuring you never miss critical security updates during ongoing audits.
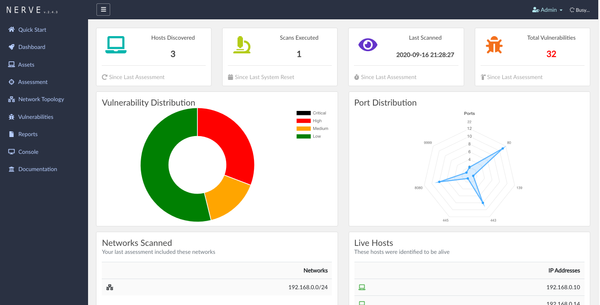
- Visualized Vulnerability Data: Use Vulsrepo to visualize which systems are most vulnerable, helping you prioritize remediation strategies during a pentest.
- Customizable Reports: Vuls reports can be customized and shared with clients to provide a detailed view of the vulnerabilities found during a security assessment.
Features
- Agent-less Scanning: No need to install any additional software on the target servers. You can run Vuls from a central management server.
- Automated Detection: Vuls continuously monitors and detects vulnerabilities relevant to your systems using CVE databases like NVD, JVN, and OVAL.
- Fast and Deep scan support
- Multi-platform Support: Vuls supports Linux and FreeBSD systems, making it suitable for a range of environments commonly used in enterprise settings.
- Detailed Reports: Vuls automatically generates vulnerability reports, which can be scheduled via CRON jobs, allowing for regular vulnerability monitoring.
- Integration with Slack: Vuls integrates with Slack (Twitter: @vuls_en) to provide alerts directly to your team, helping you stay on top of security updates.
- Vulsrepo for Visualization: Vulsrepo is an extension that allows users to visualize vulnerability data, making it easier to analyze and prioritize remediation efforts.
- Asciicast Support: View Vuls reports using an easy-to-read text-based interface with Asciicast, which can be beneficial for quick terminal-based reviews.
- Scan without root privilege, no dependencies
- Almost no load on the scan target server
- Offline mode scan with no internet access. (CentOS, Alma Linux, Rocky Linux, Debian, Oracle Linux, Red Hat, Fedora, and Ubuntu)
- Scan with root privilege
- Almost no load on the scan target server
- Detect processes affected by update using yum-ps (Amazon Linux, CentOS, Alma Linux, Rocky Linux, Oracle Linux, Fedora, and RedHat)
- Detect processes which updated before but not restarting yet using checkrestart of debian-goodies (Debian and Ubuntu)
- Offline mode scan with no internet access. (CentOS, Alma Linux, Rocky Linux, Debian, Oracle Linux, Red Hat, Fedora, and Ubuntu)
- First, start Vuls in server mode and listen as an HTTP server.
- Next, issue a command on the scan target server to collect software information. Then send the result to Vuls Server via HTTP. You receive the scan results as JSON format.
- No SSH needed, No Scanner needed. Only issuing Linux commands directory on the scan target server.
- Scan Vulnerabilities of non-OS packages
- Notification via Slack
- Detailed documentation
Supported Systems
- Alpine, Amazon Linux, CentOS, AlmaLinux, Rocky Linux, Debian, Oracle Linux, Raspbian, RHEL, openSUSE, openSUSE Leap, SUSE Enterprise Linux, Fedora, and Ubuntu
- FreeBSD
- Windows
- macOS
- Cloud, on-premise, Running Docker Container
License
GPL-3.0 License
Final Note
Vuls provides a comprehensive and efficient way for pentesters and system administrators to detect and manage vulnerabilities across Linux and FreeBSD environments. By automating the scanning process and delivering detailed reports, it eliminates the manual burden of constant monitoring and reduces the risk of oversight.
Whether you are managing a single server or an enterprise-level infrastructure, Vuls makes vulnerability scanning easier, more efficient, and more reliable.
Resources & Downloads