11 Essential Free Tools for Pentesting and Securing Your Docker and Kubernetes Containers
Table of Content
Is Your Docker Deployment Secure?
Docker containers have revolutionized the way applications are deployed and managed, but with great flexibility comes the need for heightened security vigilance. Regularly checking your Docker containers is crucial to ensure they are configured correctly and free from vulnerabilities.
Misconfiguration can expose your applications to security risks, data breaches, and unauthorized access, which can lead to severe repercussions for businesses, including financial loss and reputational damage.
Misconfigurations are common and can stem from several sources, including incorrect permission settings, outdated software dependencies, and improper network configurations.
For instance, in 2020, a misconfigured Docker container led to a significant data breach involving a major cloud provider, where sensitive information was exposed due to open access to unsecured containers.
A secure Docker install is essential for maintaining the integrity of your systems while conducting assessments.
This incident highlighted the importance of regularly auditing and configuring container settings to prevent unauthorized access and safeguard sensitive data.
Moreover, Docker containers can be vulnerable to known security threats if they are not regularly updated or monitored. Cybercriminals often exploit outdated containers, making it imperative to keep them secure.
For example, a widely publicized incident involved an attacker gaining access to a company’s network by exploiting a vulnerability in an outdated Docker image, resulting in a ransomware attack that crippled operations.

These scenarios serve as reminders that regular security assessments are essential in maintaining a robust security posture.

To ensure the security of your Docker deployment, here are several reasons to regularly check your containers:
- Identify Vulnerabilities: Regular scanning can help identify known vulnerabilities and misconfigurations in your images and containers.
- Ensure Compliance: Keeping your containers secure helps meet industry compliance standards and regulations.
- Mitigate Risks: Proactively addressing misconfigurations can prevent unauthorized access and potential breaches.
- Maintain Performance: Optimized and secure configurations can enhance the overall performance of your applications.
- Protect Sensitive Data: Ensuring containers are properly secured helps safeguard sensitive customer and business data from cyber threats.

In the following list, we compiled the best open-source tool that can help you test and check
1- grype
grype is a free vulnerability scanner for container images and filesystems. Easily install the binary to try it out. Works with Syft, the powerful SBOM (software bill of materials) tool for container images and filesystems.
Features
- Container Image Scanning: Scan container images and filesystems for vulnerabilities.
- OS Package Vulnerability Detection:
- Alpine
- Amazon Linux
- BusyBox
- CentOS
- CBL-Mariner
- Debian
- Distroless
- Oracle Linux
- Red Hat (RHEL)
- Ubuntu
- Wolfi
- Language-Specific Package Vulnerability Detection:
- Ruby (Gems)
- Java (JAR, WAR, EAR, JPI, HPI)
- JavaScript (NPM, Yarn)
- Python (Egg, Wheel, Poetry, requirements.txt/setup.py)
- Dotnet (deps.json)
- Golang (go.mod)
- PHP (Composer)
- Rust (Cargo)
- Multi-Format Support: Supports Docker, OCI, and Singularity image formats.
- OpenVEX Support: Filter and augment scanning results with OpenVEX.
2- Clair
Clair is an open-source container vulnerability analysis tool developed by CoreOS, designed to help users identify security issues in container images.
It works by examining container images and analyzing them against a database of known vulnerabilities. Clair provides detailed information on the vulnerabilities detected, including severity levels, allowing organizations to address security risks effectively.
Supported Systems and Images
Clair supports the extraction of contents and assignment of vulnerabilities from the following official base containers:
- Ubuntu
- Debian
- RHEL
- Suse
- Oracle
- Alpine
- AWS Linux
- VMWare Photon
- Python
How It Works
- Image Analysis: Clair scans container images for layers and analyzes their contents. Each layer is inspected for software packages and dependencies.
- Vulnerability Database: The tool references a vulnerability database, which is regularly updated with information about known security issues in various software packages.
- Data Comparison: Clair compares the packages found in the container images with the entries in the vulnerability database. If a match is found, it logs the associated vulnerabilities, including their severity levels.
- API Integration: Clair provides a RESTful API that allows users to integrate it into their CI/CD pipelines or other systems for automated scanning and reporting.
- Reports Generation: After the analysis, Clair generates detailed reports that outline the vulnerabilities detected, helping teams prioritize and remediate security risks in their container images.

3- DockerScan
This open-source free (old) yet usable tool allows pentersters, devOps and web developers to perform Docker security analysis & hacking easily.
How does DockerScan work?
- Docker Image Input: Users specify the Docker image they want to scan by providing the image name. DockerScan can work with both local images stored on the Docker host and images pulled from remote registries.
- Image Layer Extraction: Upon receiving the image, DockerScan extracts the various layers of the Docker image. Each image is composed of multiple layers, and DockerScan examines these layers to analyze the software packages they contain.
- Vulnerability Database: The tool references a vulnerability database, which is regularly updated with known vulnerabilities from sources such as the National Vulnerability Database (NVD) and other public vulnerability feeds. This database includes details about security issues and the affected software components.
- Package Inspection: DockerScan inspects the extracted layers for installed packages. It identifies the software dependencies and libraries present in the image.
- Vulnerability Matching: After identifying the installed packages, DockerScan compares them against the entries in the vulnerability database. If any matches are found, it logs these vulnerabilities, providing information on their severity and potential impact.
- Report Generation: DockerScan generates a detailed report outlining the vulnerabilities detected in the scanned image. This report includes information such as the package names, the severity of vulnerabilities (e.g., critical, high, medium, low), and suggested actions for remediation.
- Command-Line Interface: DockerScan is typically run through the command line, making it easy for developers and security teams to integrate it into their existing workflows, including CI/CD pipelines.
4- Harbor
Harbor is an open-source cloud-native registry that stores, signs, and scans container images. It enhances the security and efficiency of managing container images in a private or hybrid cloud environment.
Harbor integrates with popular container orchestration platforms like Kubernetes, providing a centralized solution for managing container images while ensuring compliance and security through featur2es like vulnerability scanning and access control.
Harbor's Features
- Multi-Tenancy: Supports multiple users and projects with role-based access control.
- Image Vulnerability Scanning: Automatically scans images for known vulnerabilities.
- Policy-Based Replication: Allows automatic replication of images between multiple registries.
- Access Control: Fine-grained access control to manage user permissions.
- Notary Integration: Supports signing and verification of images for added security.
- Web User Interface: User-friendly web interface for managing images and projects.
- RESTful API: Provides a robust API for integration with other tools and automation.
- Docker Registry API Compatibility: Fully compatible with Docker Registry API, allowing easy integration with existing tools.
- Audit Logs: Maintains logs of all user actions for compliance and auditing purposes.
- Chart Repository: Supports storing and managing Helm charts alongside container images.
- LDAP/AD Integration: Allows integration with existing LDAP or Active Directory for user authentication.
- Image Tagging: Supports tagging and versioning of images for better management.
- Harbor CLI: Command-line interface for easy interaction with the Harbor registry.
- Self-Hosted Deployment: Can be deployed on-premises or in a cloud environment for full control over data.

5- Trivy
Trivy is a an open-source security scanner that identifies vulnerabilities and misconfigurations across various targets. It scans container images, filesystems, Git repositories, virtual machine images, Kubernetes environments, and AWS resources.
Trivy auto-detects known vulnerabilities in operating system packages and software dependencies, identifies infrastructure as code (IaC) issues, uncovers sensitive information and secrets, and checks for software licenses.
It supports a wide range of programming languages, operating systems, and platforms.

6- BOtB
BOtB is an open-source container analysis and exploitation tool designed to be used by pentesters and security engineers while also being CI/CD friendly with common CI/CD technologies.
Features of BOtB
- Vulnerability Exploitation: Exploit common container vulnerabilities.
- Post-Exploitation Actions: Execute post-exploitation tasks.
- CI/CD Integration: Work with CI/CD technologies for container testing.
- Manual & Automated Operations: Support both modes of execution.
- Docker Daemon Breakout: Break out via exposed Docker daemons (docker.sock).
- CVE-2019-5736 Exploitation: Utilize specific vulnerabilities for breakout.
- Privileged Breakout: Break out from privileged containers using capabilities.
- Data Extraction: Extract sensitive data from Linux Kernel Keyrings.
- Kubernetes Secrets: Identify and use Kubernetes Service Account secrets.
- Metadata Service Identification: Recognize metadata service endpoints.
- Sensitive String Analysis: Analyze sensitive strings in environment variables.
- UNIX Domain Sockets: Identify UNIX domain sockets supporting HTTP.
- Host Binaries Hijacking: Hijack host binaries with custom payloads.
- CI/CD Mode Execution: Run in CI/CD mode, returning specific exit codes.
- S3 Data Pushing: Push data to S3 buckets.
- Non-blocking Exit Codes: Force exit code of 0 for non-blocking CI/CD.
- CLI & YAML Support: Use command-line or YAML configuration.
- Reverse DNS Lookup: Perform reverse DNS lookups.
7- Dagda
Dagda is an open-source static analysis tool designed to identify known vulnerabilities, malware, and other malicious threats in Docker images and containers. It imports vulnerability data from CVEs, Bugtraq IDs, and exploits into a MongoDB for efficient searching.
It analyzes the installed software, OS packages, and programming dependencies, Dagda checks for vulnerabilities.
Additionally, it utilizes ClamAV the popular open-source antivirus to detect trojans and viruses, supporting multiple Linux base images, including Red Hat, Debian, and Alpine.
8- Gorsair
Gorsair is a penetration testing tool designed to discover and remotely access vulnerable Docker APIs. By exploiting exposed Docker APIs, it allows attackers to execute commands on remote containers, posing a significant risk of unauthorized access and control over the entire system.
9- Cloud Container Attack Tool (CCAT ☁️🐈)
CCAT (Cloud Container Assessment Tool) is a versatile tool developed by Rhino Security Labs for assessing the security posture of cloud-native applications. Designed for security professionals, DevOps engineers, and penetration testers, CCAT automates the identification of misconfigurations and vulnerabilities in containerized environments.
It scans Kubernetes clusters and Docker containers to detect potential security risks, providing actionable insights to enhance cloud security.
By integrating CCAT into your security workflow, you can effectively safeguard your cloud infrastructure against emerging threats and ensure compliance with best practices.
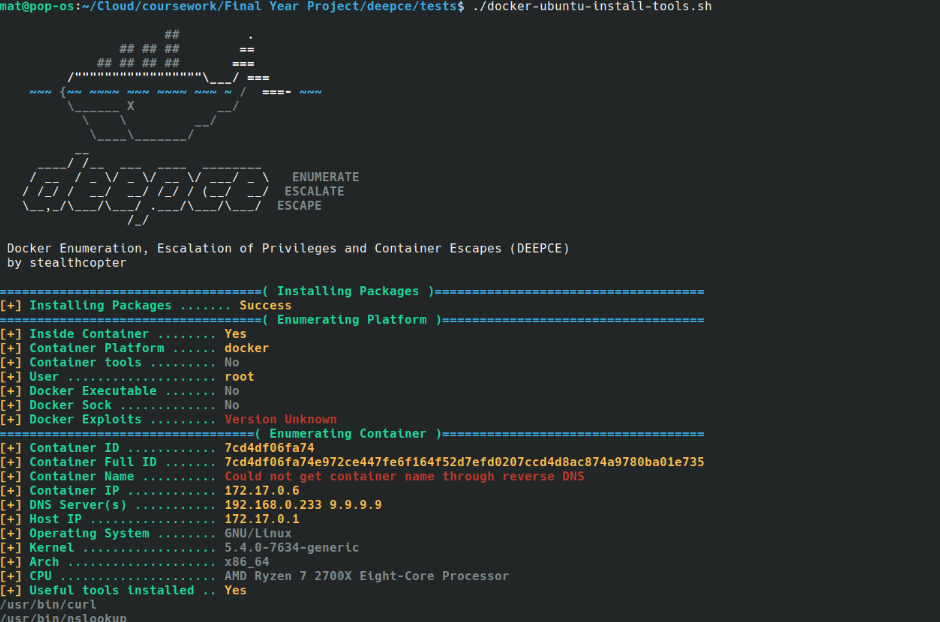
10- DeepCE
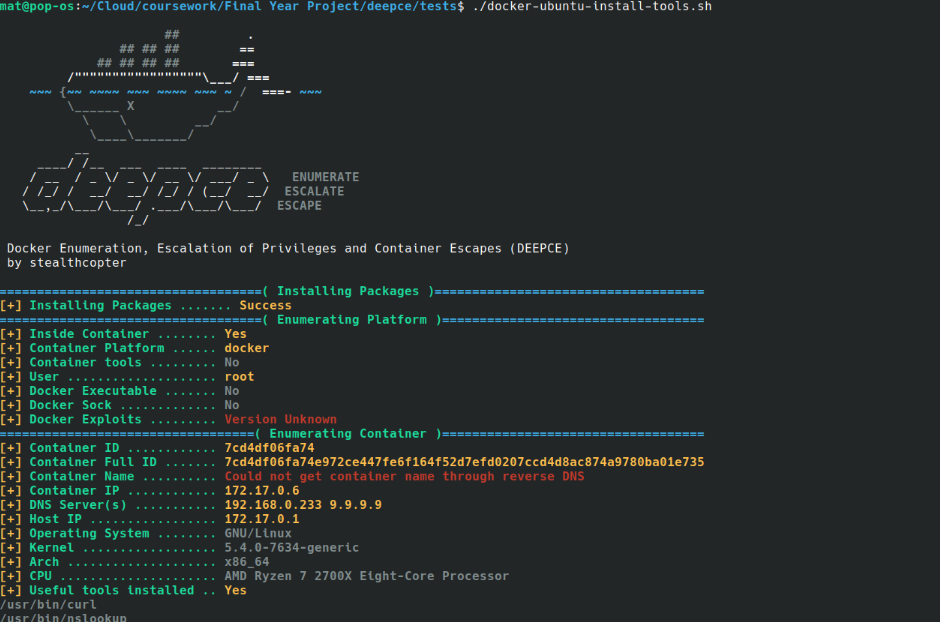
DeepCE is a security tool that conducts deep container image analysis to identify vulnerabilities and misconfigurations.
It provides insights into image layers, package vulnerabilities, and potential security risks, enhancing overall container security for developers and security professionals.
11- Docker Bench for Security
The Docker Bench for Security is a script that checks for dozens of common best-practices around deploying Docker containers in production.