BLUESPAWN: Shield Your Windows Network with Active Defense and Rapid Malware Elimination!
Table of Content
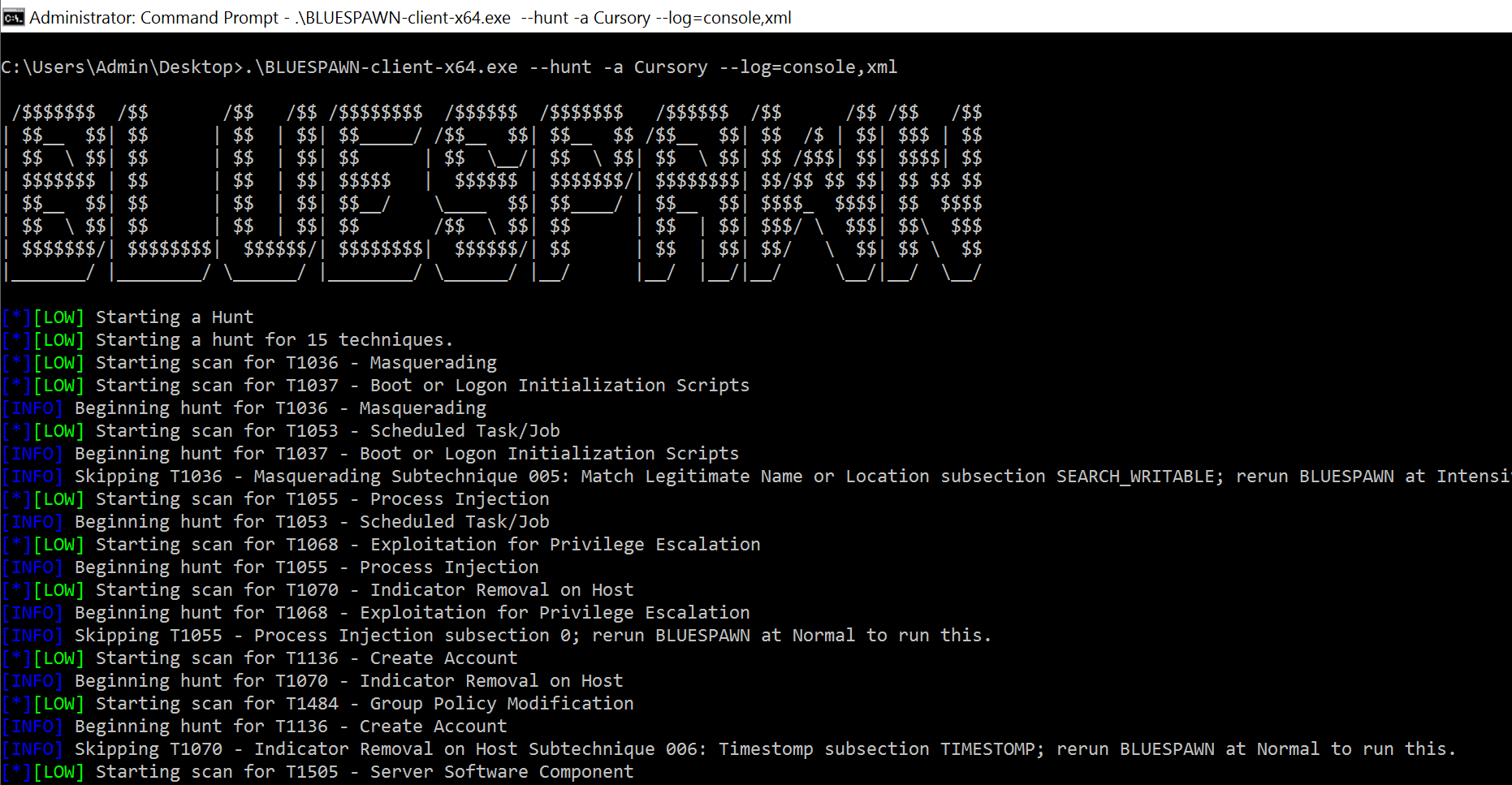
BLUESPAWN is an active defense, endpoint detection, and response tool designed for quick detection, identification, and elimination of malicious activity and malware across a network. The tool encourages user participation and contribution; suggestions for new features, bug reports, and development assistance are welcomed through their Discord server.
The creation and open-sourcing of BLUESPAWN were driven by several motivations. The developers aimed to create a tool that could rapidly identify malicious system activity, understand their detection coverage precisely, gain a better comprehension of the Windows attack surface, and contribute to the open-source Blue Team Software. BLUESPAWN also aims to demonstrate features of Operating System APIs by leveraging a wealth of resources like Microsoft Documentation and StackOverflow Answers, which may benefit other developers.
Modes
BLUESPAWN is composed of three primary modes. These modes, which include various submodules (some of which may not yet exist in the codebase) are at different stages of planning, research, and development. They are also supported by several other modules.
- Hunt: Searches for signs of malicious activity
- Mitigate: Applies security settings to reduce vulnerabilities
- Monitor: Constantly observes the system for potential malicious actions
- Scan: Evaluates items found during hunts to determine if they are suspicious or malware
- User: Includes the main program, IOBase, and other similar functions
- Util: Includes a set of modules that support the main operations such as Configurations, Event Logs, File System, Log, PEs, and Processes
Features
- Open-source
- Easy to use
- Fast
- Active defense and endpoint detection
- Real-time monitoring against active attackers
- Contains three primary modes: Hunt, Mitigate, Monitor
- Scan feature to evaluate items found during hunts
- User features including the main program and IOBase
- Util features for supporting main operations, such as Configurations, Event Logs, File System, Log, PEs, and Processes
License
The App is released under the GPL-3.0 License