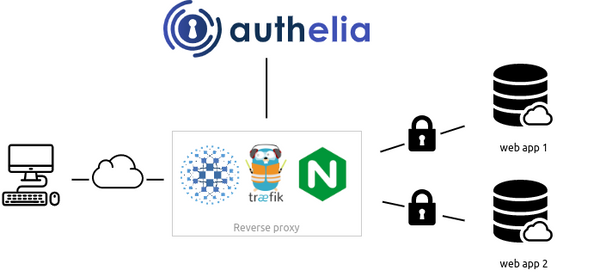
What are Identity and Access Management Solutions, and Why Do Companies Need them?
Table of Content
Identity and Access Management Solutions (IAM) have become increasingly important for businesses of all sizes as they help to manage user access to critical systems and applications while ensuring data security and compliance. In this blog post, we will explain what IAM is and why companies need it.
Understanding Identity and Access Management Solutions (IAM)
IAM refers to the set of processes, technologies, and policies that manage and secure user identities and their access to corporate resources such as networks, applications, and data. IAM solutions help organizations to manage the lifecycle of user identities from creation, provisioning, and maintenance to termination. IAM solutions also enforce access policies to ensure that only authorized users can access resources while preventing unauthorized access.
IAM technologies and protocols, such as Single Sign-On (SSO), Multi-Factor Authentication (MFA), Privileged Access Management (PAM), and Identity Governance and Administration (IGA), collaborate to provide a holistic solution for managing user identities and access to vital resources.
IAM Best Practices
To achieve optimal results, companies should follow best practices when implementing IAM solutions. These practices include:
- Implementing the principle of least privilege, which limits user access to only what they need to perform their job duties.
- Regularly reviewing and updating access permissions to ensure they remain appropriate.
- Enforcing strong password policies, including multifactor authentication.
- Regularly monitoring and auditing access activity to identify potential security threats or anomalies.
- Providing ongoing user training and education to raise awareness about the importance of security and the proper use of access.
- Regularly reviewing and updating IAM policies and procedures to ensure they remain up-to-date and effective.
IAM Benefits for Enterprise
IAM solutions provide numerous benefits to companies, including:
Improved security and compliance: IAM solutions aid in preventing unauthorized access to essential resources, mitigating the risk of data breaches, and ensuring adherence to regulatory mandates like GDPR and HIPAA.
Enhanced productivity and efficiency: IAM solutions help to automate user provisioning, access requests, and password resets, saving time and reducing the risk of errors. This also helps to improve employee productivity.
Simplified access management processes: IAM solutions help to simplify access management processes by centralizing user access to critical resources. This eliminates the need for multiple passwords and logins, reducing user frustration and increasing efficiency.
Reduced IT costs and risks: IAM solutions help to reduce IT costs and risks by automating user provisioning and access management. This also reduces the risk of insider threats and data breaches, saving companies from costly legal and reputational damage.
IAM Challenges and Considerations
IAM solutions face challenges and considerations that companies need to address. These include,
- Implementation difficulties,
- Integration with existing systems,
- User adoption and training,
- Data privacy and regulatory compliance,
- Maintenance and updates.
By addressing these issues through proper planning, training, and ongoing maintenance, companies can achieve significant benefits from implementing IAM solutions.
Types of IAM Solutions
There are three main types of IAM solutions:
- On-premise IAM: These solutions are installed and run on a company's own servers and infrastructure. They offer high levels of control and customization, but can be expensive and require dedicated IT resources.
- Cloud-based IAM: These solutions are hosted and managed by a third-party provider in the cloud. They offer lower upfront costs and scalability, but may be less customizable and require a high level of trust in the provider's security.
- Hybrid IAM: These solutions combine elements of both on-premise and cloud-based IAM, allowing for greater flexibility and customization while also taking advantage of the benefits of cloud-based solutions.
How to Choose the Right IAM Solution for Your Business
Choosing the right IAM solution for your business requires considering several factors:
- Security: Ensure the solution has robust security features that meet your business requirements.
- Scalability: Choose a solution that can accommodate your current and future needs as your business grows.
- Integration: Select a solution that can integrate with your existing systems and infrastructure.
- Ease of Use: Look for a solution that is user-friendly and easy to manage for your IT team and end-users.
- Cost: Determine the total cost of ownership, including upfront and ongoing costs.
- Support and Maintenance: Ensure the provider offers reliable support and maintenance services to keep the system up-to-date and secure.
By evaluating these factors, businesses can select an IAM solution that best meets their needs and provides the greatest benefits for their organization.
Conclusion
In conclusion, IAM solutions are critical for businesses to manage access securely, providing increased security, improved productivity, and better compliance with regulations. While there are challenges and considerations, by choosing the right solution and addressing these factors, businesses can reap the benefits of IAM while minimizing risks and ensuring business continuity.