Linux
22 System Monitor Apps and Device Information Scanners for Linux Systems
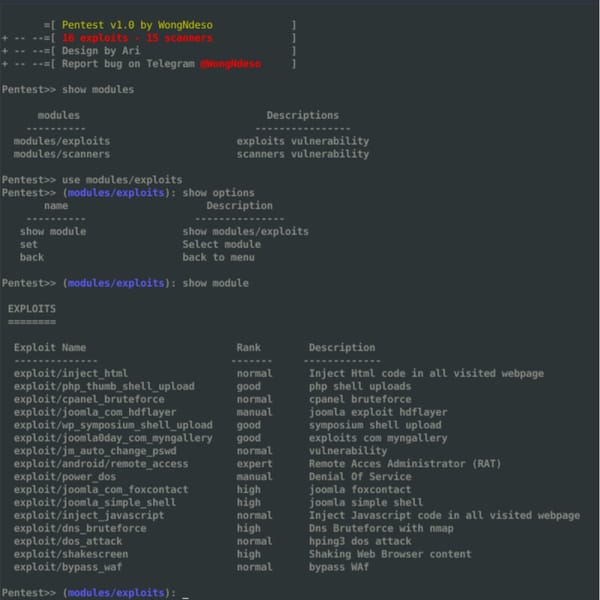
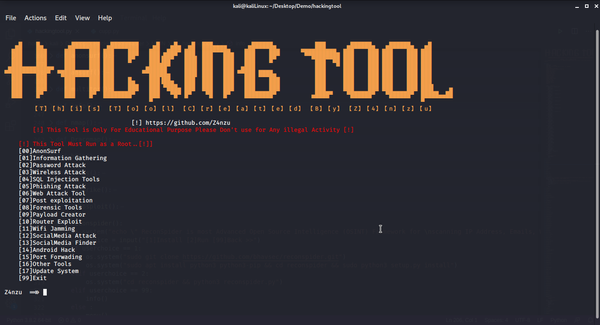
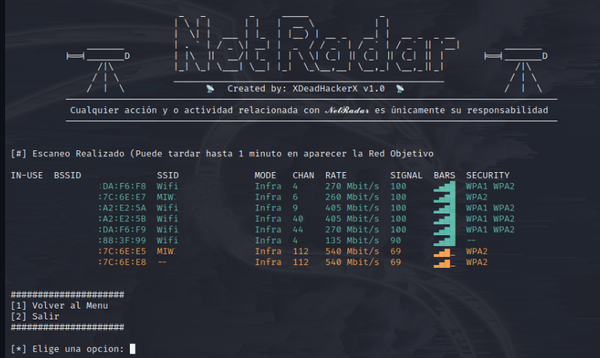
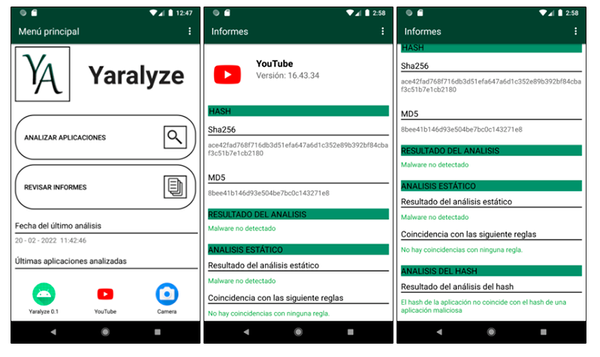
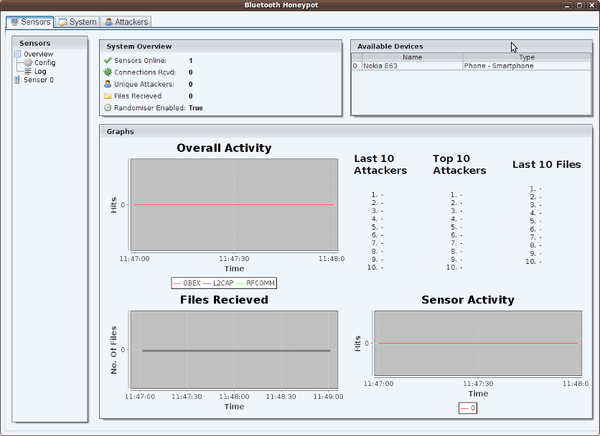
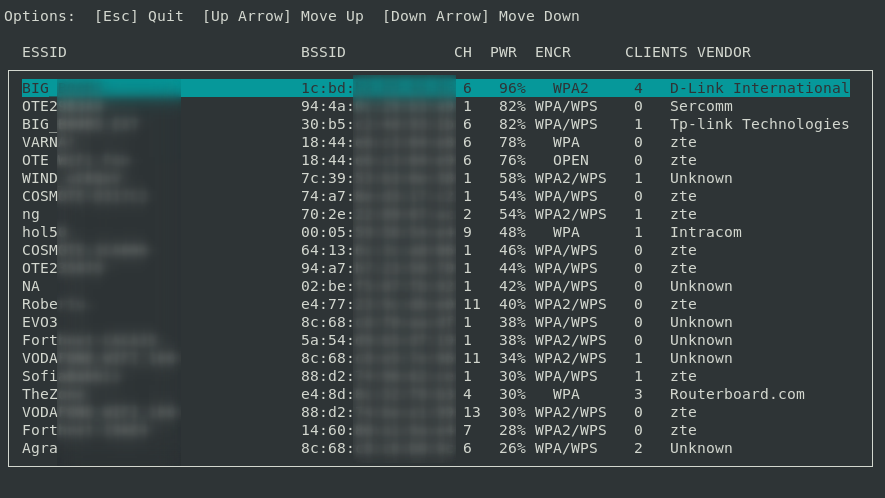
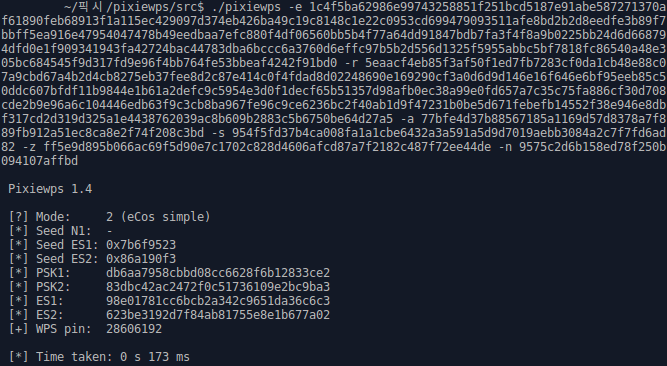
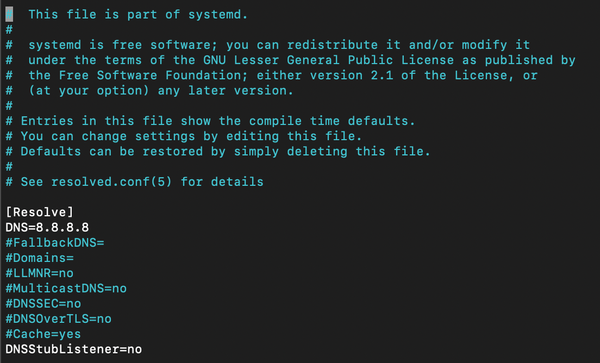
System monitors are essential tools for tracking system performance and resource usage in real time. They provide insights into CPU, memory, disk, and network activity, helping users manage both personal and server environments effectively. This is crucial for optimizing performance, troubleshooting issues, and ensuring the smooth operation of applications. Many