Cybersecurity
2025's Top Open-Source IAM Picks: Secure Your Business Today - 12 Alternatives
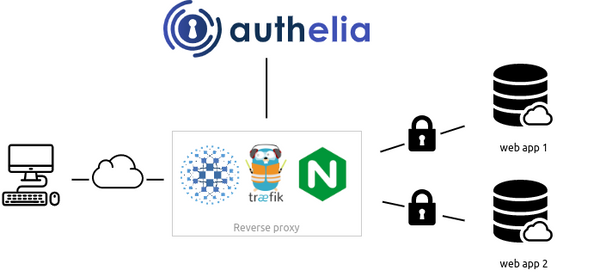
Let’s be real—managing who can access what in a company isn’t just a chore; it’s a ticking time bomb if not handled properly. One wrong click, one unauthorized login, and suddenly you’re in a cybersecurity nightmare with legal consequences knocking at your door. Enter Identity