
Cybersecurity
The Dark Side of Smart Cars: Why I Don't Trust Them (Yet)
Cybersecurity Pentesting and Smart Cars: The Growing Need for Secure Autonomous Vehicles

Cybersecurity
Cybersecurity Pentesting and Smart Cars: The Growing Need for Secure Autonomous Vehicles

pentesting
Unveiling the Power of Code Analysis in Penetration Testing Cracking the Code: Static vs. Dynamic Analysis for Aspiring Security Pros
privacy
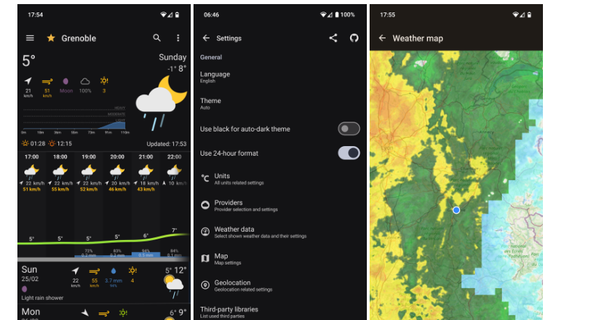
As I came from a vast valley (Egypt) where everything is clear, especially the weather. Sometimes, there is some mist in the morning, but it never lasts. It takes about a minute of looking at the sky to predict the weather for most of the day. That’s not the
Python
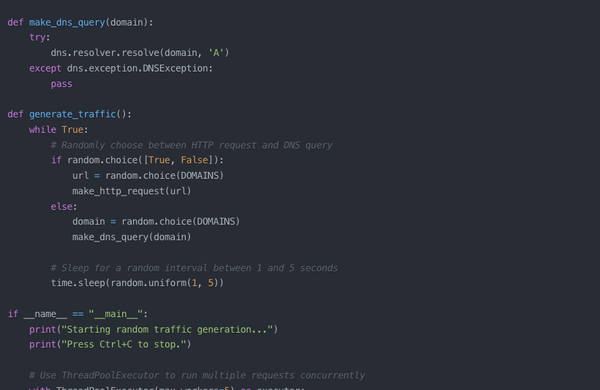
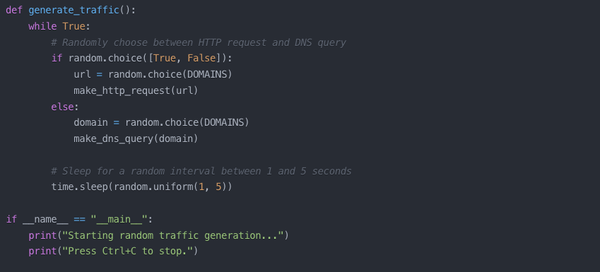
Web traffic obfuscation is a privacy-enhancing technique that involves generating random internet traffic to mask a user's actual browsing patterns. This approach is based on the principle of introducing "noise" into one's digital footprint, making it more challenging for third parties to accurately profile
Python
Enhance Privacy: Generate Random HTTP/DNS Traffic Noise with Python
CCTV
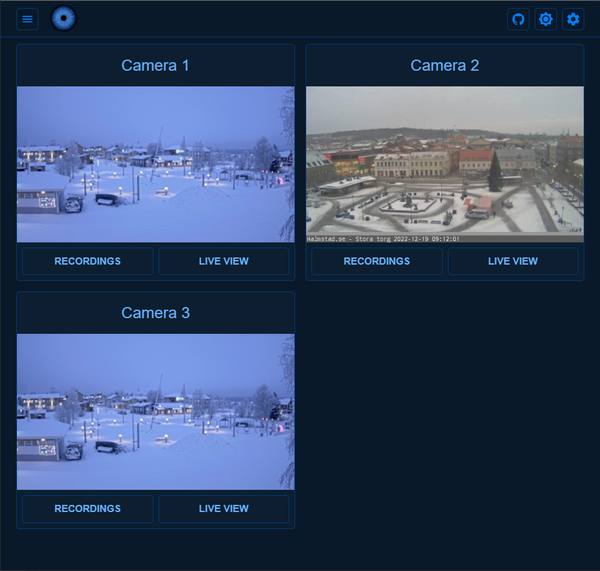
Viseron is an open-source self-hosted CCTV and local-first NVR solution with AI-powered computer vision support. It comes with amazing powerful features as Object detection, motion detection, face recognition, image classification, and supports hardware acceleration. Key features * Object Detection: YOLOv3/v4/v7 (OpenCV), Tensorflow (Google Coral EdgeTPU), CodeProject.AI * Motion Detection
privacy
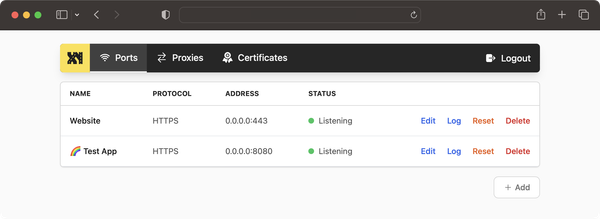
Imagine you're at a fancy restaurant. You don't talk directly to the chefs in the kitchen, right? Instead, there's a waiter who takes your order, delivers it to the kitchen, and brings back your food. That waiter is like a reverse proxy in the
Linux
Hey there, tech rebels and budget-conscious educators! Ever feel like your computer's running slower than a sloth on sedatives? Or maybe you're just tired of Big Tech breathing down your neck every time you open a browser? Well, buckle up, buttercup, because I'm about

Networks
A Network Management and Monitoring System is a set of tools and processes designed to oversee, control, and optimize network resources and services. It helps administrators monitor network performance, detect issues, and manage network resources effectively. This tool is essential for organizations looking to enhance performance, security, and efficiency in

dns
DNSCrypt is a protocol that encrypts, authenticates and optionally anonymizes communications between a DNS client and a DNS resolver. It prevents DNS spoofing. It uses cryptographic signatures to verify that responses originate from the chosen DNS resolver and haven’t been tampered with. It is an open specification, with free

Cybersecurity
Nginx is a popular open-source server that runs most of the websites, web apps and services on the internet nowadays. However, bad configuration can leave your website vulnerable to hackers. Some may use some Nginx dashboards and UI tools for better and easier system configuration, you may read about them
Android
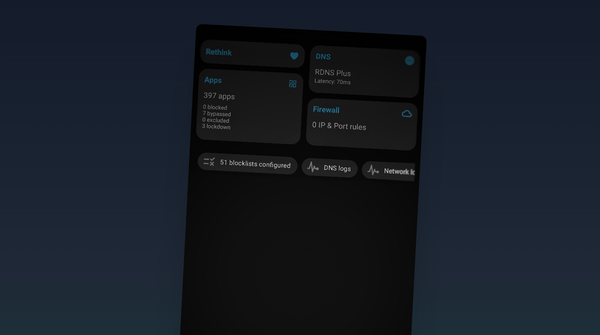
Block malware, spyware, ads, and trackers across all apps with Rethink DNS. Servers in 300+ locations: Experience Blazing fast speeds.

Open Source Intelligence (OSINT)
SpiderFoot is an open source intelligence (OSINT) automation tool. It integrates with just about every data source available and utilises a range of methods for data analysis, making that data easy to navigate. SpiderFoot has an embedded web-server for providing a clean and intuitive web-based interface but can also be

macos
A firewall app monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between trusted and untrusted networks, blocking unauthorized access while allowing legitimate communication, thereby enhancing the overall security of devices and networks. Do you need a firewall on macOS? what
Docker
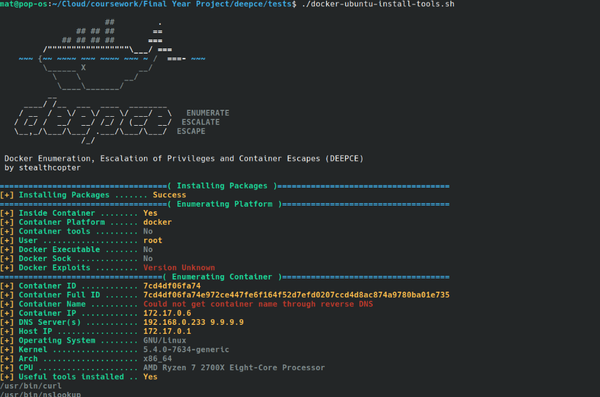
Is Your Docker Deployment Secure? Docker containers have revolutionized the way applications are deployed and managed, but with great flexibility comes the need for heightened security vigilance. Regularly checking your Docker containers is crucial to ensure they are configured correctly and free from vulnerabilities. Misconfiguration can expose your applications to

Cybersecurity
HuntKit is a collection of [penetration testing, bug bounty hunting, capture the flag, red teaming] tools in a single Docker image. Simply run the image and start using the tools. Its modular architecture allows users to customize their workflows and leverage a range of hunting techniques, enhancing the efficiency of

Android
With over 11 million Android devices affected by malware, protecting your device is more important than ever. Android’s open nature makes it a popular target for cybercriminals who exploit vulnerabilities to access your data, steal personal information, or install malicious software. A reliable malware scanner can help detect and
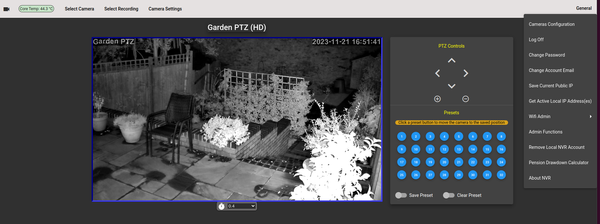
CCTV
This open-source project allows you to run a complete multi-CCTV system on your Linux, Raspberry Pi, Windows or macOS systems without any fee. Designed in Java, it runs on any Java-enabled system, ensuring broad compatibility. It supports multiple admins, many cameras, recording as it comes with a built-in NVR and
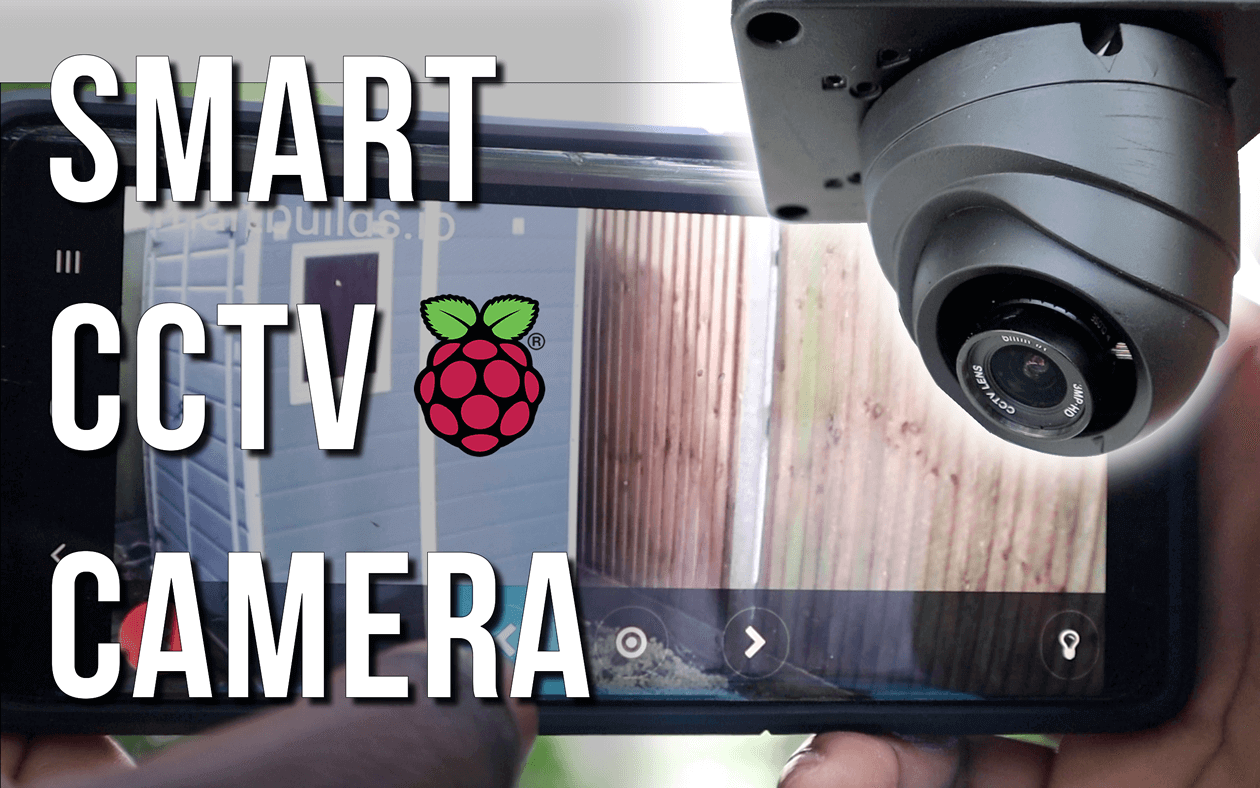
CCTV
Build your own home Raspberry Pi-powered surveillance IoT camera with Face recognition, access your live feed from any device

Cybersecurity
WhatWeb is a web technology identification and scanner tool that answers the question, "What is that Website?" It recognizes over 1800 web technologies, including CMS, analytics packages, and JavaScript libraries. WhatWeb operates with adjustable aggression levels, allowing users to balance speed and reliability. The default 'stealthy'
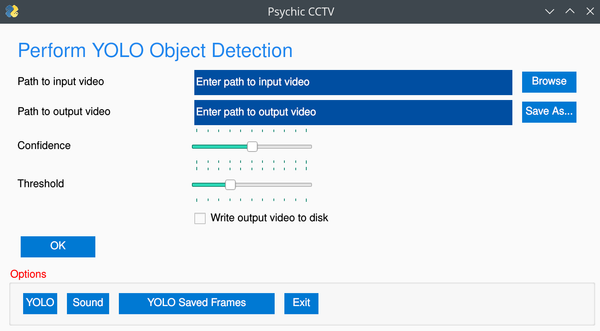
Cybersecurity
CCTV video analysis tool built completely in python.
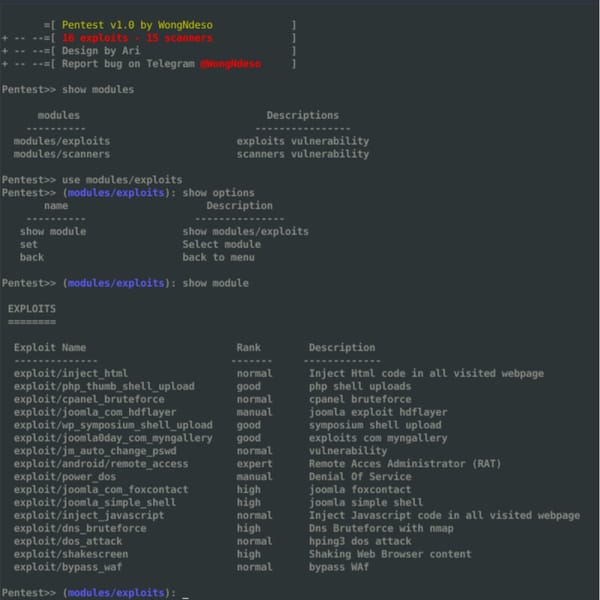
Vulnerability Scanner
Pentest Tools Framework is a database of exploits, Scanners and tools for penetration testing. Pentest is a powerful framework includes a lot of tools for beginners. You can explore kernel vulnerabilities, network vulnerabilities It is written in Python and uses some Perl, Ruby and PHP scripts. It includes a variety
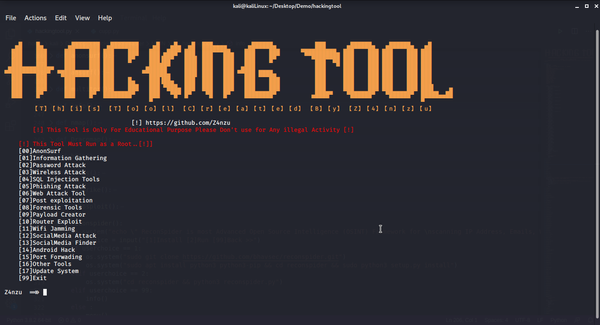
Vulnerability Scanner
HackingTool is one of the most popular pentesting and hacking toolkits available, widely used by hackers, pentesters, and security experts. It offers a vast range of essential tools, all bundled into one accessible interface. HackingTool is popular among security experts due to its all-in-one design, streamlining the entire pentesting process
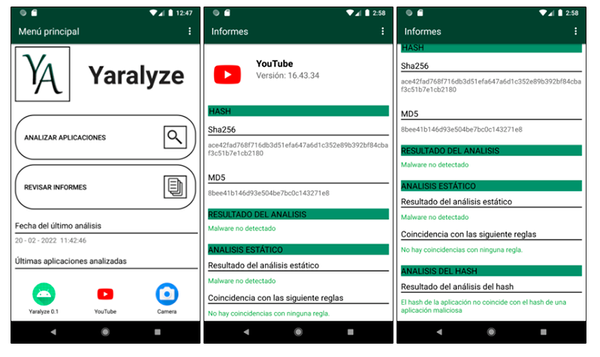
Android
Yaralyze is an malware detection tool for Android that relies on two types of static analysis, Yara rule analysis and hashes analysis.